Sodinokibi drops greatest hits collection, and crime is the secret ingredient
When a group of celebrities ask to speak with their lawyer, they usually don’t have to call in a bunch of other people to go speak with their lawyer. However, in this case it may well be a thing a little down the line. A huge array of musicians including Bruce Springsteen, Lady Gaga, Madonna, Run DMC and many more have had documents galore pilfered by the Sodinokibi gang.
Around 756GB of files including touring details, music rights, and correspondence were stolen – some of which was sitting pretty on a site accessible through TOR as proof of the sticky-fingered shenanigans. The law firm affected is Grubman Shire Meiselas & Sacks, a major player handling huge contacts for global megastars on a daily basis. Although they handle TV stars, actors, and sports personalities and more, so far the only data referenced online appears to be in relation to singers / songwriters.
Why?
The assumption is the data is being displayed as a preview of things to come; pay a ransom, or the data gets it (and by gets it, we mean “everything is published online in disastrous fashion”). The Sodinobiki gang are not to be trifled with, having already brought the walls crashing down upon Travelex not so long ago.
Hot targets…
Legal firms are becoming a hot target for malware focused criminals as they realise the value of the data they’re sitting on. Break in, exfiltrate the files, then send a few ransom notes to show them you A) have the files and B) mean business. If they refuse to pay up, drop the files and walk away from the inevitable carnage of reputational damage + compromised clients.
Who or what is Sodinokibi?
Put simply, a devastatingly successful criminal group with a penchant for Ransomware, data theft, and extortion. Sporting a popular Ransomware as a Service business model, they spiked hard in May of 2019 with a ramp-up in attacks on business and (to some degree) consumers. Their ransomware went a long way to filling the void left by GandCrab group’s “retirement,” and multiple, smaller spikes took place until an eventual decline for both consumer and business towards the end of July.
There were six versions of Sodinokibi released into the wild between April to July alone, helping to keep the security industry and targets on their toes over a very condensed period. Vulnerabilities, phishing campaigns using malicious links, malvertising, and even compromised MSPs to help launch the ransomware waves. You should absolutely lock down your MSP, by the way.
Technical details on the attack?
This is a breaking story and for various reasons the affected parties aren’t going to spill the beans just yet, especially with investigations ongoing. Having said that, there’s every probability they used ransomware to get the job done and that this was a targeted attack. How is Sodinokibi ransomware faring at the moment?
Sodinokibi ransomware statistics
This likely isn’t part of any huge spam wave. Our monthly data for consumer and business shows the last big spike in Ransom.Sodinokibi back in December:
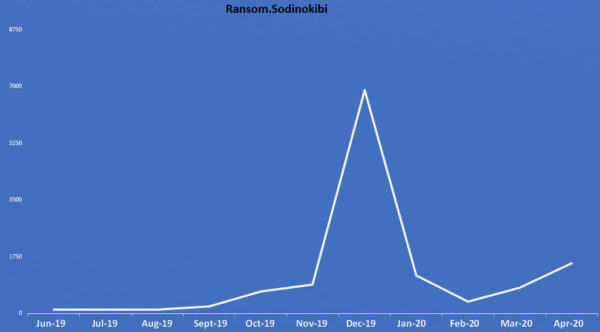
Business detections hovered between 200 to 280 from September to November 2019, before exploding over December to just under 7,000. It quickly dropped back down to 260 in February 2020, with a slight spike of 1,447 in April.
Consumer, meanwhile, followed a slightly more convoluted path with a peak of just over 600 in November 2019, and numbers ranging from 293 in July 2019 to 228 in March 2020 and generally low numbers elsewhere (76 in August 2019, 70 in December 2019, and 109 in April 2020).
In conclusion, then, ensure your ransomware armory is fully stocked and ready to go should you be sitting on lots of incredibly valuable entertainer documents, or indeed anything at all. Whether hit by random attacks or targeted mayhem, the end result is still the same: lots of headaches, and quite a few calls to legal.
Or, in this case, many calls to legal.
The post Sodinokibi drops greatest hits collection, and crime is the secret ingredient appeared first on Malwarebytes Labs.


![[DRAGONFORCE] - Ransomware Victim: Pratt Homes 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)