Spelevo exploit kit debuts new social engineering trick
2019 has been a busy year for exploit kits, despite the fact that they haven’t been considered a potent threat vector for years, especially on the consumer side. This time, we discovered the Spelevo exploit kit with its virtual pants down, attempting to capitalize on the popularity of adult websites to compromise more devices.
The current Chromium-dominated browser market share favors social engineering attacks and other threats that do not require the use of exploits in order to infect users. However, we continue to see malvertising campaigns pushing drive-by downloads in our telemetry. The malicious adverts are placed on tier 2 adult websites that still drive a lot of traffic.
Recently, we captured an unusual change with the Spelevo exploit kit where, after an attempt to trigger vulnerabilities in Internet Explorer and Flash Player, users were immediately redirected to a decoy adult site.
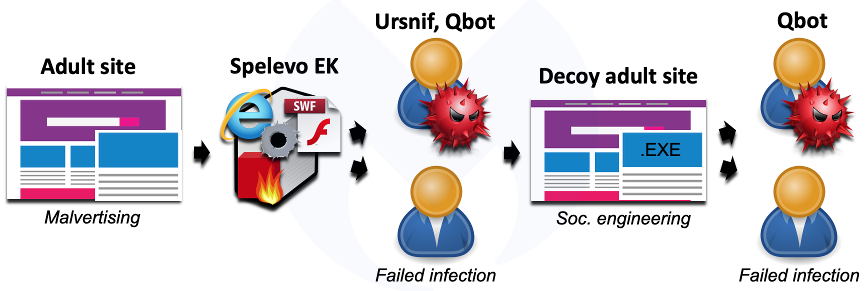
Spelevo EK instructs the browser to load this site, which social engineers victims into installing a video codec in order to play a movie. This appears to be an effort from the Spelevo EK operator to double his chances of compromising new machines.
Spelevo EK changes its redirection URL
Based on our telemetry, there are a few campaigns run by threat actors converting traffic to adult sites into malware loads. In one campaign, we saw a malvertising attack on a site that draws close to 50 million visitors a month.
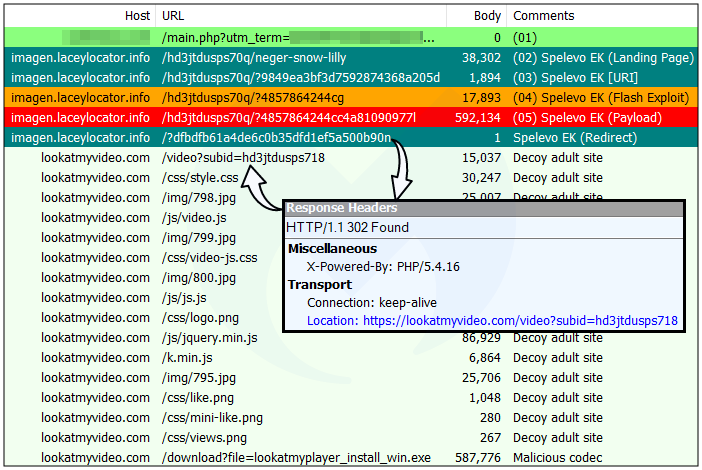
We collected two main payloads coming directly from Spelevo EK:
- Ursnif/Gozi
- Qbot/Qakbot
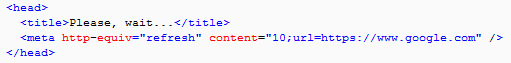
One thing that Spelevo EK did which was a little bit different from other exploit kits is redirect victims to google.com post exploitation, typically after a 10-second delay:
However, in this latest capture, we noticed that the script had been edited and that the time was increased to 60 seconds:
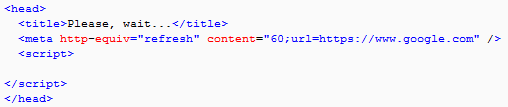
This change is important because it allows enough time for the exploit kit to run all the way and call the last URL part of the EK framework. Here, we noticed something new as well.
Previously, the URL immediately following the payload had the following ending pattern: &00000111&11. Now, the new pattern is 32 characters followed by the letter ‘n’.
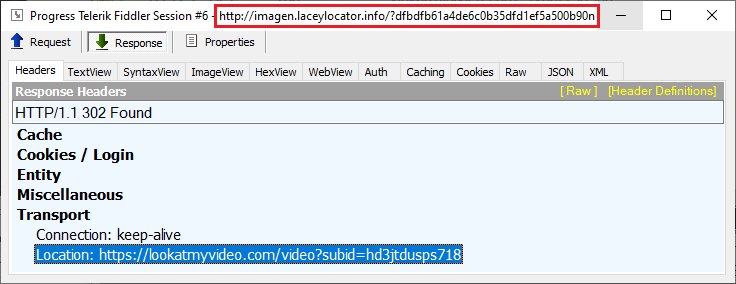
Before the refresh tag comes into effect, the browser is redirected to a new location, which happens to be a decoy adult site.
Social engineering as backup
There is nothing special about this fake adult site, but it works really well in the context of the malvertising chain. Victims were already engaged with the content and may not even realize that an exploitation attempt just happened.
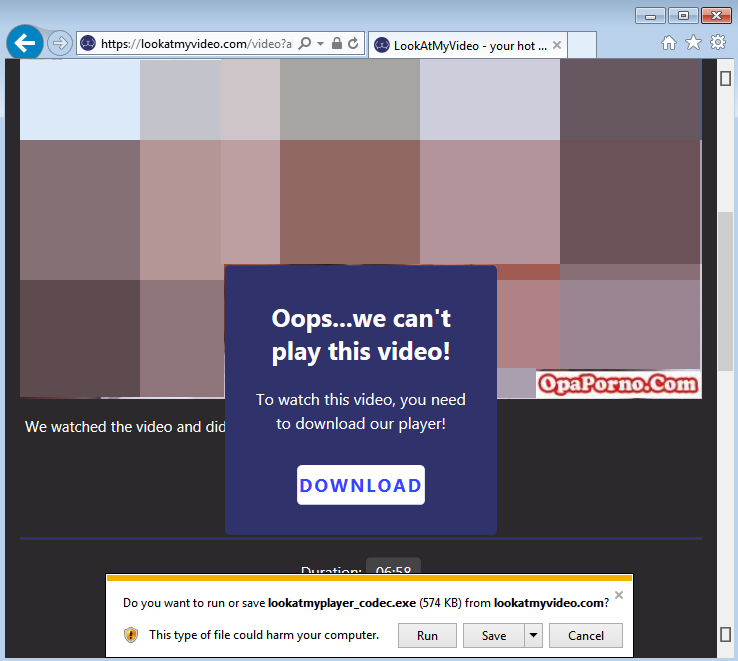
This time around, the site urges users to download a file called lookatmyplayer_codec.exe. Downloading video codecs to view media used to be fairly common back in the day, but isn’t really the case anymore. Yet, this kind of trick still works quite well and is an alternative method to compromise users.
The fake codec turns out to be Qbot/Qakbot, which is also one of the payloads distributed by Spelevo EK. In other words, the threat actor has two chances to infect victims: either via the exploit kit or fake codec.
This is not the first time that exploit kit operators have included social engineering schemes. In 2017, Magnitude EK was seen pushing a fake Windows Defender notification, while Disdain EK was tricking users with a fake Flash Player update.
Malwarebytes users are protected against both the exploit kit and payloads.
Indicators of compromise (IOCs)
Ursnif/Gozi
7212b70a0cdb4607f577e627211052e37ef01036e9231d9e286fc5e40974fd42
Qbot/Qakbot
1814deb94c42647f946b271fe9fc2baa6adae71df2b84f4854d36eda69979f93
1bbde8cee82550d4d57e4d6ee8faa9cbcbc6bdabf5873e494c47a1eb671fb7b5
Decoy adult site
lookatmyvideo[.]com
185.251.38[.]70
The post Spelevo exploit kit debuts new social engineering trick appeared first on Malwarebytes Labs.

