Stealthy Symbiote Linux malware is after financial institutions
Symbiote, a new “nearly impossible to detect” Linux malware, targeted financial sectors in Latin America—and the threat actors behind it might have links to Brazil. These findings were revealed in a recent report, a joint effort between the Blackberry Research Team and Dr. Joakim Kennedy, a security researcher with Intezer.
Despite its name, this Trojan—first seen in November 2021—is more parasitic than a mutual benefactor in a symbiosis, according to Dr. Kennedy. And this is what sets Symbiote apart from other Linux malware.
“[I]t needs to infect other running processes to inflict damage on infected machines. Instead of being a standalone executable file that is run to infect a machine, it is a shared object (SO) library that is loaded into all running processes using LD_PRELOAD (T1574.006), and parasitically infects the machine.
Once it has infected all the running processes, it provides the threat actor with rootkit functionality, the ability to harvest credentials, and remote access capability.”
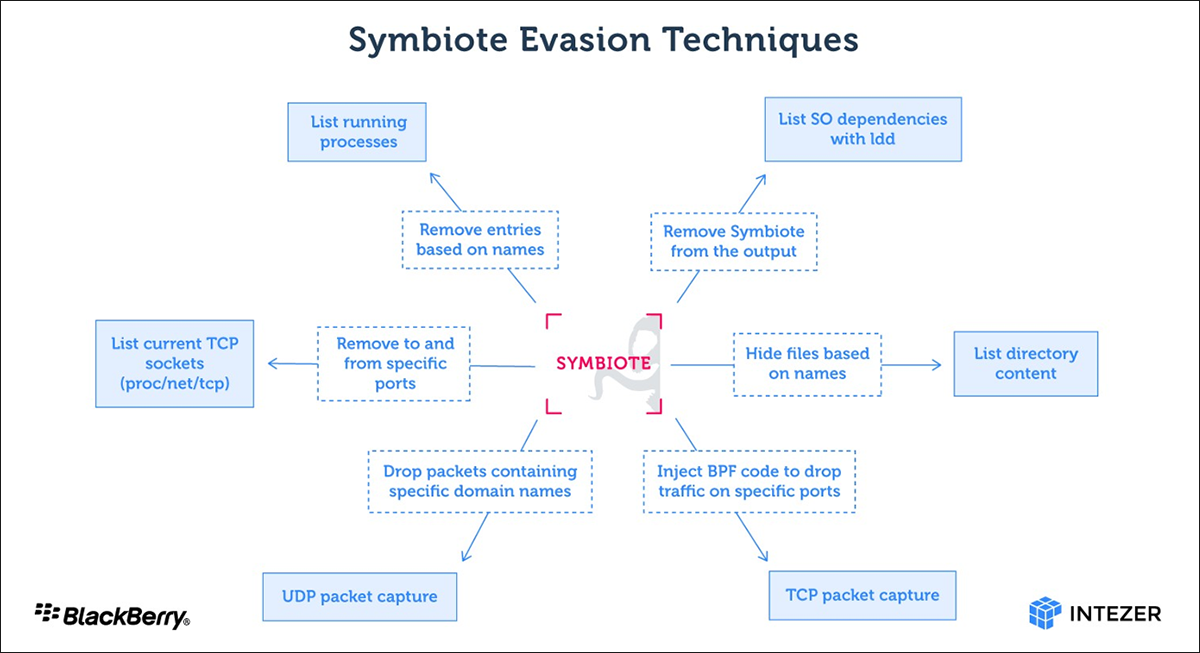
This abuse of the environmental variable LD_PRELOAD appears to be the “LD_PRELOAD trick” described in this post. Since Symbiote is a shared object, the threat actor can set LD_PRELOAD to its path. In effect, this malformed file is loaded first before other shared objects. And because it’s loaded first, Symbiote can “hijack the imports” from other SO files.
This enables it to hide on infected Linux machines.
Symbiote: the hows and whys of its ways
Once all processes have been infected, the Linux machine is as good as being infected. Symbiote then triggers its rootkit capabilities to hide, including other malware the threat actor may have dropped onto the device, processes, and network artifacts. This makes detection and active forensic examinations difficult.
Symbiote also offers threat actors a backdoor to the infected Linux machine, to which they can log in as a user with the highest privilege using a hardcoded password.
Per Dr. Kennedy, one exciting aspect Symbiote has is its Berkeley Packet Filter (BPF) hooking functionality. It does this to hide malicious traffic on an infected Linux machine. If you’re a threat actor, this is an excellent method when you don’t want to alert system admins of any network shenanigans on an infected Linux machine, as Symbiote can filter out such suspicious network traffic.
As a credential stealer, being stealthy is not an option.
“The malware’s objective, in addition to hiding malicious activity on the machine, is to harvest credentials and provide remote access for the threat actor. The credentials are first encrypted with RC4 using an embedded key, and then written to a file.
In addition to storing the credentials locally, the credentials are exfiltrated. The data is hex encoded and chunked up to be exfiltrated via DNS address record requests to a domain name controlled by the threat actor.”
The researchers further report that Symbiote impersonated Brazilian bank websites, suggesting Brazilians are the target of this campaign. The IP address of these domains is linked to the Njalla Virtual Private Server (VPS) service. Furthermore, “Passive DNS records showed that the same IP address was resolved to ns1[.]cintepol[.]link and ns2[.]cintepol[.]link a few months earlier.”
Cintepol is said to be the intelligence portal of the Federal Police of Brazil, which allowed its police officers to access intelligence from the federal police when investigating. This fake Cintepol site was abandoned in January 2022 in favor of another domain pointing to another Njalla VPS IP.
Protect against Symbiote
The threat actors behind Symbiote put a lot of effort into making it as under-the-radar as possible. However, Vulcan Cyber’s Mike Parkin, senior technical engineer, said in an interview with Dark Reading that the evasion tactics in Symbiote can still be detected by other network monitoring tools that can pinpoint malicious traffic and the infected Linux system.
Parkin further added that several endpoint tools should be able to identify malicious changes on infected systems.
“There are also forensic techniques that can use the malware’s own behavior against it to reveal its presence,” Parkin noted. “They leveraged a combination of techniques, though in so doing delivered some indicators of compromise that defenders could use to identify an infection in-situ.”
The Blackberry and Intezer report contains many indicators of compromise (IOCs) that IT admins should use to beef up the security of their Linux boxes.
You can also read our article on Malwarebytes’ EDR for Linux.
The post Stealthy Symbiote Linux malware is after financial institutions appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


