“We absolutely do not care about you”: Sugar ransomware targets individuals
Ransomware tends to target organizations. Corporations not only house a trove of valuable data they can’t function without, but they are also expected to cough up a considerable amount of ransom money in exchange for their encrypted files. And while corporations struggle to keep up with attacks, ransomware groups have left the average consumer relatively untouched—until now.
Sugar ransomware, a new strain recently discovered by the Walmart Security Team, is a ransomware-as-a-service (RaaS) that targets single computers and (likely) small businesses, too. Sugar, also known to many as Encoded01, has been in operation since November 2021.
Bleeping Computer notes that the Walmart Security Team got the name ‘Sugar’ from a site belonging to an affiliate of the ransomware operation: sugarpanel.space.
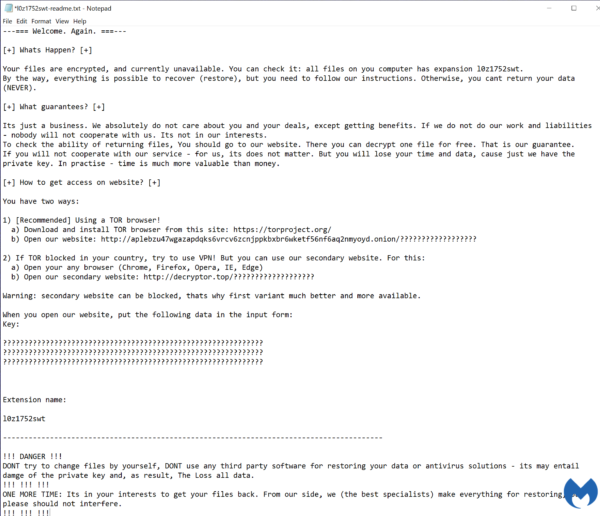
As with many ransomware strains, the authors aren’t holding back in their note which is dropped onto the system as BackFiles_encoded01.txt:
Whats Happen? [+]
Your files are encrypted, and currently unavailable. You can check it: all files on your system has extension .encoded01. By the way, everything is possible to recover (restore), but you need to follow our instructions. Otherwise, you cant return your data (NEVER).
[+] What guarantees? [+]
Its just a business. We absolutely do not care about you and your deals, except getting benefits. If we do not do our] work and liabilities - nobody will not cooperate with us. Its not in our interests. To check the ability of returning files, You should go to our website. There you can decrypt 1-5 files for free. That is our guarantee. If you will not cooperate with our service - for us, its does not matter. But you will lose your time and data, cause just we have the private key. In practise - time is much more valuable than money.
[+] How to get access on website? [+]
You can open our site by the shortcut "SUPPORT (TOR_BROWSER)" created on the desktop.
Also as the second option you can install the tor browser:
a) Download and install TOR browser from this site: https://torproject.org/
b) Open our website. Full link will be provided below.
----------------------------------------------------------------------------------------------
!!! DANGER !!!
DONT try to change files by yourself, DONT use any third party software for restoring your data or antivirus solutions- ints may entail damge of the private key and, as result, THE Loss all data.
!!! !!! !!!
ONE MORE TIME: Its in your interest to get your files back. From our side, we (the best specialists) make everything for restoring, but please should not interfere.
!!! !!! !!!
----------------------------------------------------------------------------------------------
Your ID:
{redacted}
How it works
Once executed, Sugar connects to two URLs, whatismyipaddress.com and ip2location.com, to identify the device’s IP address and geographic location. It then downloads a 76MB file, the use of which is currently unclear.
Sugar then connects to its command & control (C2) server where it transmits and receives data related to its attack. It then encrypts files located in the below folders:
- boot
- DRIVERS
- PerfLogs
- temp
- windows
However, it avoids the following files:
- .exe
- .dll
- .sys
- .lnk
- .bat
- .cmd
- .ttf
- .manifest
- .ttc
- .cat
- .msi;
- BOOTNXT
- bootmgr
- pagefile
The files are encrypted using the SCOP encryption algorithm, a stream cipher created in 1997 by Simeon Maltchev and Peter Antonov for Pentium processors but also runs very fast on other 32-bit processors. Furthermore, modifying SCOP to create a cipher optimized for 64-bit processors, which most machines run nowadays, is easy, according to Maltchev’s research. This modification will double the cipher’s speed.
Sugar is also called Encoded01 because this is the extension it appends to names of files it has encrypted. For example, after encoding a file called 1.jpg, the resulting filename is now 1.jpg.encoded01.
The ransomware note points victims at a Tor site which contains a page with the amount they have to pay in Bitcoin, a chat feature they can use to negotiate with the cybercriminals, and an offer to have five files decrypted for free.
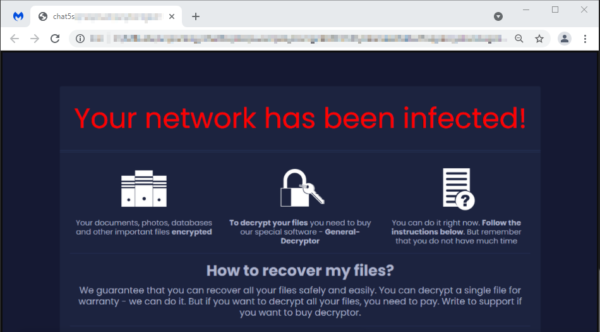
According to BleepingComputer, the ransom amount is automatically generated based on the number of files Sugar successfully encrypts. The amount tends to be relatively affordable, usually a few hundred dollars, making it more likely that people will stump up the cash for their files.
Borrowed content
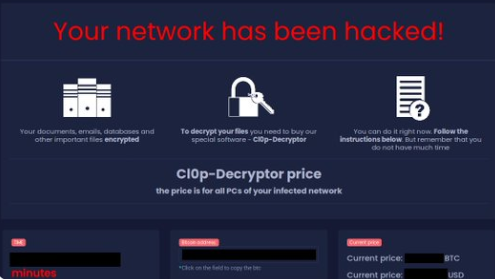
Several researchers have noted Sugar’s similarities with other ransomware families. The ransom note, for example, is reminiscent of REvil’s ransom note.
The Tor site the victim sees, on the other hand, is a lookalike of the page Cl0p used in its attacks.
How to protect yourself from ransomware
We don’t know yet how Sugar lands onto systems. So, as ever, we should continue to remain vigilant whatever we do online.
- Keep your system up to date. Cybercriminals take advantage of known vulnerabilities to infect computers. Make sure you apply patches as soon as they’re available, whether they’re for your operating system, your apps, or your browser.
- Back up your files. If you get infected with ransomware, you’re going to want to get hold of those backups. Make sure you back up offline to somewhere the attackers can’t reach.
- Don’t reuse your passwords, and make sure to choose strong ones for each account. Password managers can help with this.
- Be careful of unsolicited messages on social media, emails, online games, or anywhere else. Never click on a link sent in the message, and never enable macros in documents sent to you this way.
- Make sure all computers are protected with security protection. (Malwarebytes can help with this.)
Stay safe!
The post “We absolutely do not care about you”: Sugar ransomware targets individuals appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



