SSJ – Your Everyday Linux Distribution Gone Super Saiyan
SSJ is s silly little script that relies on docker installed on your everyday Linux distribution (Ubuntu, Debian, etc.) and magically arms it with hundreds of penetration testing and forensics tools. All of these run with almost native performance (as containers utilize the host kernel) and thus is a slightly better alternative to Virtual Machines in terms of speed, performance and convenience.
Technical Details
SSJ is a Docker image that uses kalilinux/kali as the base image and installs google-chrome, firefox-esr, sublime-text, tmux, kali-linux-large, etc. packages. It uses the kali.download/kali mirror and kali-last-snapshot branch. It also allows you to run GUI applications like Burpsuite, Wireshark, Ettercap, etc. from within the container on your everyday Linux distribution using --privileged docker capabilities and --net=host argument. This script builds the image and creates a .desktop file (the Application Launcher) for you. So, the only thing you need to do is, find SSJ in you aplicaiton drawer/menu and click on it to launch it. An xfce4-terminal will popup with all your pentesting and infosec tools in it. Execute burpsuite to fire up the proxy, firefox to fire up the browser and like that, you have access to hundreds of tools and packages that are there in Kali Linux (particularly the kali-linux-large metapackage), right on your everyday Linux distribution.
This script is just an extension to demon-docker. SSJ goes a few steps ahead to make the setup super easy and convenient for you.
Requirements
- Docker (User must be in the
dockergroup) - Internet connection
Installation
wget https://raw.githubusercontent.com/thirdbyte/ssj/main/ssj.sh && chmod +x ssj.sh && sudo ./ssj.sh
This might take half an hour to full depending upon your Internet speed. The script needs to download 3-4G of data.
Usage
- Access the application drawer/menu on your Linux distribution to find SSJ.
- Launch SSJ.
- An
xfce4-terminal1will pop up. - Use this terminal to launch any tool by executing them using their respective package names. For an example:
msfconsole,burpsuite,chromium,wireshark, etc. - You can save any file in the
/rootdirectory inside the container and find it at/home/ssjon your host Linux distribution.
Screenshots
Tested on: Ubuntu 20.04.1 LTS

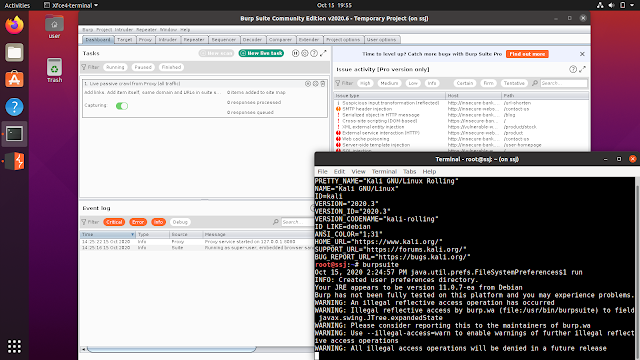
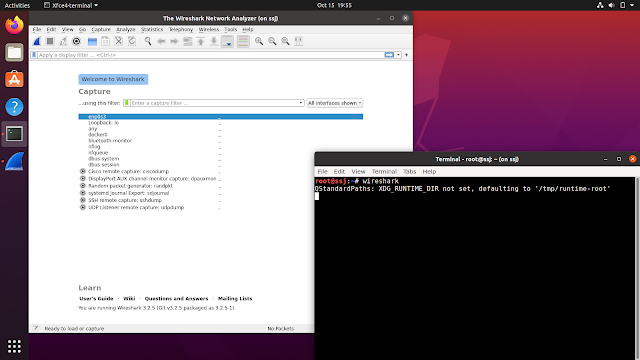
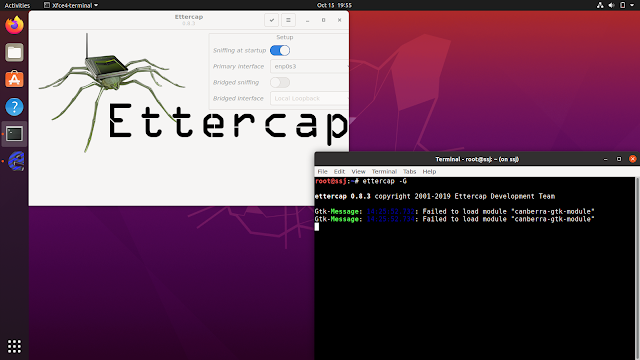
Troubleshooting
- The Kali Linux repositories are updated very frequently. Sometimes, when the packages are being migrated to the
/kalirepository, you might get a404error finding some packages while the image is building. The only way to resolve this as of now is to wait a few hours and try again.
Limitations
- Wireless hacking tools that require a patched kernel, the one that is found in Kali Linux, will not work on SSJ. The simple reason for that is SSJ utilizes the Linux kernel of your host machine which isn’t patched or modified to support packet injection.
- SSJ uses docker
--privilegedcapabilities and--net=host. It also adds a universal access control toxhostfor making GUI applications work, but immidiately closes it once you ext SSJ’sxfce4-terminalis exited. This might allow any application to access the X server or GUI in particular for the time SSJ is running. This can be a security or a privacy concern for many. - Audio ouput does not work as of now.
- Since the container runs with the root user, the files created in the
/rootdirectory have the owner set to root. On the host, this directory is/home/ssj. All the files and sub directories inside/home/ssjwill require the root user on the host in case any data needs to be written to or deleted from this directory.
And…
This script was created out of curiosity. This might solve a lot of problems. This might create new ones as well. It comes with no commitments. You are solely responsible for anything you may wish to do with this script. You can still feel free to file issues in case you experience any of them. Cheers!
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[MEDUSA] - Ransomware Victim: Pawnee Heights Unified School District 8 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)