Threat spotlight: DarkSide, the ransomware used in the Colonial Pipeline attack
Late last week, the business network systems of Colonial Pipeline, the biggest supplier of fuels on the East Coast of the United States, were compromised due to a ransomware attack, forcing the company to temporarily shut down its operations while investigations are underway.
Monday morning, Pacific time, the FBI confirmed that the ransomware culprit is DarkSide, a fairly new strain that started making a name roughly in mid- to late-2020. In this post, we take a look at the malware and the criminal gang, who many believe are based in Eastern Europe, behind the Colonial Pipeline attack.
Threat profile: DarkSide ransomware
DarkSide was first observed in the wild in August 2020 and used by the APT group Carbon Spider, also known as Carbanak and FIN7 among others, for their Big Game Hunting (BGH) campaigns. According to Crowdstrike’s adversary profile on this group, it originated in the Russian Federation and/or Ukraine. Since being active in 2013, Carbon Spider has targeted institutions in the Middle East, Europe, and eventually, the United States.
DarkSide ransomware is sold to affiliates using the Ransomware-as-a-Service (RaaS) distribution model, so attacks are carried out by affiliates.
There are currently two known versions of DarkSide: DarkSide v1.0 and DarkSide v2.1. The latter is less weighty in terms of file size (53 KB versus 59.5 KB) and has a shorter decryption time.
v2.1 has a new “call on us” feature, which allows ransomware affiliates to conduct a Voice Over IP (VoIP) session with victim organizations, their partners, and even journalists. It is believed that they added this feature to exert extra pressure against their victims.
DarkSide also has a Linux version that is capable of targeting VMWare ESXi vulnerabilities, making virtual machines (VMs) susceptible to hijacking and encryption of virtual drives.
Like other Big Game Hunting ransomware families, DarkSide is human-operated. This means that the ransomware is executed by an actual person behind the screen after they have successfully infiltrated a target network. This makes it possible for threat actors to move laterally, scouring the entire network to persistently backdoor several systems until they gain administrative access. They use these administrator credentials to deploy the DarkSide.
They also use their time in the network to harvest data and upload to their servers, before they encrypt the victim’s copy.
Once deployed, DarkSide begins to:
- Encrypt all files using a combination of Salsa20 and RSA-1024
- Empty the Recycle Bins
- Uninstall services
- Delete shadow copies
- Terminate processes
- Encrypt local disks
- Encrypt network shares
After all the data have been exfiltrated, the threat actors post it on their leak site, DarkSide Leaks, along with other pertinent information about the attack, such as the name of the company, the date it was breached, how much data was stolen, sample screenshots of the stolen data, and the types of stolen data.
It is observed that DarkSide and REvil ransomware, also known as Sodinokibi, share some similarities:
- Their ransom notes seem to have come from the same template.
- Both ransomware families use Windows PowerShell to delete shadow volume copies on compromised systems,
- …and both families also use a particular string of PowerShell code to perform this action.
DarkSide ensures that victims feel their personalized touch by customizing the ransom note and file extension for their victims. For example, a checksum of the victim’s MAC address is used as the extension name of encrypted files when, normally, ransomware would just use their own pre-defined extension. (HelloKitty ransomware uses .kitty, for example.)
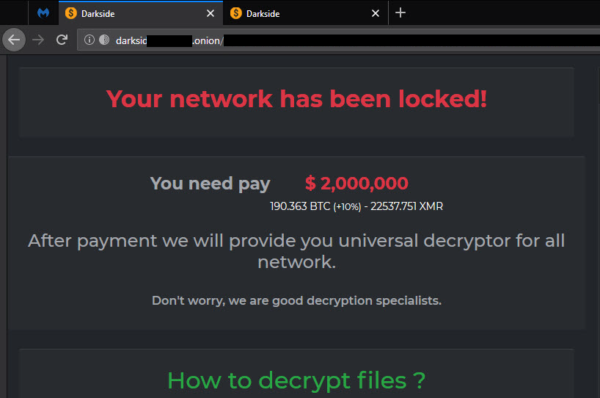
A portion of a DarkSide ransom note is reproduced below. Ransom notes include the type of files, a link to the victim organization’s personal leak page, and instructions on what victims can do.
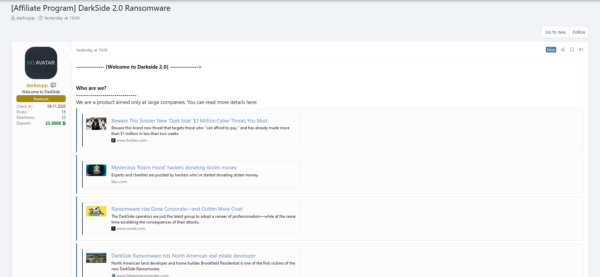
----------- [ Welcome to DarkSide 2.0] -----------> What happend? --------------------------------------------- Your computers and servers are encrypted, backups are deleted. We use Strong encryption algorithms, so you cannot decrypt your data. But you can restore everything by purchasing a special program from us - universal decryptor. This program will restore all your network. Follow our instructions below and you will recover all your data. Data leak --------------------------------------------- First of all we have uploaded more than full dump data. These files include: - finance - private information - partners documents
The DarkSide leaks website has a “Press Center” section where journalists can register. It has a section where “recovery companies”—victimized organizations that had no choice but to give in to DarkSide’s ransom demand—can register to receive decryptors, get additional “discounts”, and have a ready line to the threat actor’s support service. All of which demonstrates how organized DarkSide operators can be.
Malwarebytes’ signature-less protection detects all known variants of DarkSide.
Adversary profile: DarkSide operators
Leslie Carhart, DFIR at Dragos, has taken note that DarkSide operators have been increasing their double-extortion attacks yet somehow successfully getting little attention.
The threat actors behind DarkSide ransomware are doing all this to gain money. However, its original creators declared that criminal groups who want to partner with them via their RaaS scheme should avoid targeting companies in certain sectors. These are:
- Healthcare
- Education
- Nonprofit
- Government
DarkSide may seem like your common-or-garden ransomware gang who only cares about making money off of the backs of organizations, including hospitals, but they would like you to think otherwise. One of the things that separates the DarkSide gang from the other “heartless” gangs is their declared intent to “make the world a better place”.
In 2020, the gang did just that by donating a portion of the money they extorted from victims to charity—not realizing that charities, knowing that the money is fraudulent, would never accept it. Not only that, charities who do accept fraudulent money without them knowing can get into a lot of trouble from the law. They can be charged with crimes related to money laundering—something perhaps the DarkSide gang didn’t see coming when thinking about the children.
In common with many other ransomware gangs, it’s also their mandate not to target states under the Commonwealth of Independent States (CIS), including Georgia and Ukraine.
While they reach for this dubious moral high ground, let us not forget that DarkSide threat actors have not only threatened victim organizations to leak all their files but also weaponize them by sharing them to their competitors, the media, and government regulators.
After the Colonial Pipeline attack made headlines and got the attention of no less than the FBI and the US government, DarkSide released a statement about it:
We are apolitical, we do not participate in geopolitics, do not need to tie us with a defined government and look for other our [sic] motives.
Our goal is to make money, and not creating problems for society.
From today we introduce moderation and check each company that our partners want to encrypt to avoid social consequences in the future.
Many suspect that DarkSide operators are already in a mad rush to patch things up, having bitten off more than they can chew.
The straw that broke the camel’s back?
The DarkSide attack on the Colonial Pipeline may turn out to be the straw that broke the camel’s back. Last week, the White House held emergency meetings to take a look at an already drafted Executive Order on cybersecurity—possibly to strengthen it following this latest attack—that is expected to be released soon. Prior to that, the US Justice Department has already announced a 120-day review of its approach to combating cyberthreats, and been urged by the Ransomware Task Force’s strategic plan for tackling ransomware to treat ransomware as a national security threat.
Yesterday, the FBI and the US Cybersecurity and Infrastructure Security Agency (CISA) issued a joint cybersecurity advisory (CSA) against DarkSide ransomware. It contains detailed mitigation steps that business should follow to reduce the risk of successful ransomware attacks overall. These include simple steps, such as:
- Using multi-factor authentication (MFA) to access networks remotely
- Enabling stronger spam filters
- Updating software to their latest versions
- Regularly scanning systems using a good antivirus product, and
- Limiting access to resources over networks
Organizations of all sectors should take heed of these best practices. Because before the publication of this article, DarkSide appears to have netted another victim.
The post Threat spotlight: DarkSide, the ransomware used in the Colonial Pipeline attack appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



