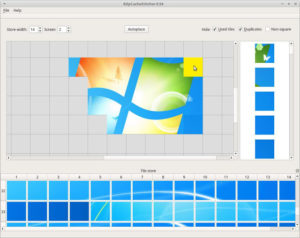
RdpCacheStitcher – RdpCacheStitcher Is A Tool That Supports Forensic Analysts In Reconstructing Useful Images Out Of RDP Cache Bitmaps
RdpCacheStitcher is a tool that supports forensic analysts in reconstructing useful images out of RDP cache bitmaps. Using raw RDP...