VMware warns admins of critical Carbon Black App Control flaw

VMware has released a critical security upgrade to address a critical injection vulnerability that impacts several versions of Carbon Black App Control for Windows.
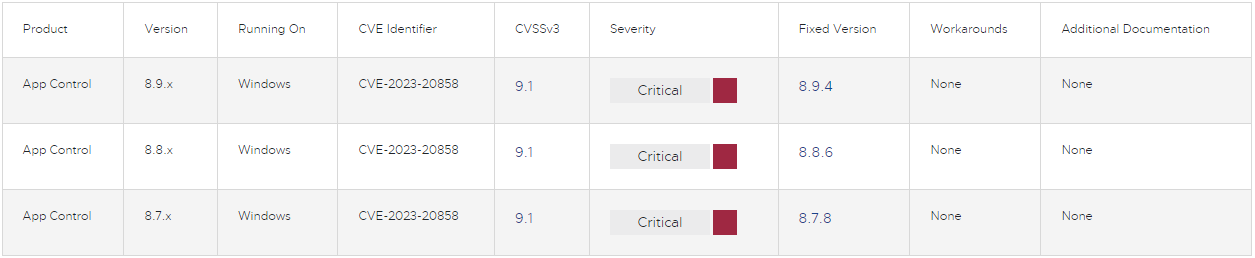
The company warns that the severity rating of the security issue is 9.1 out of 10 and that an attacker can leverage it to gain access to the underlying operating system.
Carbon Black App Control is a suite designed to help large organizations ensure that its critical endpoints run only trusted and approved software.
Tracked as CVE-2023-20858, the issue was discovered by security analyst Jari Jääskelä and could allow a threat actor with privileged access to the App Control administration console to get access to the operating system using specially crafted input.
“A malicious actor with privileged access to the App Control administration console may be able to use specially crafted input allowing access to the underlying server operating system,” reads VMware’s advisory.
Injection flaws allow attackers to execute commands or code in the target app. They can lead to complete compromise of backend systems and all clients that connect to the vulnerable application.
VMware strongly recommends administrators to “upgrade as soon as possible” to a safe version of the product.
CVE-2023-20858 impacts VMware Carbon Black App Control for Windows version 8.7.7 and older, version 8.8.5 and older, and version 8.9.3 and older. Administrators are recommended to upgrade to versions 8.9.4, 8.8.6, and 8.7.8 or later.
VMware’s security advisory has shared no workarounds or mitigation advice, so the only safe option is to move to the recommended versions.
On Tuesday, VMware also patched CVE-2023-20855, a high-severity (CVSS v3: 8.8) XXE (XML external entity) injection flaw that could enable an attacker to bypass XML parsing restrictions to access sensitive information or perform privilege escalation.
CVE-2023-20855 impacts VMware Orchestrator below v8.11.1 (fixed version), vRealize Automation below v8.11.1 (fixed version), and VMware Cloud Foundation 4.x (fixed in KB90926).
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below

To keep up to date follow us on the below channels.





