Task Force delivers strategic plan to address global ransomware problem
The Ransomware Task Force (RTF), a think tank composed of more than 60 volunteer experts who represent organizations encompassing industries and governments, has recently pushed out a comprehensive and strategic plan for tackling the increasing threat and evolution of ransomware.
The report, entitled “Combating Ransomware – A Comprehensive Framework for Action: Key Recommendations from the Ransomware Task Force”, which you can read here [PDF] advocates for “a unified, aggressive, comprehensive, public-private anti-ransomware campaign.”
The purpose of creating the document seems to be threefold: first, to educate the targeted reader—in this case, policy makers and industry leaders—about the dangers of ransomware; second, to call for unification amongst organizations to collectively beat the ransomware enterprise; and third, to guide organizations and governments on action items (48 in total) they can pursue to disrupt the ransomware-as-a-service (RaaS) model and extensively lessen the impact of current and future attacks.
“This is great news and sorely needed,” says Jerome Segura, Director of Threat Intelligence at Malwarebytes, in an email. “One key aspect is, of course, international cooperation (or the lack thereof) which has proven to be a key reason why many criminals from Eastern Europe can continue their business without real fear of prosecution.”
Ransomware: a threat to national security
Ransomware attacks had been popping up left and right, even before the COVID-19 pandemic threw a wrench into cybersecurity efforts of many already challenged companies and industries. Ransom demands inflated steeply through the pandemic, and the money raised appears to be being reflected in increasing innovation and sophistication.
The report quantifies the impact of a ransomware attacks with some startling statistics. According to the RTF the average ransom payment in 2020 was $312,493, an increase of 171% over the previous year. Perhaps even more costly and damaging, it puts the average time it takes to fully recover from a ransomware attack at just over nine months.
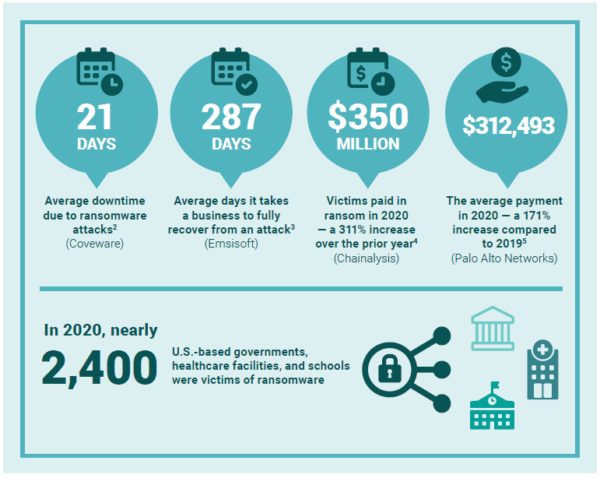
Note that these are average numbers, which means that there are cases when organizations have dealt with much longer downtimes and paid far higher ransoms (demands go into the tens of millions) to get their businesses back up and running as quickly as possible.
Gone are the days when threat actors behind ransomware campaigns targeted organizations they thought had the means to readily cough up money to meet their demands. These past few years, ransomware gangs have become more opportunistic, perhaps comforted by the wide availability of ransom insurance. They have deliberately targeted networks and breached systems of vital infrastructure, such as hospitals, schools, local governments, and nuclear plants, knowing full well that they may be putting lives at risk.
Organizations who refuse to pay the ransom have then to deal with the data leaking that will inevitably follow; the delays caused by identifying and fixing the problems that allowed the ransomware gang into its systems; and the cost to undergo crisis management efforts and generally getting back on track as quickly as possible, while also increasing their overall cybersecurity posture. On the other hand, organizations who do pay the ransom get to spend millions of dollars, too, on top of the ransom payment and still aren’t guaranteed to get their data back, or a speedy recovery.
Ransom payments may then used to fund criminal enterprises that, for example, engage in human trafficking, terrorism, and “the proliferation of mass destruction”. But perhaps the most damaging of all is that ransomware attacks can sow doubt in the minds of the public towards public institutions.
To add salt to the wound, ransomware threat actors do this from within countries that are turning a blind eye to, or even encouraging, these cybercrime campaigns. They are safe havens where gangs know they won’t be charged, prosecuted or extradited for their actions. It is not difficult then to see why the RTF urged its audience to “raise the priority of ransomware within the intelligence community, and designate it as a national security threat” while advocating the use of “criminal prosecution and other tactics”.
Core actions organizations and governments must take
Although there are multiple steps recommended in the report, the RTF prescribes that these steps should be viewed and considered part of a bigger whole as they were each designed to complement and build on each other.
According to the report:
“The strategic framework is organized around four primary goals: to deter ransomware attacks through a nationally and internationally coordinated, comprehensive strategy; to disrupt the business model and reduce criminal profits; to help organizations prepare for ransomware attacks; and to respond to ransomware attacks more effectively.”
To see the necessary impact against the ransomware enterprise, the task force stresses the importance of adopting these steps as soon as possible, with continuous coordination among the involved parties at a national and international level. (The RTF has proposed that the US government take charge in international coordination efforts with its partners.)
Among its priority recommendations, the RTF proposes that greater prioritization be given to an intelligence-driven anti-ransomware efforts; mandatory reporting of ransomware attacks and the creation of Cyber Response and Recovery funds; the development of a framework to help organizations prepare for, and respond to, ransomware attacks; and greater regulation of the cryptocurrency sector.

About the RTF and other anti-ransomware efforts
The Institute of Security and Technology (IST) is the host organization that launched the Ransomware Task Force four months ago in December 2020. Before this, significant efforts have been made by organizations within or associated with the cybersecurity industry in combating ransomware.
In January this year, the Cybersecurity and Infrastructure Security Agency (CISA) launched the Reduce the Risk of Ransomware Campaign where it focused on educating the public and private sectors on anti-ransomware best practices and what tools and resources to use to mitigate attacks. CISA’s one-stop page for everything one needs to know about ransomware can be found on this CISA ransomware page.
In July 2016, Europol’s European Cybercrime Centre joined forces with other law enforcement bodies and IT security companies to launch No More Ransom (NMR). Similar to the above mentioned efforts, NMR also aims to help victims recover their data without shelling out money. They do this by collating decryption tools for ransomware families, created by cybersecurity volunteers. You can learn more about No More Ransom by visiting its official website.
The post Task Force delivers strategic plan to address global ransomware problem appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


