Telegram-Scraper – A Powerful Python Script That Allows You To Scrape Messages And Media From Telegram Channels Using The Telethon Library
A powerful Python script that allows you to scrape messages and media from Telegram channels using the Telethon library. Features...


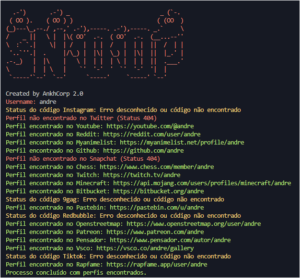

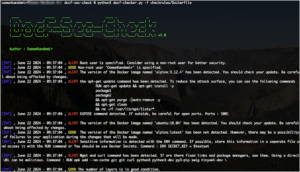








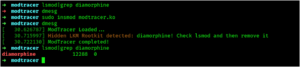
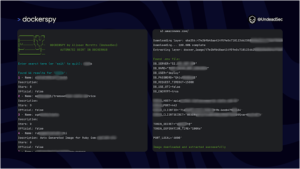
![Cobalt Strike Beacon Detected - 112[.]124[.]68[.]87:8080 25 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
