Warning issued over tampered QR codes
Avid readers of the Malwarebytes Labs blog are quite aware of QR code shenanigans—both within and outside of the United States.
Take, for example, that QR code scam in the Netherlands that victimized at least a dozen (and likely a lot more) car owners. It goes like this: Someone approaches you to let you know that they want to pay for parking but can’t find payment terminals that accept cash. They then ask you to kindly pay on their behalf—say, $5 USD—by scanning a QR code with their bank’s app after they hand you the money. Only, it isn’t just $5 USD that leaves your account.
Then, a few weeks ago, the Austin Police Department in Texas released a scam alert on Twitter about “pay-to-park” scams involving a QR code that directs users to a phish. We have covered this news in detail here.
Be extra vigilant when faced with a QR code
So it’s no wonder then that the FBI last week released a public service announcement about criminals using malicious Quick Response (QR) codes.
These codes that provide contactless access to a product or service have proven themselves useful and very convenient, especially with the pandemic still ongoing. But the problem is, it’s impossible to tell from the look of a QR code where it will take you, and whether it will be to a malicious destination or not.
“Cybercriminals tamper with both digital and physical QR codes to replace legitimate codes with malicious codes,” notes the FBI alert. “A victim scans what they think to be a legitimate code but the tampered code directs victims to a malicious site, which prompts them to enter login and financial information. Access to this victim information gives the cybercriminal the ability to potentially steal funds through victim accounts.”
QR codes can also be embedded with malware that, once scanned, can infect a device. Criminals are then given access to the now-affected device where they can do what they want. Depending on the malware, criminals could steal personal and financial information (if you bank using your smartphone) from you, make your device part of a botnet, or even spy on you.
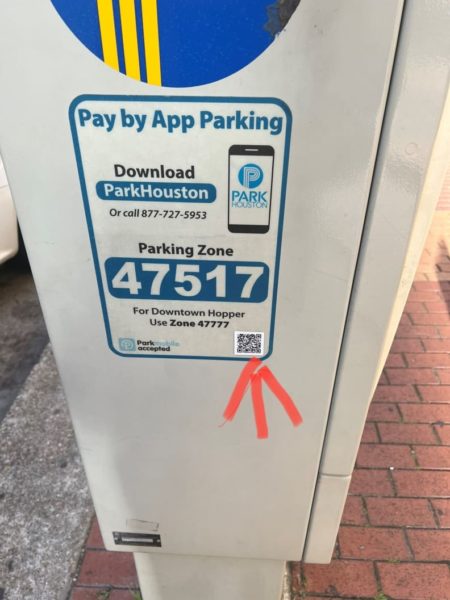
Criminals can also replace legitimate QR codes in establishments in order to mislead users and direct them to a potentially malicious site. In certain cases where a contactless way of paying is available but does not use QR codes, it would be easy for criminals to just add their QR code sticker and make users believe that they should scan it.
This is exactly what happened in the fraudulent “pay-to-park” scheme.
How to protect yourself from QR code scams
The FBI has recommended the following steps that users should keep in mind:
- Check the URL to ensure that you’re being directed to a site where you’re supposed to be directed once you scan a QR code. Watch out for misspellings in the URL.
- When you see a QR code in a shop and want to scan it, make sure you check for signs of tampering, such as a sticker over the QR code itself.
- Download an app from your go-to app store, not from a QR code.
- Use the built-in scanner through your smartphone’s camera to scan for QR codes. There is no need to download another one from the app store as there are fake QR code scanners, too.
- If you receive a QR code either through the mail or sent to you by a friend, get in touch with them first and verify if they have, indeed, sent you a QR code.
- If you can, avoid making payments via a QR code. There are better and more secure ways of paying.
Ideally, avoid making online transactions via a QR code. This poses a really high risk and must only be done if you really, really have no other option.
Stay safe!
The post Warning issued over tampered QR codes appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[QILIN] - Ransomware Victim: Sai Mai Hospital 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
