ADFSRelay – Proof Of Concept Utilities Developed To Research NTLM Relaying Attacks Targeting ADFS
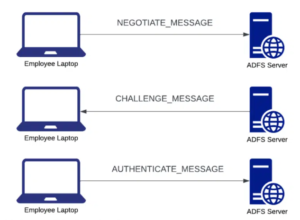
This repository includes two utilities NTLMParse and ADFSRelay. NTLMParse is a utility for decoding base64-encoded NTLM messages and printing information...






![[PLAY] - Ransomware Victim: Encore Repair Services 25 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
