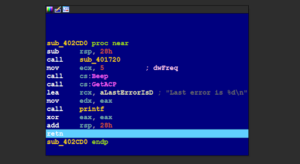
ClearURLs – An Add-On Based On The New WebExtensions Technology And Will Automatically Remove Tracking Elements From URLs To Help Protect Your Privacy
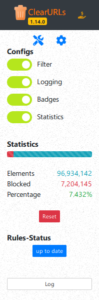
ClearURLs is an add-on based on the new WebExtensions technology and is optimized for Firefox and Chrome based browsers. This...