Warning: GravityRAT Android Trojan Steals WhatsApp Backups and Deletes Files
An updated version of an Android remote access trojan dubbed GravityRAT has been found masquerading as messaging apps BingeChat and Chatico as part of a narrowly targeted campaign since June 2022.
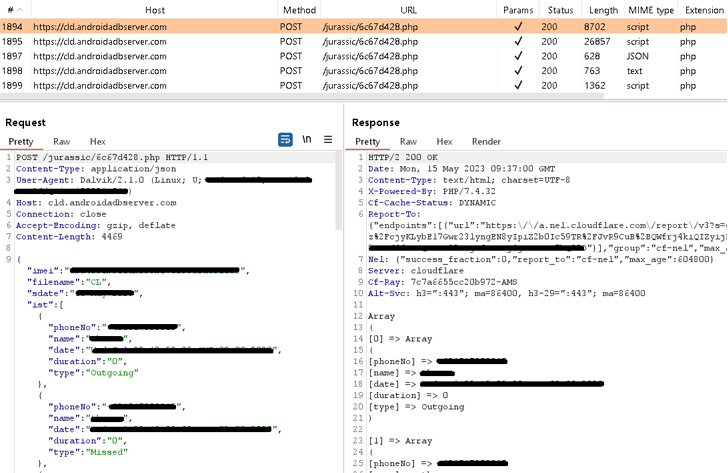
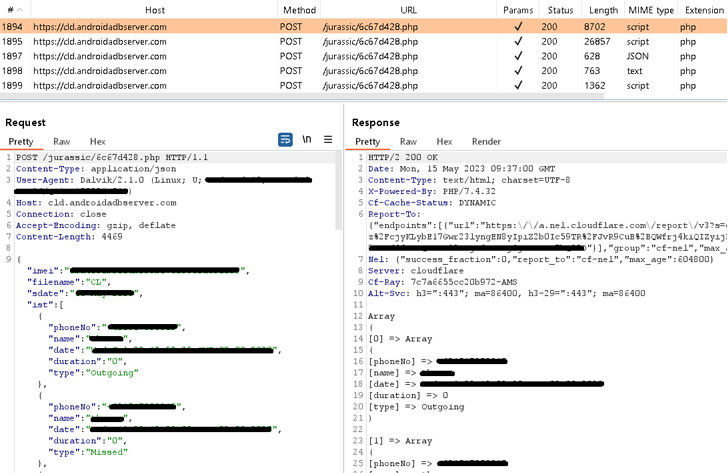
“Notable in the newly discovered campaign, GravityRAT can exfiltrate WhatsApp backups and receive commands to delete files,” ESET researcher Lukáš Štefanko said in a new report published today.
“The malicious apps also provide legitimate chat functionality based on the open-source OMEMO Instant Messenger app.”
GravityRAT is the name given to a cross-platform malware that’s capable of targeting Windows, Android, and macOS devices. The Slovak cybersecurity firm is tracking the activity under the name SpaceCobra.
The threat actor is suspected to be based in Pakistan, with recent attacks involving GravityRAT targeting military personnel in India and among the Pakistan Air Force by camouflaging it as cloud storage and entertainment apps, as disclosed by Meta last month.
The use of chat apps as a lure to distribute the malware was previously highlighted in November 2021 by Cyble, which analyzed a sample named “SoSafe Chat” that was uploaded to the VirusTotal database from India.
The chat apps, while not available on Google Play, are distributed through rogue websites promoting free messaging services: bingechat[.]net and chatico[.]co[.]uk.
“This group used fictitious personas — posing as recruiters for both legitimate and fake defense companies and governments, military personnel, journalists, and women looking to make a romantic connection — in an attempt to build trust with the people they targeted,” Meta said in its Quarterly Adversarial Threat Report.
The modus operandi suggests that potential targets are contacted on Facebook and Instagram with the goal of tricking them into clicking on the links and downloading the malicious apps.
GravityRAT, like most Android backdoors, requests for intrusive permissions under the garb of a seemingly legitimate app to harvest sensitive information such as contacts, SMSes, call logs, files, location data, and audio recordings without the victim’s knowledge.
The captured data is ultimately exfiltrated to a remote server under the threat actor’s control. It’s worth noting that using the app is conditional on having an account.
Discover the untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join our insightful webinar!
Learn, Connect, GrowWhat makes the new version of GravityRAT stand out is its ability to steal WhatsApp backup files and receive instructions from the command-and-control (C2) server to delete call logs, contact lists, and files with particular extensions.
“These are very specific commands that are not typically seen in Android malware,” Štefanko pointed out.
The development comes as Android users in Vietnam have been victimized by a new strain of banking cum stealer malware known as HelloTeacher that uses legitimate messaging apps like Viber or Kik as a cover to siphon sensitive data and carry out unauthorized fund transfers by abusing the accessibility services API.
Also discovered by Cyble is a cloud mining scam that “prompts users to download a malicious application to start mining,” only to take advantage of its permissions to the accessibility services to gather sensitive information from cryptocurrency wallets and banking apps.
The financial trojan, codenamed Roamer, exemplifies the trend of utilizing phishing websites and Telegram channels as distribution vectors, thereby effectively widening the potential victim pool.
“Users must exercise caution and refrain from following suspicious cryptocurrency mining channels on platforms like Telegram, as these channels can lead to substantial financial losses and compromise sensitive personal data,” Cyble said.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.