Telegram-powered bots circumvent 2FA
Two-factor authentication is a great way to protect your online accounts, and we always recommend you turn it on. But where users put up walls, you can be sure there are cybercriminals trying to break them down.
Yesterday, security intelligence firm, Intel 147, revealed it had noticed an uptick of activity in threat actors providing access to services in Telegram that circumvent two-factor authentication (2FA) methods. These services include calling their target victims, appearing to be from their bank, and socially engineering them into handing over a one-time password (OTP)—or other verification code—to the bot operators.
Other services target “other popular social media platforms or financial services, providing email phishing and SIM swapping capabilities.”
Intel 147 has been observing these activities since June when services like these started operating.
“[They] either operate via a Telegram bot or provide support for customers via a Telegram channel,” Intel 147 wrote, “In these support channels, users often share their success while using the bot, often walking away with thousands of dollars from victim accounts.”
The two bots that are becoming criminal favorites are SMSRanger and BloodOTPbot, according to Intel 147. Another bot, SMS Buster, was mentioned, but the researchers said operating it requires more effort on the part of the threat actor.
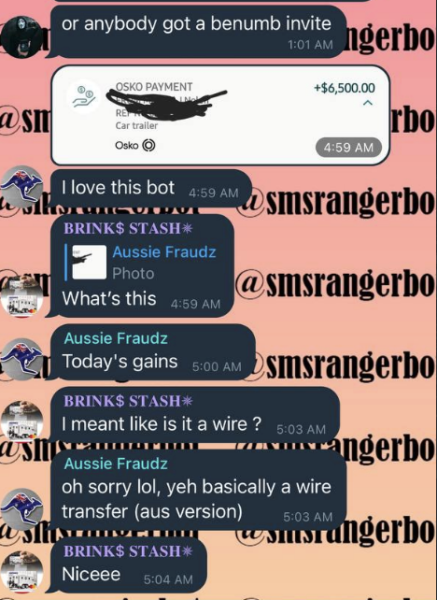
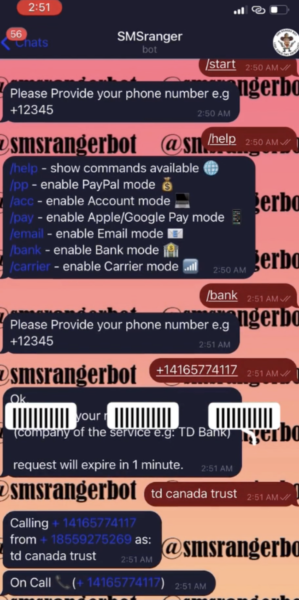
(Source: Intel 147 blog)
Those looking to operate these bots are expected to shell out $300 USD monthly. For additional services on top of the bot, they need to hand over an extra $20-$100 USD more.
2FA isn’t foolproof
These 2FA threats only further highlight the problem we already know about SMS-based and phone-call-based authentication OTP methods: they have weaknesses that can be easily exploited by threat actors.
Make no mistake: using 2FA is still better than not using it. But if companies start using better authentication methods, such as Time-Based One-Time Password (TOTP) codes—e.g. Google Authenticator and Authy—or push notifications—e.g. Okta or Duo—then such bots wouldn’t be much of a problem.
What to do
If you have sent your OTP to what you now believe is a scammer, call your bank and report it. Note that this might be a new scheme that banks have never heard of, so please do your best in explaining what happened. Remember that the more people report of the same or similar instances, the more aware banks will be of the fraud attempts.
Share your experience with friends and family to raise awareness on the matter, in order to prevent them falling for the same trick.
Remember that your bank won’t call you to ask for your OTP—ever—so if you receive similar requests in the future, just hang up.
Trust us: they won’t think you’re being rude.
Stay safe!
The post Telegram-powered bots circumvent 2FA appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![Cobalt Strike Beacon Detected - 154[.]204[.]35[.]215:80 4 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)