Tech support scam campaign targets Japanese visitors to PornHub
The Malwarebytes Threat Intelligence team has identified a malvertising campaign targeting Japanese users. The campaign they discovered was found to be using a cloaking technique to lure visitors of popular adult site PornHub to a decoy site at the domain mixhd[.]club.
Cloaking
Cloaking is a method which gives visitors and search engines the impression that a website carries content that is different from what users actually see. In this case, every visitor that was not geolocated in Japan was shown a decoy page with content stolen from a well-known Japanese adult site.
The web server in this case decides what the visitor gets to see based on the information provided by the visitor like the user-agent string, browser language, IP address, and cookies.
Japan
With a population of some 125 million and a high level of connectivity, Japan has the third highest number of Internet users after China and the US. However, we hardly ever hear about any tech support scams directed at this audience.
In fact, the first arrests for tech support scams in Japan only happened in January this year, when Tokyo police announced that they had arrested three people in connection with an alleged scam where the suspects claimed to be providing technical support for malware-infected computers.
The campaign
Visitors to PornHub were shown an advertisement for another site with adult content. Users that followed the advertisement and that were fingerprinted as being Japanese were confronted with this browser lock page.
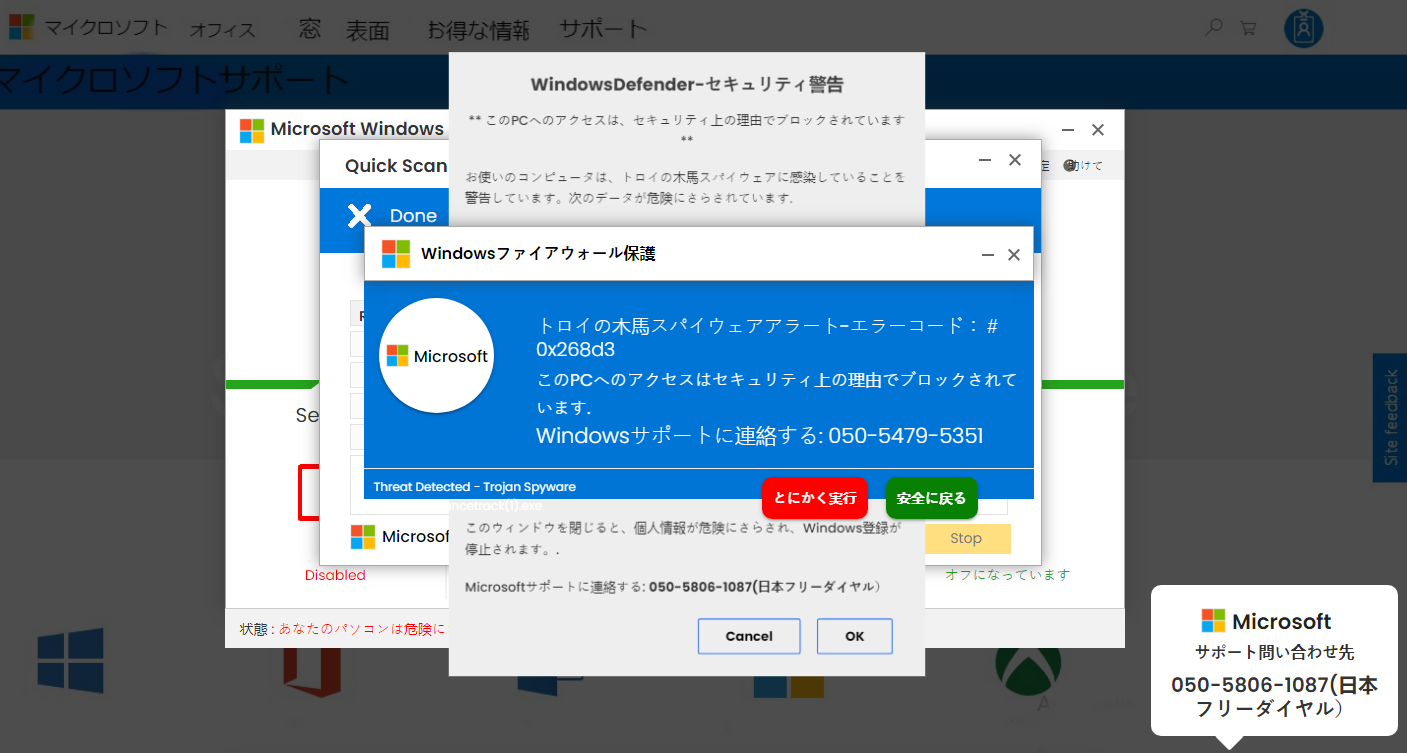
Popups and an audio warning on the page urge the victim to call Microsoft support, but shows telephone numbers that do not belong to Microsoft.
The goal is to defraud the victims in a tech support scam. Typically, scammers will use remote control of the affected system to help the victim get rid of the browser lock and the pop-ups at a steep price. They will then try to convince the victims to sign expensive contracts. In the case where the arrests were made, for example, victims were charged around ¥30,000 (US$ 245) for half-year contracts.
While most tech support scams are operated out of India, in this case Japanese police arrested the alleged ring master, a Filipino man. Based on additional evidence we collected, we believe there is a collaboration between criminal groups in India and the Philippines, with the former providing the traffic, pop-up alerts and browser locker infrastructure. But this is not limited to Japan, as we reported a few days ago tech support fraud is still a growing market in the US.
Stay safe, everyone!
The post Tech support scam campaign targets Japanese visitors to PornHub appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


