BackupOperatorToolkit – The BackupOperatorToolkit Contains Different Techniques Allowing You To Escalate From Backup Operator To Domain Admin
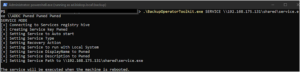
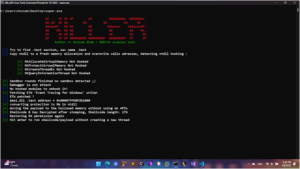
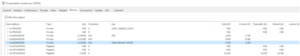
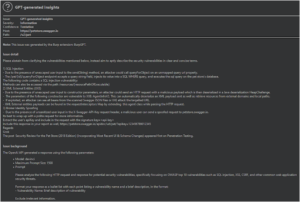
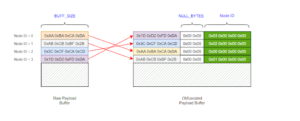
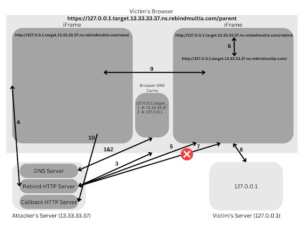
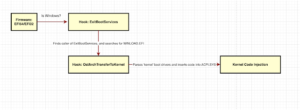
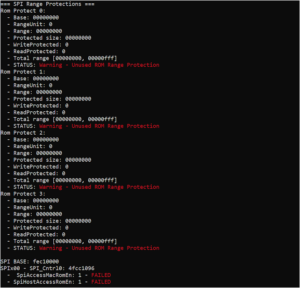
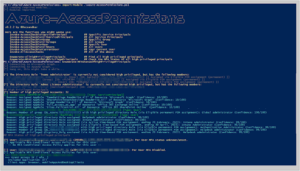
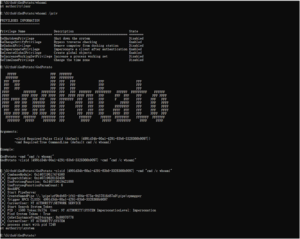
The BackupOperatorToolkit contains different techniques allowing you to escalate from Backup Operator to Domain Admin. Usage The BackupOperatorToolkit (BOT) has...









![[SAFEPAY] - Ransomware Victim: healthandvitalitycenter[.]com 26 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
