Malware Analysis – djvu – 65178f6a1891f152c05326a628e6fa3a
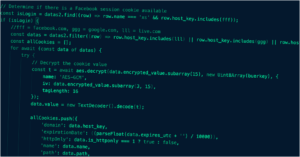
Score: 10 MALWARE FAMILY: djvuTAGS:family:djvu, family:vidar, botnet:31c7719b5ee962fbde376b75e771360d, discovery, persistence, ransomware, spyware, stealerMD5: 65178f6a1891f152c05326a628e6fa3aSHA1: 6a9b6ab36f14db9948e988c68d1b91d733315578ANALYSIS DATE: 2023-05-04T16:10:23ZTTPS: T1012, T1082, T1060, T1112,...








![LockBit 3.0 Ransomware Victim: triaflex[.]at 17 image-11](https://www.redpacketsecurity.com/wp-content/uploads/2022/06/image-11-300x142.png)
![Cobalt Stike Beacon Detected - 101[.]42[.]17[.]226:443 18 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)

