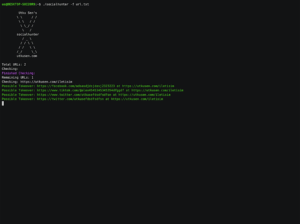
Previously undocumented Aoqin Dragon APT targets entities in Southeast Asia and Australia
Researchers spotted a previously undocumented Chinese-speaking APT, tracked as Aoqin Dragon, targeting entities in Southeast Asia and Australia. SentinelOne documented a...