WebMonitor RAT Bundled with Zoom Installer

By Raphael Centeno, Mc Justine De Guzman, and Augusto Remillano II
The coronavirus pandemic has highlighted the usefulness of communication apps for work-from-home (WFH) setups. However, like they always do, cybercriminals are expected to exploit popular trends and user behavior. We have witnessed threats against several messaging apps including Zoom.
In early April, we spotted an attack leveraging Zoom installers to spread a cryptocurrency miner. We recently encountered a similar attack that drops a different malware: RevCode WebMonitor RAT (detected by Trend Micro as Backdoor.Win32.REVCODE.THDBABO).
Note that although the installers are legitimate, the ones bundled with malware do not come from official sources of the Zoom app like Zoom’s own download center or legitimate app stores such as the Apple App Store and Google Play Store. They instead come from malicious sources. We also note that the Zoom app has been updated to version 5.0.
Plenty of malware variants pose as legitimate applications to conceal their malicious intent. Zoom is not the only app used for this type of threat, as many other apps have been used for this attack as well. For this particular instance, cybercriminals may have repackaged the legitimate installers with WebMonitor RAT and released these repackaged installers in malicious sites.
Observations
The compromise starts with the user downloading the malicious file ZoomIntsaller.exe from malicious sources. Here, ZoomInstaller.exe refers to the file that contains the combination of a non-malicious Zoom installer and RevCode WebMonitor RAT.
When running the ZoomInstaller.exe, it drops a copy of itself named Zoom.exe. ZoomInstaller.exe will then open the process notepad.exe to run Zoom.exe.
The backdoor connects to the URL dabmaster[.]wm01[.]to and executes commands from a remote malicious user, some of which are listed below (for the full list, please refer to our malware report):
- Add, delete, and change files and registry information
- Close connections
- Get software and hardware information
- Get webcam drivers/snapshot
- Record audio and log keystrokes
- Start, suspend, and terminate processes and services
- Start/stop screen stream
- Start/stop Wireless Access Point
It also drops the file Zoom.vbs into the Windows User Startup folder to enable automatic execution at every system startup. However, these processes will not proceed if it detects processes connected to certain debugging or security tools:
- aswidagent.exe
- avastsvc.exe
- avastui.exe
- avgsvc.exe
- avgui.exe
- avp.exe
- bdagent.exe
- bdwtxag.exe
- dwengine.exe
- mpcmdrun.exe
- msmpeng.exe
- nissrv.exe
- ollydbg.exe
- procexp.exe
- procexp64.exe
- procmon.exe
- procmon64.exe
- windbg.exe
It terminates itself when executed in the following virtual environments:
- Kernel-based Virtual Machine
- Microsoft Hypervisor
- Parallels Hypervisor
- VirtualBox
- VMware
- Xen Virtual Machine Manager
It also terminates itself if it finds a file name similar to any of the following:
- Malware
- Sample
- Sandbox
Since the system downloaded a legitimate Zoom application version (4.6), it won’t make the users suspicious. However, the system has already been compromised at this point.
Initial observation of the sample shows Fareit-like behavior. However further inspection reveals that it is actually RevCode WebMonitor RAT, which certain groups were reportedly peddling in hacking forums back in mid-2017. The RAT allows threat actors to gain control of compromised devices and spy on them via keylogging, or web camera streaming, or screen captures. We found a YARA rule for this in this Twitter thread.
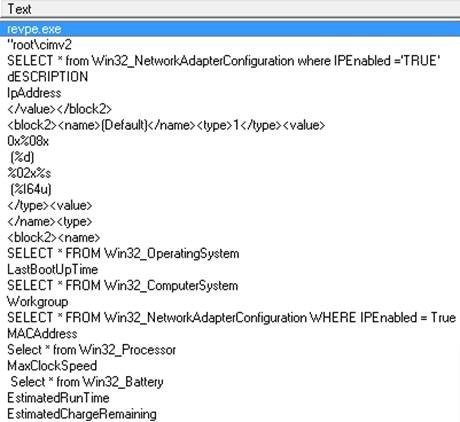
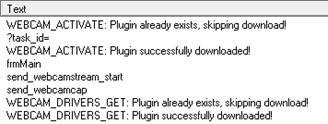
Figure 2. Snippets of the strings from the partially unpacked payload
The sample gathers the following information and sends them via HTTP POST to the URL hxxps://213.188.152.96/recv7[.]php
.{BLOCKED}.96/recv7.php:
- Battery Information
- Computer Information
- Desktop Monitor Information
- Memory Information
- Network Adapter Configuration
- OS Information
- Processor Information
- Video Controller Information
Recommendations
The Covid-19 pandemic and the ongoing home quarantine measures implemented in many countries has forced companies to adopt WFH arrangements that necessitates video conferencing apps. These apps can be secured by following these best practices:
- Only download installers from official sources, like the apps’ own download centers. Unofficial download sites are highly likely set up by cybercriminals to lure unwitting users.
- Secure video conferencing apps. Some of the ways to do this include putting in passwords for meetings, keeping meeting information private, using waiting rooms or lobbies, and configuring host controls.
- Always update the apps to the latest version. This addresses software vulnerabilities that attackers can exploit. For Zoom users: Zoom version 5.0 will be available soon.
To supplement these steps, the following security solutions are recommended:
- Trend Micro Apex One
 – offers advanced automated threat detection and response against an ever-growing variety of threats.
– offers advanced automated threat detection and response against an ever-growing variety of threats. - Trend Micro XDR – Applies artificial intelligence and analytics to the deep data sets collected from Trend Micro solutions across the enterprise, leading to early and better detection.
A multilayered protection approach is also recommended to proactively detect and block known and new threats from all possible points of entry.
Indicators of Compromise
URLs
- dabmaster[.]wm01[.]to
- hxxps://213.188.152.96/recv7[.]php
| SHA-256 | Trend Micro Pattern Detection |
| 753418831fcf215fe2d00ed33b9d2f1ed78bc92355e780c782fb35228007318e | Backdoor.Win32.REVCODE.THDBABO |
The post WebMonitor RAT Bundled with Zoom Installer appeared first on .

 – offers advanced automated threat detection and response against an ever-growing variety of threats.
– offers advanced automated threat detection and response against an ever-growing variety of threats.