Update now! Chrome fix patches in-the-wild zero-day
The Microsoft Browser Vulnerability Research team has found and reported a vulnerability in the audio component of Google Chrome. Google has fixed this high-severity vulnerability (CVE-2021-21166) in its Chrome browser and is warning Chrome users that an exploit exists in the wild for the vulnerability. It is not the first time that Chrome’s audio component was targeted by an exploit.
No details available
Further details about the vulnerability are restricted until a majority of Chrome users have updated to the patched version of the software. What we do know is that it concerns an object lifecycle issue in the audio component of the browser.
An object lifecycle is used in object oriented programming to describe the time between an object’s creation and its destruction. Outside of the lifecycle the object is no longer valid, which could lead to a vulnerability.
For example, if everything goes as planned with the lifecycle the correct amount of computer memory is allocated and reclaimed at the right times. If it doesn’t go well, and memory is mismanaged, that could lead to a flaw – or vulnerability – in the program.
More vulnerabilities patched in the update
As per usual Google patched several other vulnerabilities and bugs in the same update. Some of the other vulnerabilities were listed with high severity:
Google said that it fixed three heap-buffer overflow flaws in the TabStrip (CVE-2021-21159, CVE-2021-21161) and WebAudio (CVE-2021-21160) components. A high-severity use-after-free error (CVE-2021-21162) was found in WebRTC. Two other high-severity flaws include an insufficient data validation issue in Reader Mode (CVE-2021-21163) and an insufficient data validation issue in Chrome for iOS (CVE-2021-21164).
The CVE’s
Publicly disclosed computer security flaws are listed in the Common Vulnerabilities and Exposures (CVE) database. Its goal is to make it easier to share data across separate vulnerability capabilities (tools, databases, and services).
- CVE-2021-21159, CVE-2021-21161: Heap buffer overflow in TabStrip. Heap is the name for a region of a process’ memory which is used to store dynamic variables. A buffer overflow is a type of software vulnerability that exists when an area of memory within a software application reaches its address boundary and writes into an adjacent memory region. In software exploit code, two common areas that are targeted for overflows are the stack and the heap.
- CVE-2021-21160: Heap buffer overflow in WebAudio.
- CVE-2021-21162: Use after free in WebRTC. Use after free (UAF) is a vulnerability due to incorrect use of dynamic memory during a program’s operation. If after freeing a memory location, a program does not clear the pointer to that memory, an attacker can use the error to manipulate the program. WebRTC allows programmers to add real-time communication capabilities to their application.
- CVE-2021-21163: Insufficient data validation in Reader Mode. Insufficient data validation could allow an attacker to use especially crafted input to manipulate a program.
- CVE-2021-21164: Insufficient data validation in Chrome for iOS.
When more details about the vulnerabilities come to light it’s possible that more exploits for them will be found in the wild. It depends a lot on how easy they are to abuse, and how big the possible impact can be. But with one already being used in the wild, it is advisable to update now.
How to update
The easiest way to do it is to allow Chrome to update automatically, which basically uses the same method I outlined below but does not require your attention. But you can end up lagging behind if you never close the browser or if something goes wrong, such as an extension stopping you from updating the browser.
So, it doesn’t hurt to check now and then. And now would be a good time.
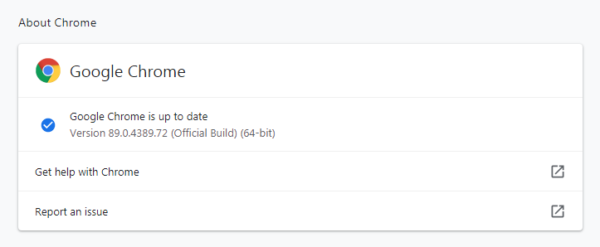
My preferred method is to have Chrome open the page chrome://settings/help which you can also find by clicking Settings > About Chrome.
If there is an update available, Chrome will notify you and start downloading it. Then it will tell you all you have to do to complete the update is Relaunch the browser.
Stay safe, everyone!
The post Update now! Chrome fix patches in-the-wild zero-day appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


