Top 5 Ways to Get a Network Traffic Source on Your Network

In my last blog post, I looked at How Rapid7 Customers Are Using Network Traffic Analysis in Detection and Response. However, none of these use cases are possible without a source of network traffic. If you want to monitor network traffic on your network, you will need a source of network packets. Thankfully, there are many options available, and in this post I am going to take a brief look at the five most popular.
1. SPAN or port mirroring on physical switches
A SPAN or mirror port is a passive way to get a copy of traffic from a network switch. Most managed switches will have options for setting up port or VLAN mirroring. If supported by your switch vendor, VLAN mirroring is easy and powerful. For example, this one command monitor session 1 source vlan 1 both allows you to instantly monitor all the traffic to and from the servers in your server VLAN if you use VLAN ID 1.
When configured, the switch will send a copy of the selected port or VLAN traffic to a nominated port. This is a passive method of traffic capture that does not interfere with the communication between clients and servers. If you want to read up on what options are available for your switches, there is a useful resource at this link that has a reference for the most popular vendors and switches.
The image below shows a typical setup where your network traffic analysis tool is connected to a SPAN or mirror port on a core switch. A core switch is an ideal location, as a lot of interesting network traffic will pass through this point.
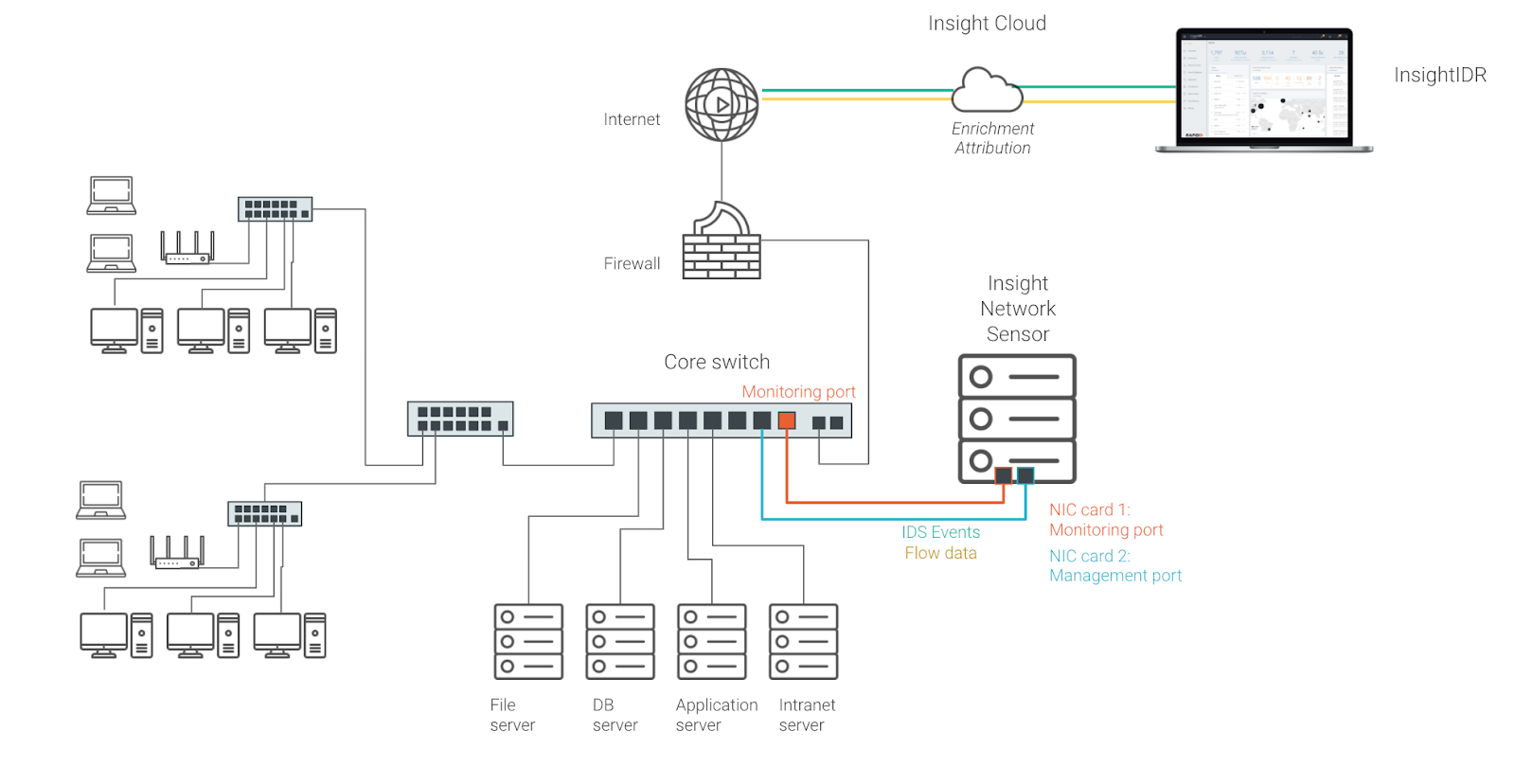
This is recommended if you need north-south and east-west network traffic visibility. You do need a way to connect your Insight Network Sensor to the SPAN or mirror port. Either install your sensor on a dedicated server or allocate a dedicated NIC on a Hypervisor so you can connect a VM to this network traffic source.
2. Virtual port groups
One of the easiest ways to get started with network traffic analysis is to deploy an Insight Network Sensor as a virtual machine and monitor traffic associated with virtual hosts. This includes traffic within the virtual environment as well as traffic to and from external network devices.
A Hypervisor or virtual machine host such as VMWare ESX allows you to capture network traffic by using a feature called promiscuous mode on virtual port groups. This approach requires no physical hardware, no network cables, nor any changes to your network switches. It can be done in minutes while sitting at your desk.
The image below shows a typical setup where one NIC of a network traffic analysis tool is connected to a virtual machine port group. The security settings of this port group are then modified to allow promiscuous mode so that this NIC can capture traffic associated with other virtual machines.
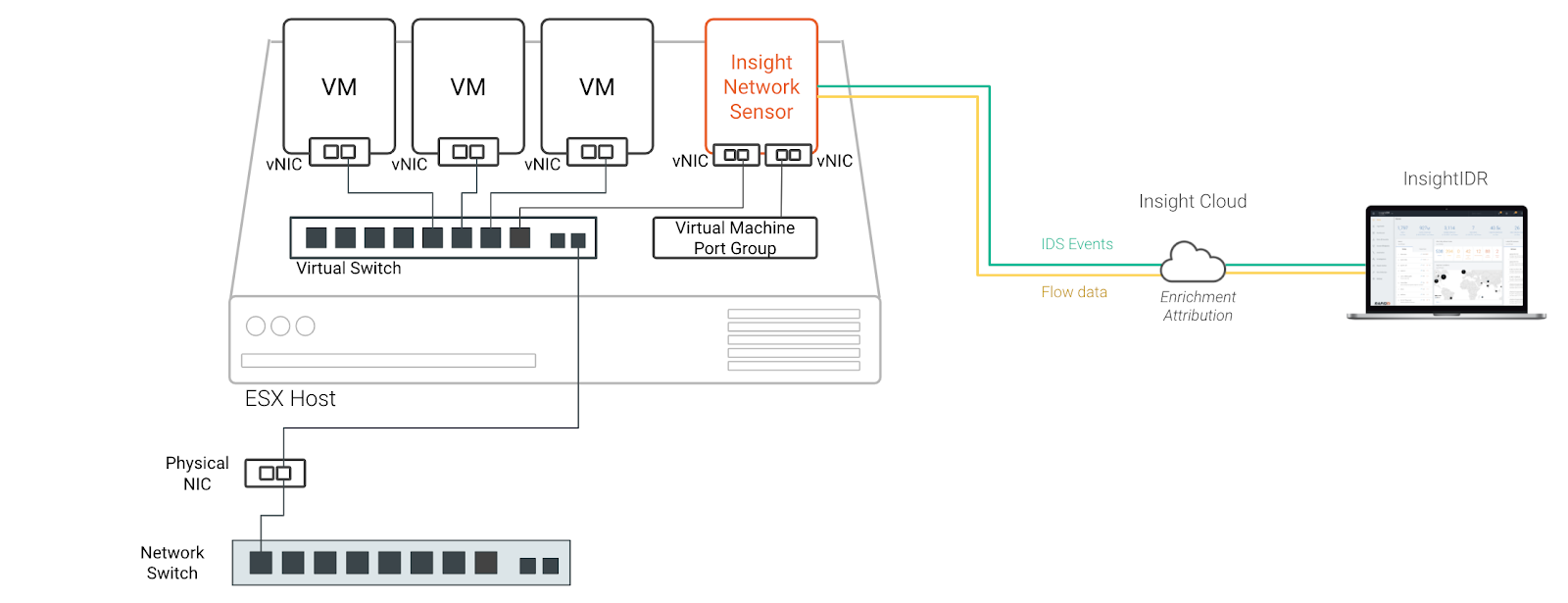
This is recommended if you want a quick way to set up network traffic analysis for a POC. It’s also useful for finding out what is happening inside virtual network environments.
3. Mirror ports on virtual switches
Enterprise-sized networks will often contain multiple hypervisors for load sharing and resiliency. In order to gain visibility into what is happening within these environments, you have two options: Either deploy an Insight Network Sensor on every host, or use the port mirroring feature available on distributed switches. This port mirroring option allows you to use a single network sensor to gain visibility across multiple ESX hosts.
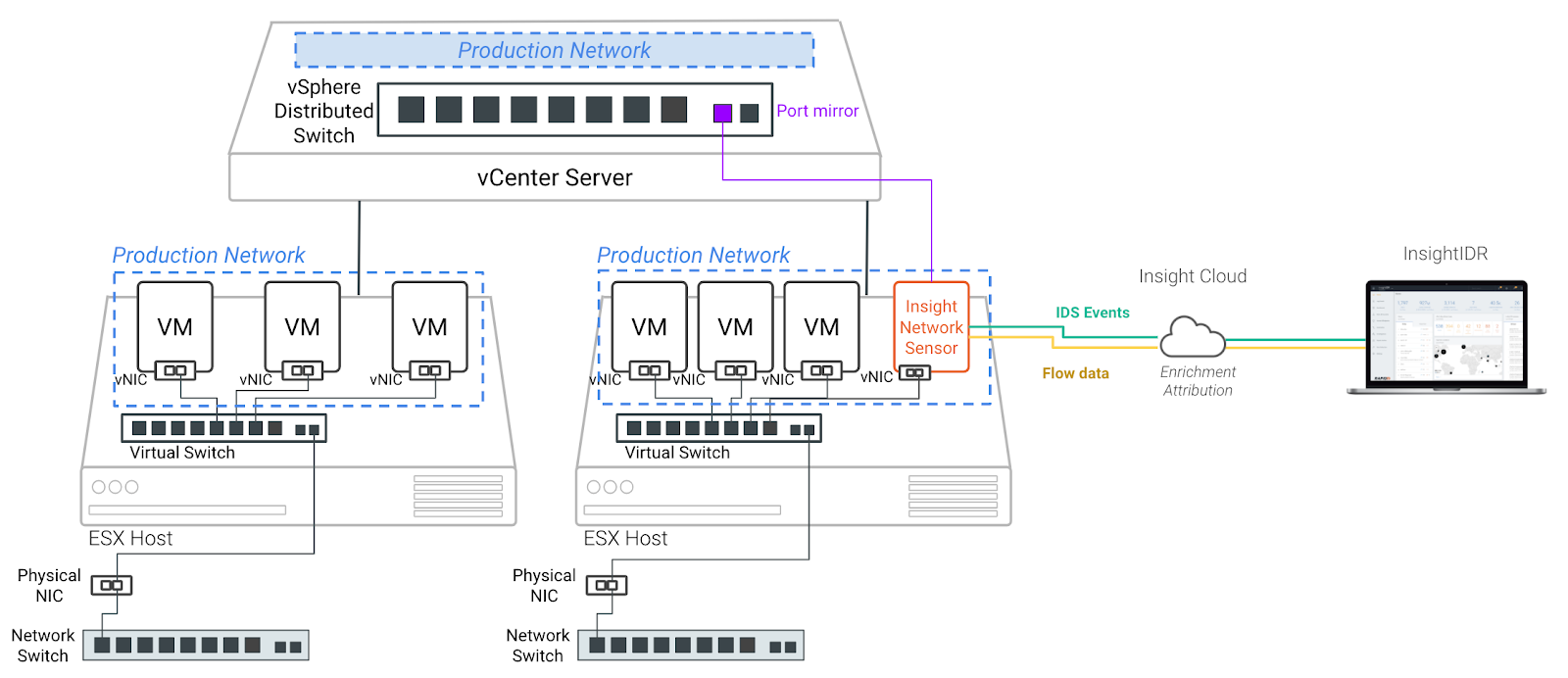
This is recommended if you use vCenter Server and require visibility across multiple ESX hosts with a single Insight Network Sensor.
4. Network TAPs and packet brokers
A network TAP has (at least) three ports: an input port, an output port, and a monitor port. A TAP inserted between two network devices passes all traffic (send and receive data streams) through, unimpeded in real time, but also copies that same data to its monitor port, enabling a data source for network traffic analysis. Downtime is required initially to get the TAP in place. A common point to TAP on a network would be the connection to and from a firewall.
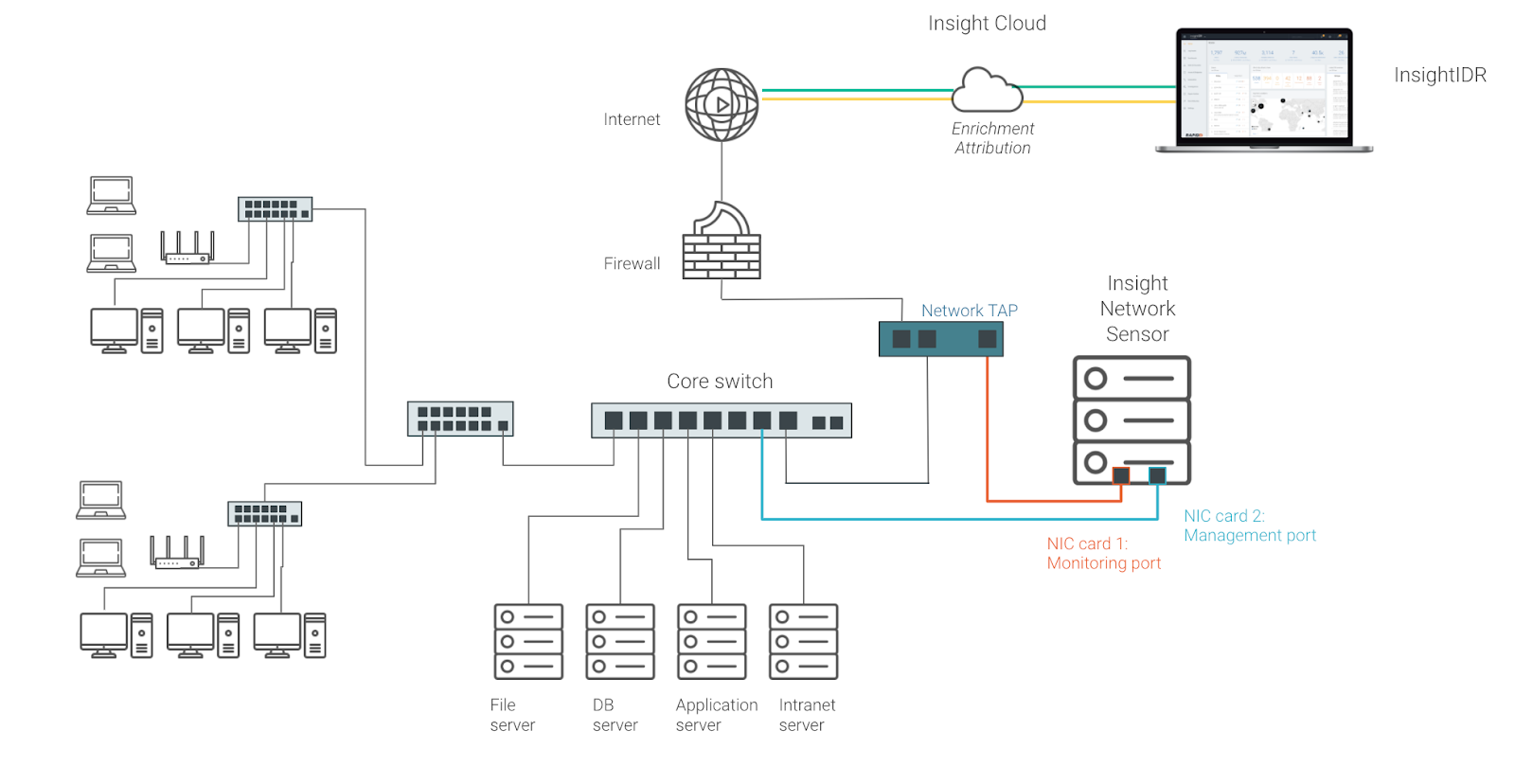
A Network Packet Broker is a physical device that directs selected raw data packets from network interfaces (typically via SPAN or network TAP points) to specific network traffic analysis devices, and security applications such as an IDS. Some IT and security managers have a requirement for packet brokers, as most switches only provide for two SPAN outputs and they require more outputs for various security and operational tools.
This is recommended if you have an existing TAP or packet broker on your network. There’s no need to install one if you are new to traffic analysis and have SPAN or mirror ports on your network that are not all used up.
5. Cloud-based virtual TAPs
Most cloud providers have options for virtual TAPs or port mirroring. They operate similar to the way SPAN or port mirroring works. You specify what you want to monitor, then choose a mirror target, which can be a virtual NIC connected to your network traffic analysis system. Amazon AWS calls its feature “VPC Traffic Mirroring.”
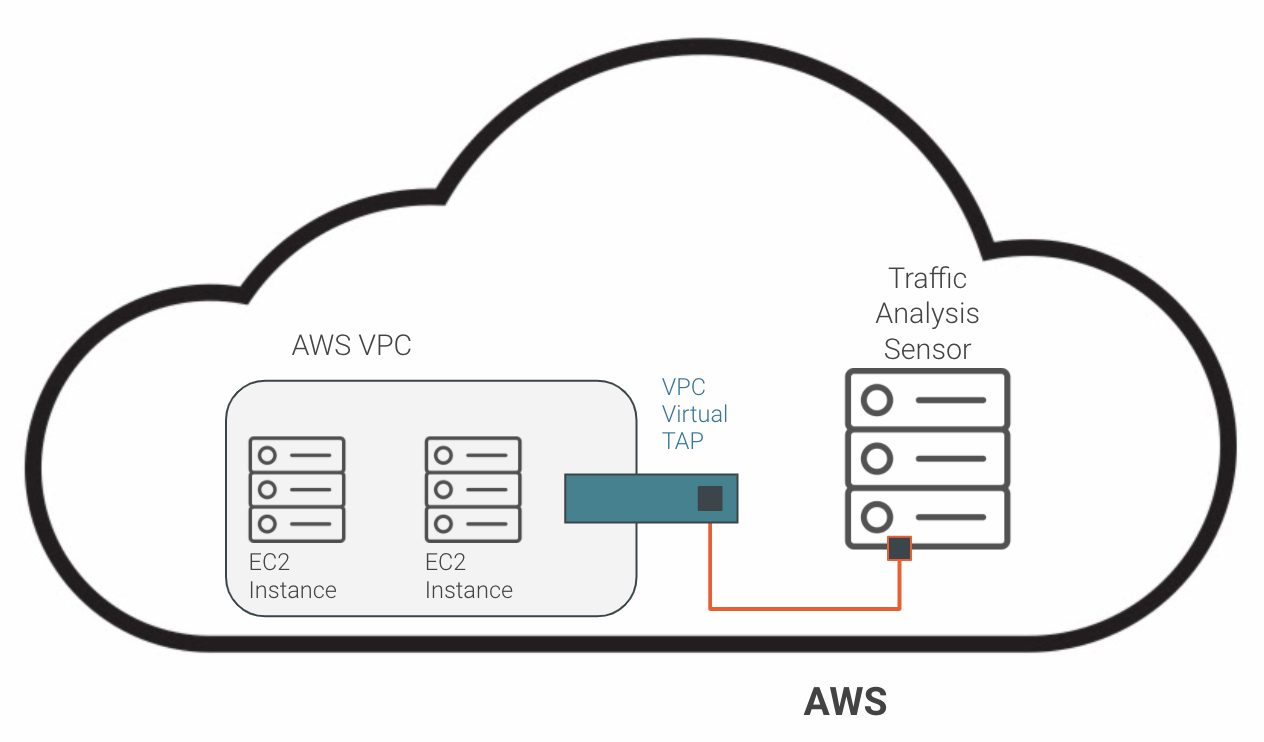
This is recommended if you want to monitor network traffic and/or detect and alert on suspicious activity within your cloud estates.
What option is best for you?
No matter what type of network topology you have, you will have options to monitor network traffic. If you have a virtual environment such as VMWare and you want something quick and easy to set up without any hardware requirements, check out the port group option.
If you need east-west as well as north-south network visibility, check out SPAN or port mirroring off your core switch. Without any downtime or making any major changes to your network, these options allow you to leverage network traffic analysis to instantly obtain deep visibility across your network.
[On-Demand Demo] See our network traffic analysis capabilities in action
Watch Now
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


