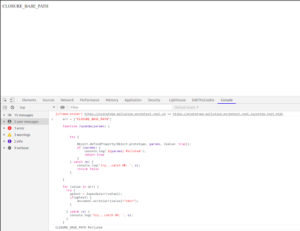
JSPanda – Client-Side Prototype Pullution Vulnerability Scanner
Source code analysis - Screenshot Supporting Materials : https://twitter.com/har1sec/status/1314469278322655233 https://github.com/BlackFan/client-side-prototype-pollution https://github.com/ThePacketBender/notes/blob/01c0b834f6e3ee4d934b087b2d92c9e484dc2a50/web/prototype_pollution.txt https://habr.com/ru/company/huawei/blog/547178/ https://infosecwriteups.com/javascript-prototype-pollution-practice-of-finding-and-exploitation-f97284333b2 https://github.com/securitum/research/tree/master/r2020_prototype-pollution Learn Prototype Pollution in Series -...










![[BLACKSHRANTAC] - Ransomware Victim: CCI Tax Pros, Inc 25 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
