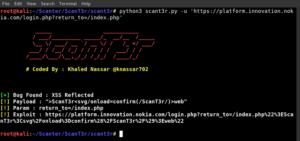
Maskprocessor – High-Performance Word Generator With A Per-Position Configureable Charset
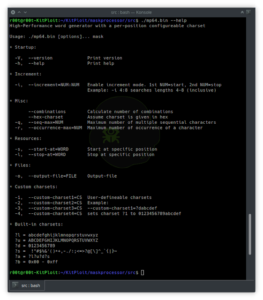
High-Performance word generator with a per-position configureable charsetMask attackTry all combinations from a given keyspace just like in Brute-Force attack,...