Themoon Malware Infects 6 000 Asus Routers In 72 Hours For Proxy Service

A new variant of “TheMoon” malware botnet has been spotted infecting thousands of outdated small office and home office (SOHO) routers and IoT devices in 88 countries.
TheMoon is linked to the “Faceless” proxy service, which uses some of the infected devices as proxies to route traffic for cybercriminals who wish to anonymize their malicious activities.
Black Lotus Labs researchers monitoring the latest TheMoon campaign, which started in early March 2024, have observed 6,000 ASUS routers being targeted in under 72 hours.
The threat analysts report that malware operations such as the IcedID and SolarMarker currently use the proxy botnet to obfuscate their online activity.
Source: Black Lotus Labs
Targeting ASUS routers
TheMoon was first spotted in 2014 when researchers warned that the malware was exploiting vulnerabilities to infect LinkSys devices.
The malware’s latest campaign has been seen infecting nearly 7,000 devices in a week, with Black Lotus Labs saying they primarily target ASUS routers.
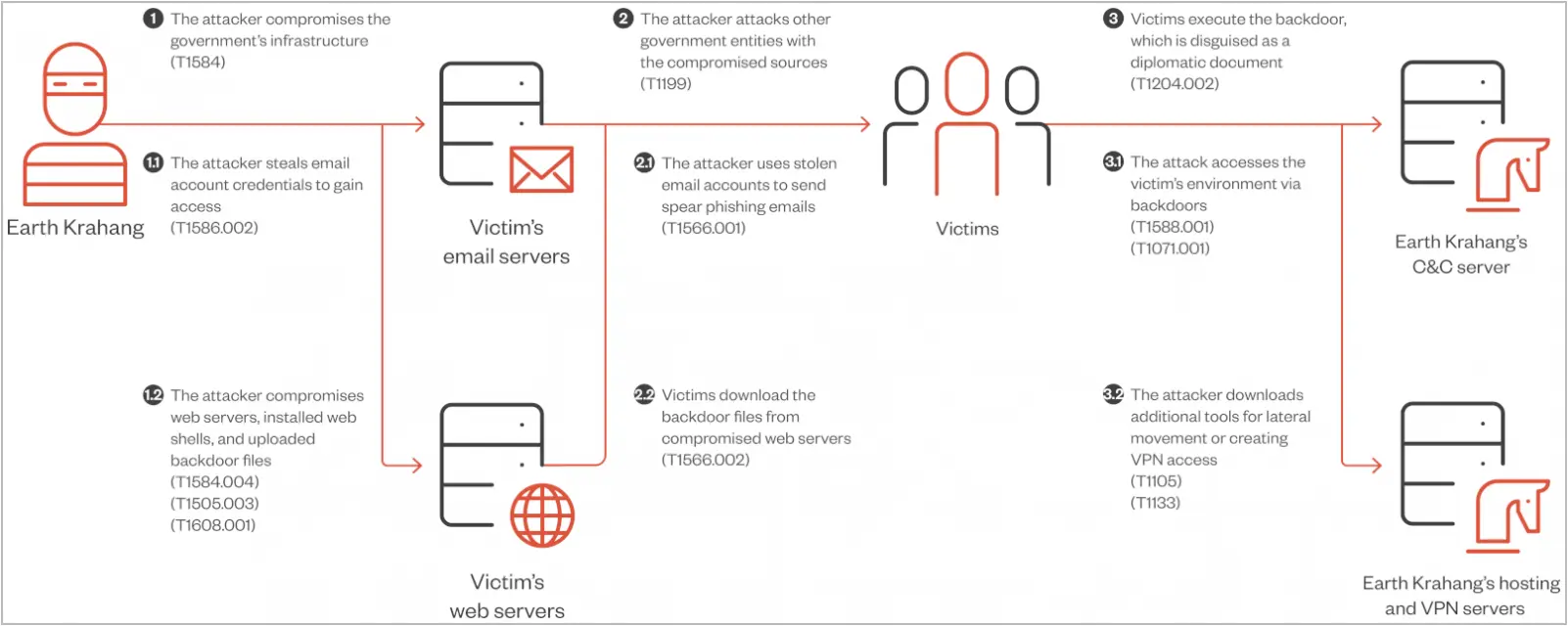
“Through Lumen’s global network visibility, Black Lotus Labs has identified the logical map of the Faceless proxy service, including a campaign that began in the first week of March 2024 that targeted over 6,000 ASUS routers in less than 72 hours,” warn the Black Lotus Labs researchers.
The researchers do not specify the exact method used to breach the ASUS routers, but given that the targeted device models are end-of-life, it is likely that the attackers leveraged known vulnerabilities in the firmware.
The attackers may also brute-force admin passwords or test default and weak credentials.
Once the malware gains access to a device, it checks for the presence of specific shell environments (“/bin/bash,” “/bin/ash,” or “/bin/sh”); otherwise, it stops the execution.
If a compatible shell is detected, the loader decrypts, drops, and executes a payload named “.nttpd” which creates a PID file with a version number (26 currently).
Next, the malware sets up iptables rules to drop incoming TCP traffic on ports 8080 and 80 while allowing traffic from specific IP ranges. This tactic secures the compromised device from external interference.
The malware next attempts to contact a list of legitimate NTP servers to detect sandbox environments and verify internet connectivity.
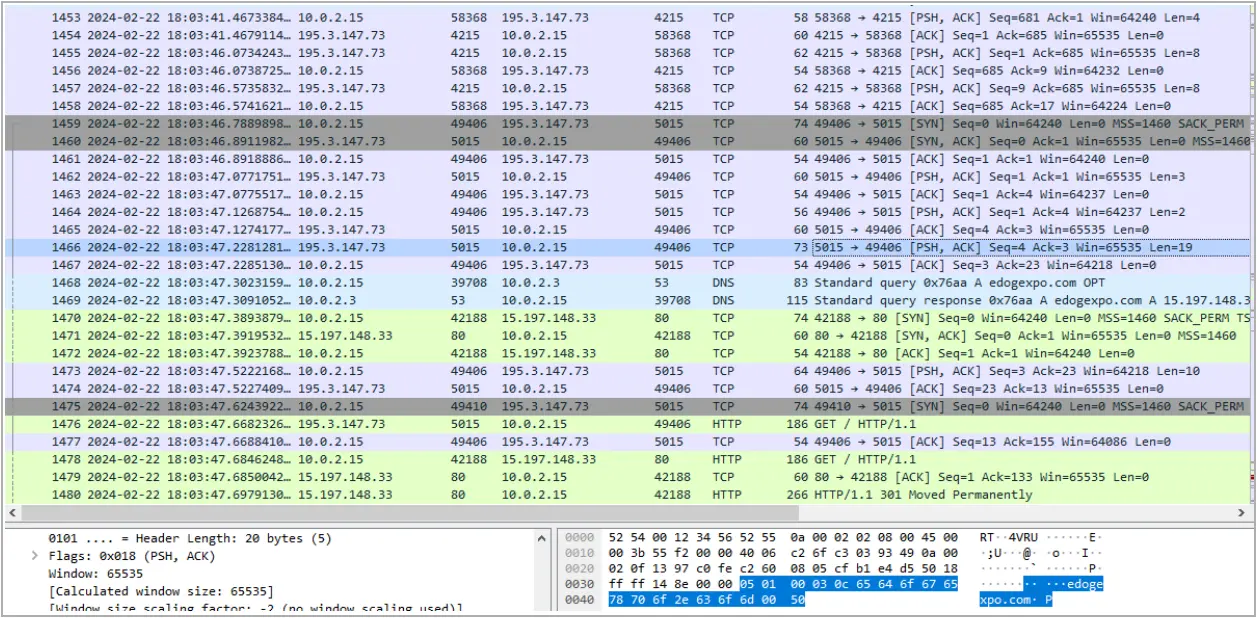
Finally, the malware connects with the command and control (C2) server by cycling through a set of hardcoded IP addresses, and the C2 responds with instructions.
In some cases, the C2 may instruct the malware to retrieve additional components, like a worm module that scans for vulnerable web servers on ports 80 and 8080 or “.sox” files that proxy traffic on the infected device.
Source: Black Lotus Labs
The Faceless proxy service
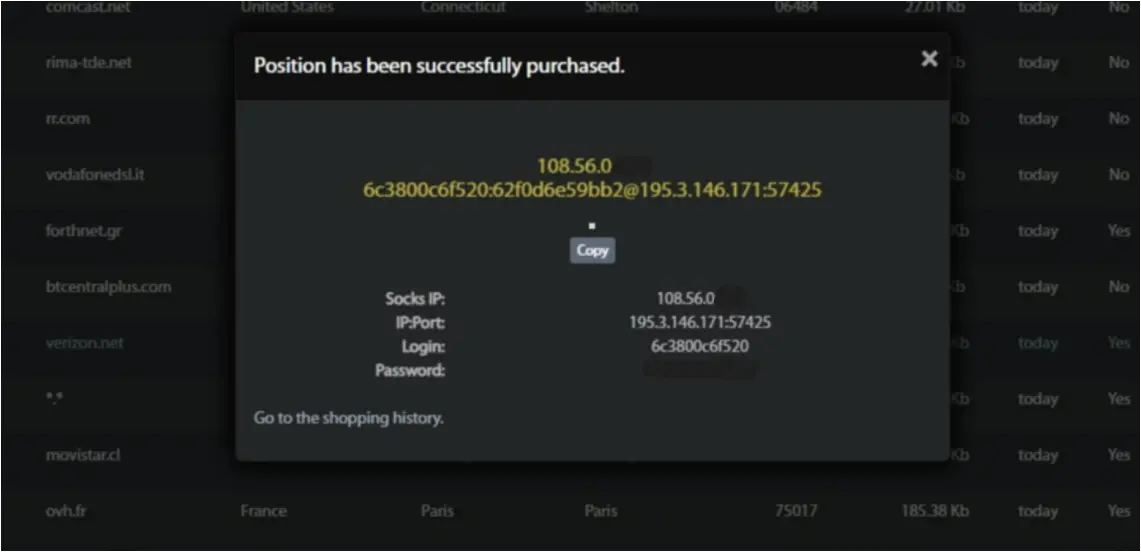
Faceless is a cybercrime proxy service that routes network traffic through compromised devices for customers who pay exclusively in cryptocurrencies. The service does not utilize a “know-you-customer” verification process, making it available to anyone.
Source: Black Lotus Labs
To protect their infrastructure from being mapped by researchers, Faceless operators ensure that each infected device communicates with only one server for as long as the infection lasts.
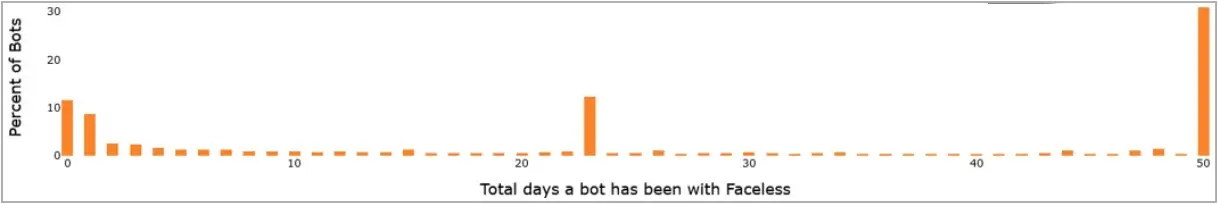
Black Lotus Labs reports that one-third of the infections last over 50 days, while 15% are lost in under 48 hours. This indicates that the latter are better monitored, and the compromise is detected quickly.
Source: Black Lotus Labs
Despite the clear connection between TheMoon and Faceless, the two operations appear to be separate cybercrime ecosystems, as not all malware infections become part of the Faceless proxying botnet.
To defend against these botnets, use strong admin passwords and upgrade your device’s firmware to the latest version that addresses known flaws. If the device has reached EoL, replace it with an actively supported model.
Common signs of malware infection on routers and IoTs include connectivity problems, overheating, and suspicious setting changes.
