Terminator antivirus killer is a vulnerable Windows driver in disguise

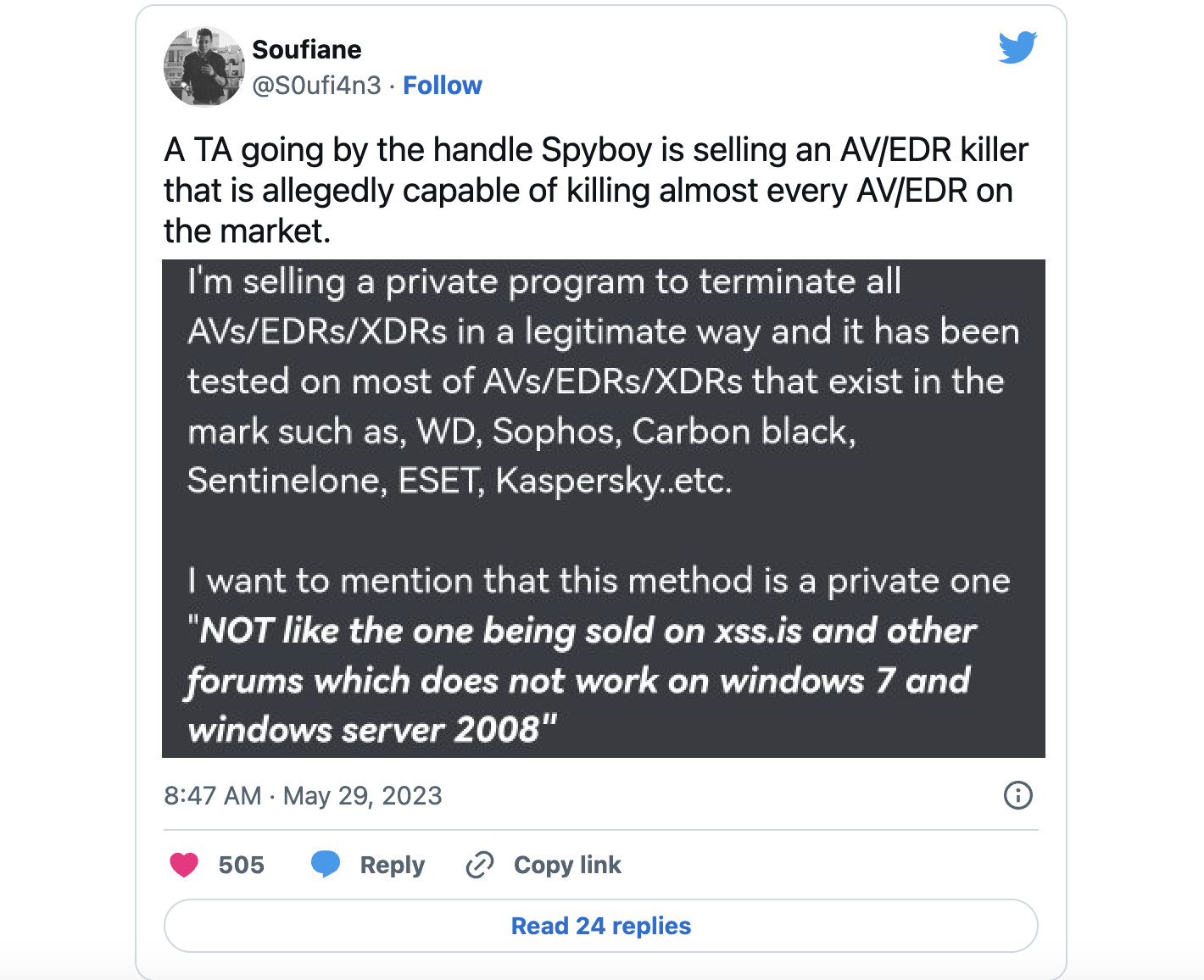
A threat actor known as Spyboy is promoting a tool called “Terminator” on a Russian-speaking hacking forum that can allegedly terminate any antivirus, XDR, and EDR platform. However, CrowdStrike says that it’s just a fancy Bring Your Own Vulnerable Driver (BYOVD) attack.
Terminator is allegedly capable of bypassing 24 different antivirus (AV), Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR) security solutions, including Windows Defender, on devices running Windows 7 and later,
Spyboy sells the software for prices ranging from $300 for a single bypass to $3,000 for an all-in-one bypass.
“The following EDRs cannot be sold alone: SentinelOne, Sophos, CrowdStrike, Carbon Black, Cortex, Cylance,” the threat actor says, with a disclaimer that “Ransomware and lockers are not allowed and I’m not responsible for such actions.”
To use Terminator, the “clients” require administrative privileges on the targeted Windows systems and have to trick the user into accepting a User Account Controls (UAC) pop-up that will be displayed when running the tool.
However, as a CrowdStrike engineer revealed in a Reddit post, Terminator just drops the legitimate, signed Zemana anti-malware kernel driver named zamguard64.sys or zam64.sys into the C:\Windows\System32\ folder with a random name between 4 and 10 characters.
After the malicious driver is written to the disk, Terminator loads it to use its kernel-level privileges to kill off the user-mode processes of AV and EDR software running on the device.
While it is not clear how the Terminator program is interfacing with the driver, a PoC exploit was released in 2021 that exploits flaws in the driver to execute commands with Windows Kernel privileges, which could be used to terminate normally-protected security software processes.
This driver is only being detected by a single anti-malware scanning engine as a vulnerable driver at the moment, according to a VirusTotal scan.
Luckily, Nextron Systems head of research Florian Roth and threat researcher Nasreddine Bencherchali have already shared YARA and Sigma (by hash and by name) rules that can help defenders detect the vulnerable driver used by the Terminator tool.
This technique is prevalent among threat actors who like to install vulnerable Windows drivers after escalating privileges to bypass security software running on the compromised machines, execute malicious code, and deliver additional malicious payloads.
In Bring Your Own Vulnerable Driver (BYOVD) attacks, as they are known, legitimate drivers signed with valid certificates and capable of running with kernel privileges are dropped on the victims’ devices to disable security solutions and take over the system.
A wide assortment of threat groups have used the technique for years, ranging from financially-motivated ransomware gangs to state-backed hacking outfits.
More recently, Sophos X-Ops security researchers have spotted a new hacking tool dubbed AuKill used in the wild to disable EDR software with the help of a vulnerable Process Explorer driver before deploying ransomware in BYOVD attacks.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.