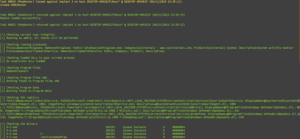
Invoke-EDRChecker – Checks Running Processes, Process Metadata, Dlls Loaded Into Your Current Process And The Each DLLs Metadata, Common Install Directories, Installed Services, The Registry And Running Drivers For The Presence Of Known Defensive Products Such As AV’s, EDR’s And Logging Tools
The script will check running processes, process metadata, Dlls loaded into your current process and the each DLLs metadata, common...


![Cobalt Stike Beacon Detected - 188[.]93[.]233[.]171:80 4 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)


![LockBit 2.0 Ransomware Victim: hancockassociates[.]com 17 lockbit_logo](https://www.redpacketsecurity.com/wp-content/uploads/2021/08/lockbit_logo-300x141.png)
