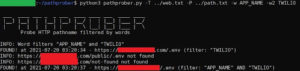
Pathprober – Probe And Discover HTTP Pathname Using Brute-Force Methodology And Filtered By Specific Word Or 2 Words At Once
Probe and discover HTTP pathname using brute-force methodology and filtered by specific word or 2 words at once. PurposeBrute-forcing website...













![Cobalt Strike Beacon Detected - 166[.]88[.]2[.]184:80 25 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
