Windows Installer vulnerability becomes actively exploited zero-day
Sometimes the ways in which malicious code gets in the hands of cybercriminals is frustrating for those in the industry, and incomprehensible to those on the outside.
A quick summary of the events in the history of this exploit:
- A researcher found a flaw in Windows Installer that would allow an attacker to delete targeted files on an affected system with elevated privileges.
- Microsoft patched the vulnerability in November’s Patch Tuesday update.
- The researcher found a way to circumvent the patch and this time decided not to engage in responsible disclosure because he got frustrated with Microsoft’s bug bounty program.
- The researcher’s PoC is being tested in the wild and cybercriminals could be preparing the first real attacks exploiting this vulnerability.
Let’s have a look at what is going on and how it came to this.
The vulnerability
Publicly disclosed computer security flaws are listed in the Common Vulnerabilities and Exposures (CVE) database. Its goal is to make it easier to share data across separate vulnerability capabilities (tools, databases, and services).
The vulnerability in question was listed as CVE-2021-41379 and is a local Windows Installer Elevation of Privilege (EoP) vulnerability. If successfully exploited, the bypass could give attackers SYSTEM privileges on up-to-date devices running the latest Windows releases, including Windows 10, Windows 11, and Windows Server 2022.
By exploiting this zero-day, threat actors that already have limited access to compromised systems can elevate their privileges and use these privileges to spread laterally within a target network.
The patch
Microsoft patched the vulnerability in the November Patch Tuesday updates. But according to the researcher, the bug was not fixed correctly. He discovered a new variant during the analysis of the CVE-2021-41379 patch.
With the new variant, an attacker will be able to run programs with a higher privilege than they are entitled to. To be clear, an attacker using the new variant must already have access and the ability to run code on a target victim’s machine, but now they can run the code with SYSTEM privileges thanks to the exploit.
The frustration
The researcher appears to have been so disappointed in Microsoft after he responsibly disclosed the vulnerability by means of the Trend Micro zero-day initiative, that he decided to skip that path altogether when he found the new method to bypass the patch. The researcher published a new version of the proof of concept (PoC) exploit, which is even more powerful than the original exploit.
Apparently the main reason for his frustration was the reward level.
““Microsoft’s rewards have been very bad since April 2020; the community wouldn’t make these kinds of decisions if Microsoft took its rewards seriously.”
In the wild
Several security vendors have noticed malware samples in the wild that are attempting to take advantage of this vulnerability. A quick search on VirusTotal showed dozens of different files that tried to do this. This may be some threat actors testing the exploit code to turn it into something they can use in their attacks, along with some researchers trying out different ways to use and stop the exploit. It is worrying nonetheless to see once again how quick attackers are able to weaponize publicly available exploit code.
Mitigation
The researcher recommends users wait for Microsoft to release a security patch, due to the complexity of this vulnerability, although he doesn’t seem confident that Microsoft will get it right this time.
“Any attempt to patch the binary directly will break windows installer. So you better wait and see how Microsoft will screw the patch again.”
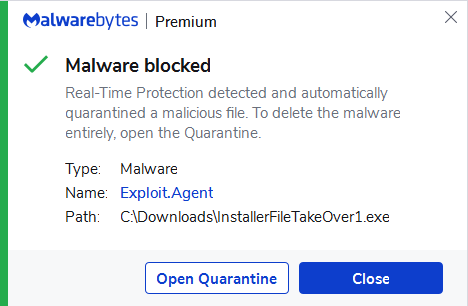
Microsoft says it is working on it. In the meantime, Malwarebytes Premium and business users are protected, because our programs detect the files using this vulnerability as Exploit.Agent.
Stay safe, everyone!
The post Windows Installer vulnerability becomes actively exploited zero-day appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


