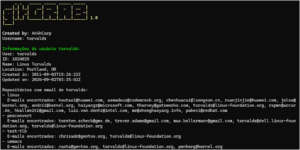
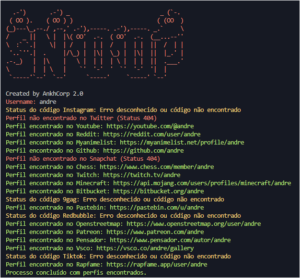
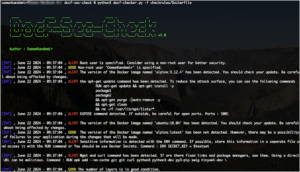
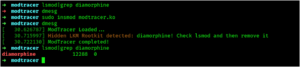
gitGRAB – This Tool Is Designed To Interact With The GitHub API And Retrieve Specific User Details, Repository Information, And Commit Emails For A Given User
This tool is designed to interact with the GitHub API and retrieve specific user details, repository information, and commit emails...













![[QILIN] - Ransomware Victim: Truro Cannabis 25 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

